Cloudflare has unveiled AI Labyrinth, an innovative platform designed to combat AI-powered bots that relentlessly crawl and scrape data from websites without permission.
By employing AI-generated content, AI Labyrinth cleverly slows down and misdirects these bots, safeguarding legitimate websites while enhancing bot detection capabilities.
What is AI Labyrinth?
AI Labyrinth is a proactive defense mechanism that deploys an AI-generated series of linked web pages when unauthorized crawling activity is detected.
This system operates without requiring users to create custom rules, making it accessible to all Cloudflare customers, including those on the free plan.
By enticing bots into traversing these AI-created pages, AI Labyrinth efficiently diverts resources away from valuable site data, rendering the bots less effective at gathering information for training AI models.
Generative AI has become increasingly prevalent across platforms, with an estimated 47% of Medium content reportedly AI-generated.
While this technology offers numerous benefits, it also facilitates malicious activities such as AI-driven data scraping.
Cloudflare has utilized this trend to its advantage by employing AI-generated content as a defensive strategy.
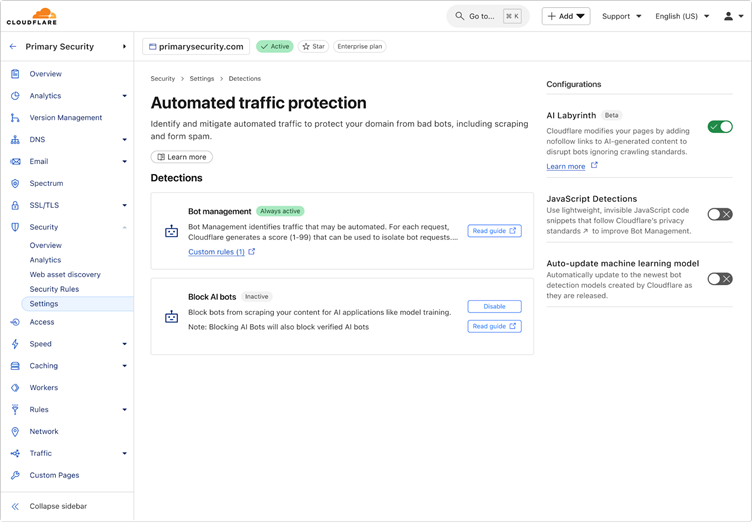
When detected, unauthorized crawlers are directed to convincing yet irrelevant AI-generated content, which appears authentic enough to deceive bots but lacks any real value, thereby wasting their resources.
Building the Labyrinth
To generate this convincing content, Cloudflare leverages Workers AI and an open-source model to produce unique HTML pages on various scientific topics.
The content is pre-generated and stored in Cloudflare’s R2 data storage, ensuring it is sanitized for security and can be quickly accessed when needed.
This approach ensures that generated content does not spread misinformation but remains factual and irrelevant to the site being crawled.
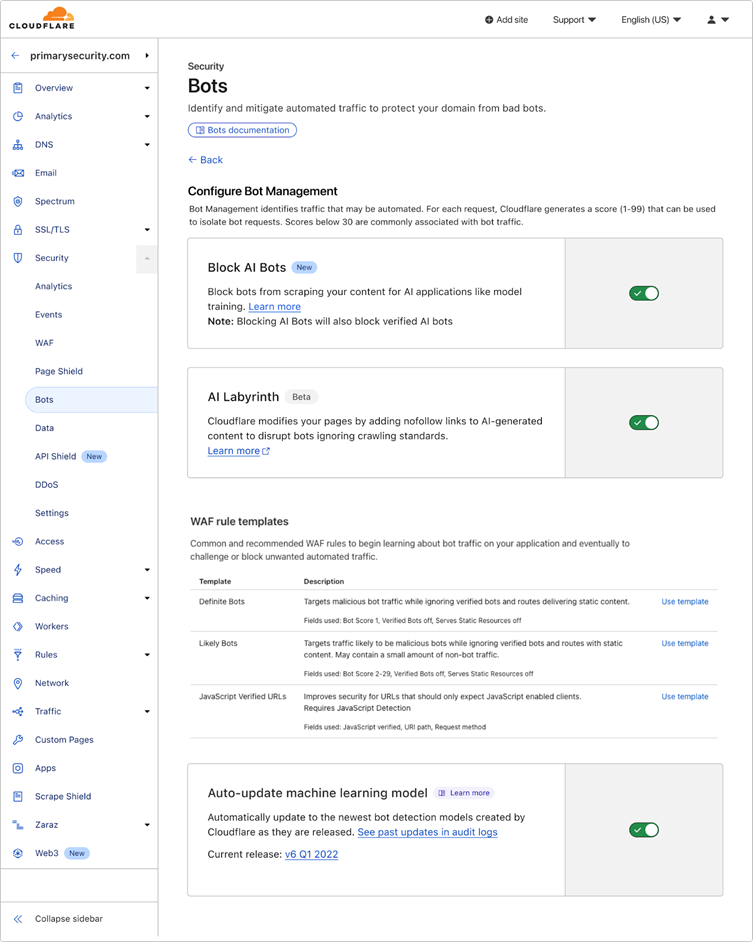
These AI-generated pages are seamlessly integrated into existing websites through hidden links that remain invisible to human visitors.
AI Labyrinth serves as a sophisticated honeypot, enabling Cloudflare to identify and fingerprint malicious bots with high precision.
When bots follow these hidden links, the system confidently identifies them as automated traffic, providing invaluable data that enhances its machine-learning models.
This ongoing process helps refine the system’s detection capabilities, ensuring it remains a step ahead of evolving AI scrapers.
Benefits and Accessibility
Enabling AI Labyrinth in the Cloudflare dashboard is straightforward and requires only a simple toggle.
Once activated, the system begins working without additional setup, ensuring minimal disruption to normal website operations.
By leveraging AI-generated content as a defensive tool, Cloudflare offers an innovative solution that not only thwarts AI crawlers but also contributes to improving the overall security landscape for its users.
This initial rollout of AI Labyrinth marks just the beginning of Cloudflare’s exploration into using AI to combat malicious web activity.
Future iterations will focus on making the AI-generated content even more indistinguishable from actual website content, seamlessly integrating it into existing structures without impacting user experience.
Users are encouraged to participate by opting into AI Labyrinth to aid in its development and help protect a broader community of Cloudflare customers.
Cloudflare’s AI Labyrinth offers a powerful and pioneering approach to mitigating AI-driven threats on the web, showcasing how generative AI can be harnessed to enhance cybersecurity.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
