Cloudflare, a leading web infrastructure and security company, has launched the Cloudforce One threat events platform, designed to revolutionize how security professionals detect and analyze indicators of compromise (IOCs), including IP addresses, domains, and other critical metadata.
The proliferation of threat intelligence feeds has become a cornerstone for cybersecurity strategies, but these feeds often fall short in providing the necessary context.
Most indicator feeds focus solely on blockable indicators such as IP addresses, ASNs, and domains, without delving into the complexities of threats, such as exploits of vulnerabilities or insider threats.
These nuanced threats are typically covered in long-form reports, which can suffer from delays in publication due to the extensive time required for research and editing.
Introduction of Cloudforce One
Cloudflare’s Cloudforce One platform is poised to bridge this gap by offering a more comprehensive and real-time view of threat activity across the internet.
Every day, Cloudflare processes billions of transactions, handling an average of 71 million HTTP requests per second and 44 million DNS queries per second. This immense traffic volume provides Cloudflare with unparalleled insights into current and emerging threats.
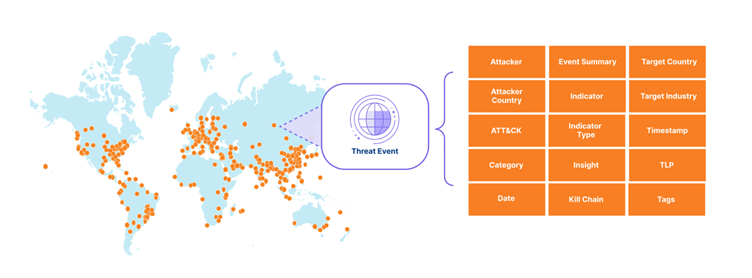
The Cloudforce One platform curates threat activity into actionable events that include context beyond just indicators of compromise.
These events encompass denial-of-service (DoS) attacks, advanced threat operations, and are mapped to frameworks like the MITRE ATT&CK matrix and the cyber kill chain stages.
In the future, the platform will expand to include data from Cloudflare’s Web Application Firewall, Zero Trust Gateway, and more, offering a detailed view of internet-wide threat activity.
How the Platform Works
The Cloudforce One platform is built using Cloudflare Workers, a versatile tool that allows seamless integration with the Cloudflare network. The platform utilizes Durable Objects with SQLite for storing and managing datasets.
This approach enables dynamic creation of SQL tables, ensuring scalability and flexibility in handling large volumes of threat data. It also allows for controlled sharing of datasets with trusted partners or restricting access to authorized users.
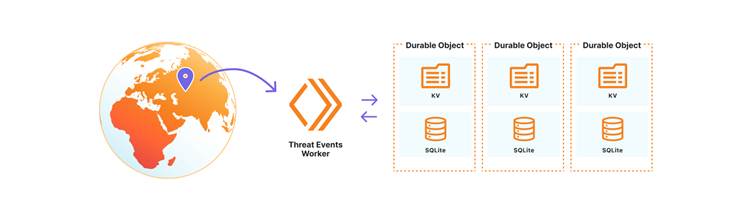
Each threat event contains a unique identifier, linking it to specific threat activity for further analysis by Cloudflare’s threat intelligence team.
The metadata for each event is stored in Durable Object KV, allowing for the storage of additional contextual data that can help in investigations.
Accessing Threat Events
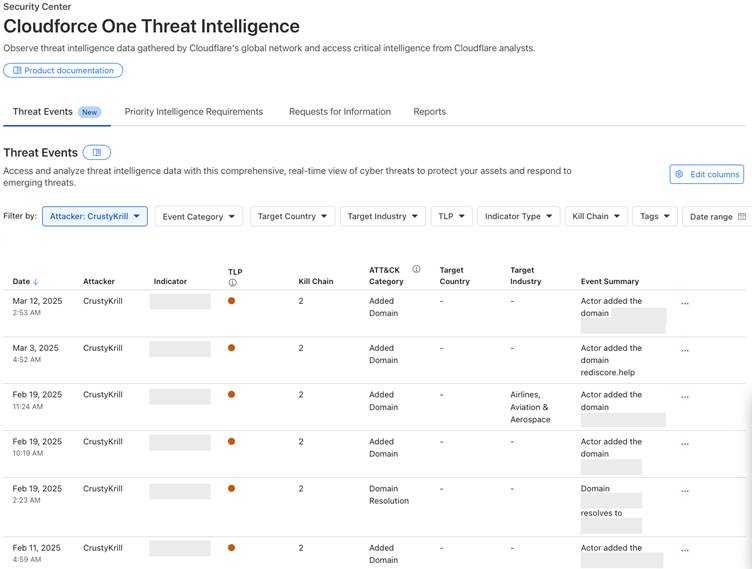
Cloudforce One customers can access threat events through the Cloudflare Dashboard’s Security Center or via the Cloudforce One API.
Both methods provide customizable streams of threat activity, allowing users to filter events based on various criteria.
The dashboard offers an Attacker Timelapse view for strategic insights, alongside a granular events table for detailed drill-downs.
Real-World Application
To demonstrate the platform’s capabilities, Cloudflare highlighted its use in analyzing the Black Basta criminal enterprise.
Leaked chats from Black Basta revealed details about their operations and infrastructure.
Cloudflare integrated this information into the threat events platform, providing users with actionable insights into the group’s activities, such as verified IP addresses and domains.
Future Developments
Cloudflare is committed to enhancing the threat events platform with additional features. Future updates will include more advanced visualizations and analytics tools, such as detailed attacker timelines and campaign overviews.
These enhancements will enable deeper insights into threats and facilitate better reporting and decision-making.
The platform is also set to integrate with existing Security Information and Event Management (SIEM) systems and enable the sharing of indicators across different systems, further empowering organizations to bolster their cybersecurity posture.
In a recent validation exercise, a Fortune 20 threat intelligence team ranked Cloudflare’s threat events as the top threat intelligence source among over 110 alternatives, underscoring the platform’s unique value in the cybersecurity landscape.
With the launch of Cloudforce One, Cloudflare is transforming how cybersecurity professionals approach threat detection and analysis.
By providing real-time, contextualized insights into IOCs, IPs, domains, and other complex threats, Cloudflare is equipping organizations with the tools they need to stay ahead of rapidly evolving cybersecurity challenges.
As cyber threats continue to grow in sophistication, platforms like Cloudforce One are crucial for ensuring timely and effective cybersecurity strategies.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
