Security researchers from Palo Alto Networks discovered new six vulnerabilities with D-Link wireless home router let attackers launch remote attacks.
The vulnerabilities found with the DIR-865L model of D-Link routers, those are mostly used in home-based environments. In the current situation as we are working from home these vulnerabilities may pose serious threats.
Researchers absorbed six such vulnerabilities with the newer models of the firmware. Combining vulnerabilities can lead to significant risks.
CVE-2020-13782
The vulnerabilities reside in the controller of the web interface of the router, an attacker with authentication, or by having an active session cookie can inject an arbitrary code to execute in administrative privileges.
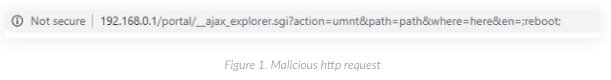
CVE-2020-13786
Multiple webpages of router web interface vulnerable to CSRF. It allows an attacker to sniff the web traffic and to gain access to password-protected pages of the web interface.
CVE-2020-13785
Data transferred with the SharePort Web Access portal on port 8181 are not encrypted, it allows an attacker to determine the password.

CVE-2020-13784
The session cookie generation is predictable, an attacker can determine the session cookie by just knowing the user login time.
CVE-2020-13783
The login credentials are stored in plain text, an attacker must have physical access to steal the passwords.
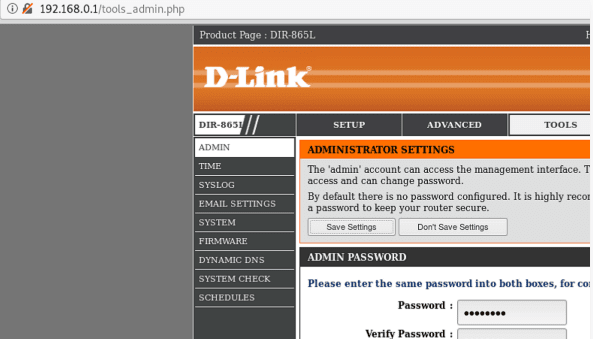
CVE-2020-13787
If the administrator selects Wired Equivalent Privacy (WEP) which was deprecated in 2004 for guest wifi network then passwords will be sent cleartext.
Combining all these vulnerabilities allow attackers to run arbitrary commands, exfiltrate data, upload malware, delete data, or steal user credentials, reads Paloalto blog post.
D-Link fixed the vulnerabilities with the router, users are recommended to update with the latest firmware to patch the vulnerabilities.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.
Also Read
Hackers Hijacking DLink Routers to Gain Bank Credentials By Using Various Router Exploits
New DNS Hijacking Attack Exploiting DLink Routers to Target Netflix, PayPal, Uber, Gmail Users



.png
)
