Cloudflare has contributed to the open-sourcing of OPKSSH, a tool that integrates single sign-on (SSO) technologies like OpenID Connect (OIDC) into SSH protocols.
This integration simplifies SSH access by leveraging OpenPubkey, which embeds public keys into the SSO tokens issued by identity providers (IdPs).
The main beneficiaries of this innovation are organizations that struggle with managing and securing long-lived SSH keys.
Background and Challenges in SSH Key Management
SSH (Secure Shell) is a widely used protocol for secure access and management of remote servers.
Traditional SSH access involves generating a pair of long-lived public and private keys, where the public key needs to be configured on each server the user accesses.
This approach poses several challenges:
- Security Risks: Long-lived SSH keys can become compromised if not managed properly. Users often copy private keys to multiple devices, increasing the risk of unauthorized access.
- Usability Issues: Users must securely store their private keys and manually update public keys on servers when access needs to be revoked or updated.
- Visibility and Compliance: Tracking who has access to servers can be cumbersome, as administrators need to manage lists of public keys rather than identities.
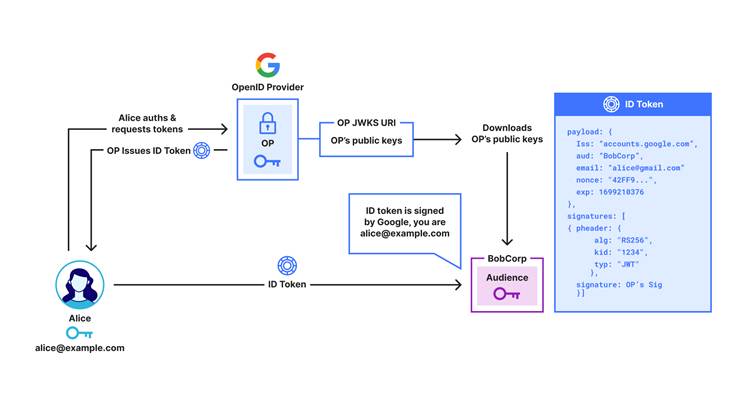
How OpenPubkey and OPKSSH Solve These Challenges
OpenPubkey is an extension of OpenID Connect, a widely adopted SSO protocol. It embeds public keys into the ID Tokens (PK Tokens), which are issued by an OpenID Provider (OP).
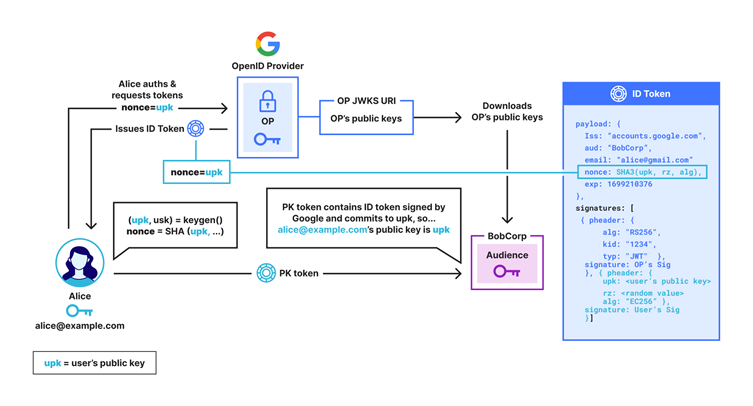
This allows these tokens to be used similarly to certificates, connecting a user’s identity with a specific public key.
OPKSSH expands this capability by enabling the use of these PK Tokens as SSH keys, thereby integrating SSO directly into SSH protocols without requiring changes to the underlying SSH infrastructure.
Here’s how it improves upon traditional SSH key management:
- Improved Security: OPKSSH generates ephemeral SSH keys that are created on-demand and expire after a certain period, typically 24 hours by default. This reduces the risk of key compromise and limits the window of exposure if a private key is stolen.
- Enhanced Usability: Users can access SSH-enabled servers simply by logging in through their SSO provider, similar to other SSO-enabled services. This eliminates the need to manually manage or copy SSH private keys across devices.
- Better Visibility: Access control moves from public keys to user identities. Administrators can manage access by email addresses rather than public keys, making it easier to track who has access to servers and ensuring compliance.
How OPKSSH Works
To use OPKSSH, a user runs the opkssh login command, which generates ephemeral SSH keys and prompts the user to authenticate through their OpenID Provider.
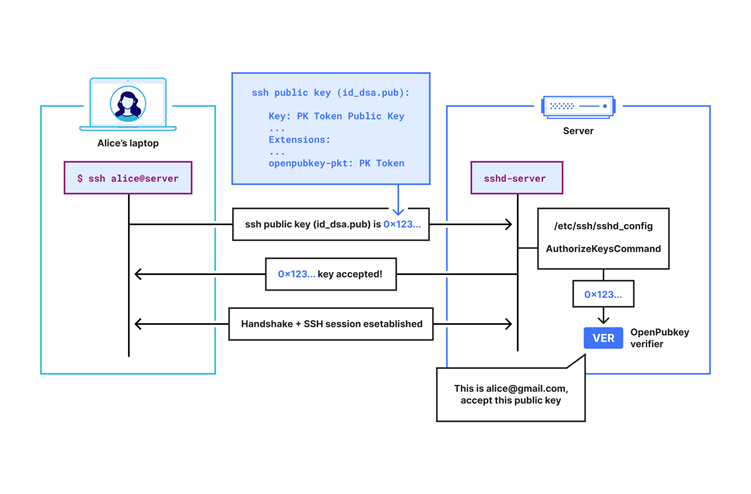
Upon successful authentication, OPKSSH creates a PK Token that links the user’s identity with their ephemeral public key.
This information is packaged into an SSH certificate extension and transmitted to the server during the SSH connection process.
On the server side, the SSH configuration is updated to use the OpenPubkey verifier instead of the standard SSH key checker.
This verifier checks the validity and expiration of the received PK Token, ensuring that the public key presented matches the one in the token and that the user is authorized to access the server.
The open-sourcing of OPKSSH represents a significant leap forward in streamlining SSH access while bolstering security.
By leveraging existing single sign-on infrastructure, organizations can eliminate the complexities of managing long-lived SSH keys, enhancing both user experience and security posture.
Cloudflare’s integration not only modernizes SSH security but also aligns well with broader trends in identity-driven access management.
With OPKSSH now available under the Apache 2.0 license on GitHub, developers and administrators can explore and implement this feature-rich tool to simplify SSH management in their environments.
The potential benefits extend beyond security; they also enhance operational efficiency and user convenience, which are critical factors in today’s fast-paced and security-conscious digital landscape.
Are you from SOC/DFIR Teams? – Analyse Malware, Phishing Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
