Cybersecurity analysts have uncovered a sophisticated campaign exploiting a fake Zoom installer to deliver BlackSuit ransomware across Windows-based systems.
The attack, documented by DFIR experts, highlights how threat actors are leveraging popular software to deceive unsuspecting victims into installing malware capable of crippling entire networks.
The Fake Zoom Installer
The malicious activity began with a website mimicking Zoom’s legitimate domain, enticing users to download a file named “Zoom_v_2.00.4.exe.”
![Initial Malicious Zoom via zoommanager[.]com](https://gbhackers.com/wp-content/uploads/2025/03/image-89.png)
This website, cleverly crafted to resemble the legitimate Zoom interface, fooled users into believing they were downloading the popular teleconferencing software.
Behind the scenes, however, the installer functioned as a delivery mechanism for a multi-stage malware attack chain.
The fake installer was built using Inno Setup—a legitimate installer creation tool. Its payload included “d3f@ckloader,” a sophisticated downloader designed in Pascal scripting language.
Upon execution, the malicious code leveraged multiple stages to bypass security, install additional payloads, and execute nefarious activities.
The Multi-Stage Attack Chain
Stage 1: Initial Access and Defense Evasion
After downloading the fake installer, victims unknowingly executed a series of batch scripts that:
- Disabled Windows Defender by adding malicious directories to exclusion lists.
- Downloaded additional payloads from remote sources, including Steam Community pages and Pastebin, to initiate the malware chain.
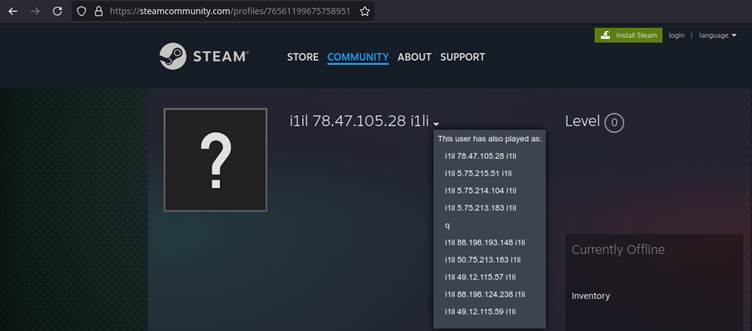
Stage 2: Malware Deployment
The fake installer simultaneously deployed two executables:
- A legitimate Zoom installer to reduce suspicion.
- IDAT loader that eventually injected SectopRAT, a malicious remote access trojan (RAT), into the “MSBuild.exe” process.
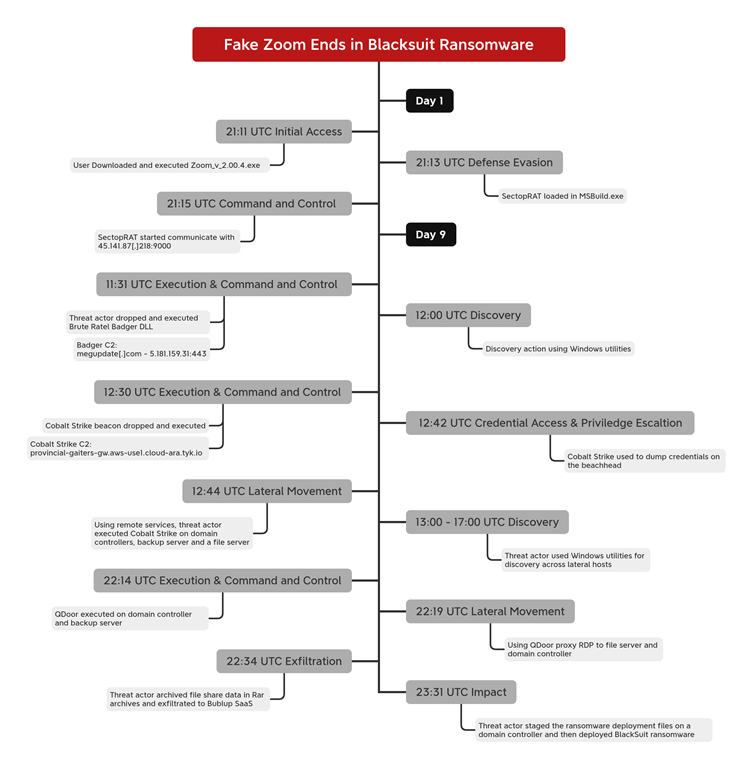
For nine days, the SectopRAT trojan remained dormant, enabling the threat actor to avoid detection while gathering intelligence.
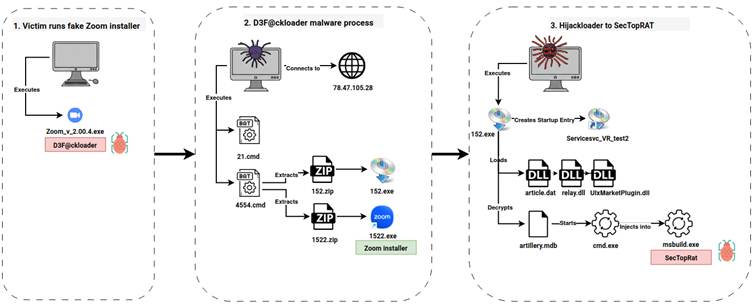
On the ninth day, it activated additional payloads, including Brute Ratel, and later deployed the widely recognized Cobalt Strike post-exploitation toolkit.
Lateral Movement and Data Theft
Using tools like QDoor malware and RDP (Remote Desktop Protocol), the attacker achieved lateral movement across the compromised environment.
Sophisticated proxies enabled secure tunneling of commands and data between infected systems, ensuring continued control over the network.
Once access to sensitive file servers and domain controllers was achieved, the attacker used WinRAR to compress files and exfiltrated them to a SaaS application called Bublup.
Deployment of BlackSuit Ransomware
In the final stage, the attacker executed BlackSuit ransomware—an advanced strain capable of encrypting files and rendering systems inoperable.
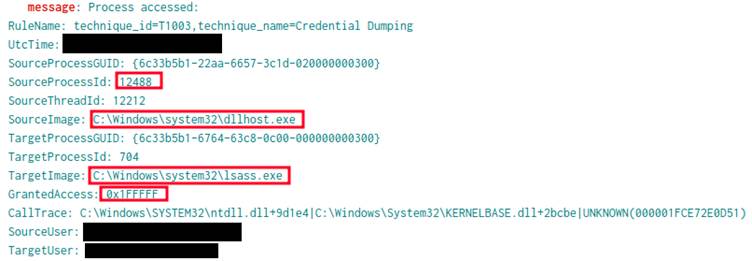
Using the PsExec utility, the ransomware was deployed across multiple remote systems. Once executed, BlackSuit:
- Deleted shadow copies to prevent recovery.
- Encrypted all files, locking users out of their data.
- Dropped ransom notes, demanding payment in exchange for decryption.
The entire operation, from initial access to ransomware deployment, took approximately nine days.
How to Protect Yourself
This campaign underscores the critical importance of vigilance when downloading software, especially from unofficial sources. Here are actionable steps for defense:
- Download software only from verified sources—always double-check website URLs to ensure legitimacy.
- Enable advanced malware detection tools that can identify multi-stage attacks like BlackSuit ransomware.
- Regularly update your security protocols and train employees to recognize phishing attempts and suspicious downloads.
- Maintain backups of sensitive data and implement offline storage solutions to safeguard against ransomware.
- Monitor network traffic for unusual communication patterns (e.g., connections to external IPs or platforms like Telegram and Steam).
The discovery of this campaign serves as a sobering reminder that threat actors are becoming increasingly innovative in their attack strategies.
By exploiting the global popularity of software like Zoom, they have created a trap capable of paralyzing organizations and extorting significant financial gains.
Security teams must be proactive and responsive to protect systems against such evolving threats. Awareness, vigilance, and robust cybersecurity measures remain the best defense against becoming the next victim of ransomware attacks like BlackSuit.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!



.png
)
