Cloudflare has announced the implementation of post-quantum cryptography across its services.
This advancement is part of a broader effort to protect customers from potential quantum attacks that could compromise conventional cryptographic systems in the future.
Quantum computers, which are rapidly becoming more powerful, pose a significant threat to the cryptographic algorithms currently used to secure online communications.
Conventional cryptography, such as RSA and Elliptic Curve Cryptography (ECC), forms the backbone of Internet security today but is vulnerable to attacks by advanced quantum computers.
This vulnerability is not merely theoretical; recent breakthroughs in quantum computing have made it clear that the transition to post-quantum cryptography must begin now.
The National Institute of Standards and Technology (NIST) has also recognized the urgency of this transition, announcing plans to phase out RSA and ECC by 2030 and disallow them entirely by 2035.
However, Cloudflare is not waiting; the company has been at the forefront of developing and implementing post-quantum cryptography since 2017, understanding that privacy and advanced security should be accessible to all without additional cost.
Cloudflare’s Post-Quantum Cryptography
Cloudflare’s Zero Trust platform is now enhanced with post-quantum cryptography, allowing organizations to secure their corporate network traffic without the need to individually upgrade each application or system.
This includes key use cases like clientless Zero Trust Network Access (ZTNA), the WARP device client, and Cloudflare Gateway.
Key Features:
- Clientless Access: Cloudflare’s clientless ZTNA solution verifies user identity and device context for every HTTPS request, providing end-to-end quantum safety for accessing corporate applications through web browsers.
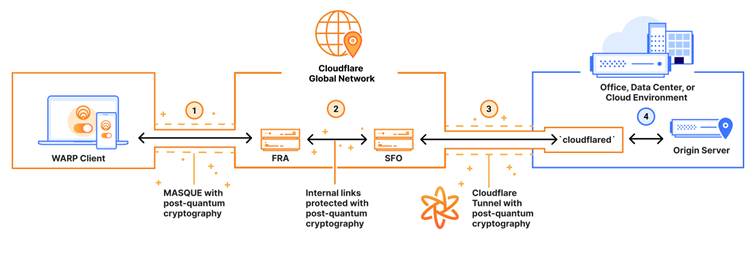
- WARP Device Client: By mid-2025, customers using the WARP client will enjoy all their traffic tunneled over a connection protected by post-quantum cryptography, replacing traditional VPNs and offering quantum safety for any protocol.
- Secure Web Gateway (SWG): Cloudflare Gateway now supports TLS with post-quantum cryptography, ensuring secure access to third-party websites and inspecting TLS traffic effectively.
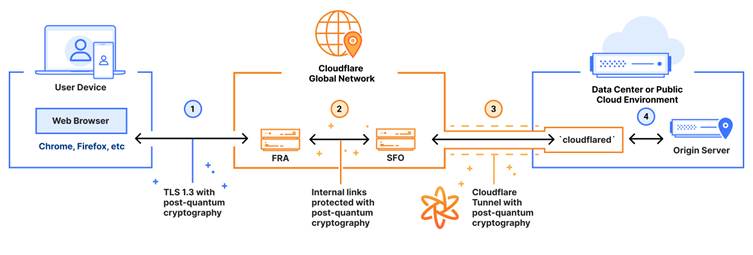
Migrating to Post-Quantum Cryptography
The transition to post-quantum cryptography involves two main phases: migrating key agreement protocols and updating digital signatures.
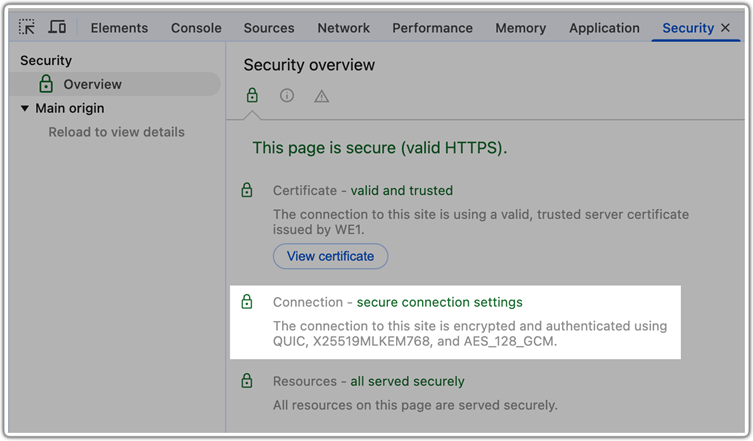
- Key Agreement: Cloudflare has focused on transitioning TLS 1.3 to support ML-KEM (Module-lattice based Key-Encapsulation Mechanism Standard), a post-quantum key exchange protocol. This is crucial for securing against “harvest now, decrypt later” threats, where encrypted data is stored with the intent of decrypting it once quantum technology advances.
- Digital Signatures: While post-quantum digital signatures are essential for authenticating connections, their larger size and slower performance have slowed adoption. Cloudflare is actively involved in standardizing these signatures for future use.
Why Adopt Post-Quantum Cryptography Now?
The transition to post-quantum cryptography is necessary for two primary reasons:
- Crypto-Agility Challenges: Updating cryptographic systems is notoriously difficult. For instance, despite being deemed insecure, the MD5 hash function was still in use until recently. Starting early helps mitigate these challenges.
- “Harvest Now, Decrypt Later” Threats: Even though current quantum computers cannot break conventional cryptography, adversaries can harvest encrypted data now and decrypt it later when quantum technology advances. Protecting data today prevents potential future liabilities.
Cloudflare’s adoption of post-quantum cryptography marks a significant step in ensuring the future security of digital communications.
As quantum computing evolves, the need for robust protections will only grow.
By providing immediate access to quantum-safe connections, Cloudflare empowers organizations to safeguard their data and applications against emerging threats without the burden of individually upgrading every system.
Whether through cloud-based applications or traditional network infrastructure, Cloudflare’s commitment to crypto-agility and post-quantum security leads the way in future-proofing cybersecurity for businesses and users alike.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
