Google releases a new announcement for Android users to authenticate the web-based google services in chrome for Android using a fingerprint instead of traditional password-based authentication and the feature called FIDO2-based local user verification for Google Accounts.
A password-based authentication protects billion of Android users but now its surpassed by the fingerprint-based authentication which is now available for on Pixel devices and the feature rolling out for Android 7+ devices and reach to users within next few days.
This new feature will increase the security from password-based attacks such as phishing on the web and reduce the burden from keep on remembering the passwords.
In order to provide high-level secure authentication for Google users, the new fingerprint-based authentication implemented using the FIDO2 standards, W3C WebAuthn, and FIDO CTAP.
This is the first time fingerprint-based authentication available on the web and it required to register the users at only once and then use the same Fingerprint authentication for both web service and native apps that installed in users Android phone.

Here the FIDO2 is playing a major role and the fundamental part of the FIDO2 design let never share your fingerprint to Google servers instead of that it only shares the correctly scanned cryptographic proof.
Fingerprints Authentication Working Mechanism
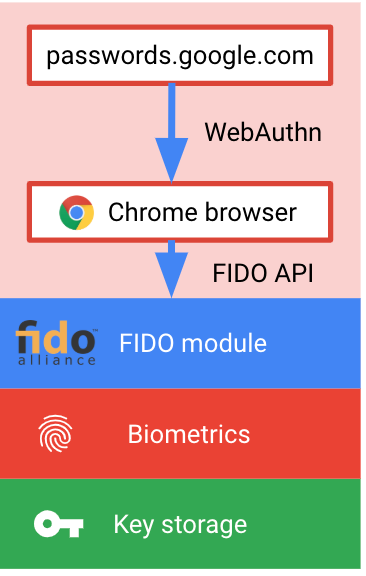
When the users accessing Google services such as Passwords.google.com, First it issues the WebAuthn, a core component of the FIDO2 Project that helps to authenticate the users to web-based applications.
FIDO2 Project is a joint effort between the FIDO Alliance and the World Wide Web Consortium (W3C) whose goal is to create a strong authentication solution for the web.
According to Google. ” Now, when the user visits a compatible service, such as passwords.google.com, we issue a WebAuthn “Get” call, passing in the credentialId that we got when creating the credential. The result is a valid FIDO2 signature. “
Now you can experience this new feature in passwords.google.com, a Google web service to access your saved password for update and edit, follow these steps.
- Open the Chrome app on your Android device
- Navigate to https://passwords.google.com
- Choose a site to view or manage a saved password
- If you tap on any one of these saved passwords, then Google will prompt you to “Verify that it’s you,”
- At this pointYou can use the Fingerprint that you have already set up for unlocking your android
Google also advised to protecting your accounts with two-step verification (2SV), including Titan Security Keys and Android phone’s built-in security key to protect from attackers who continuously attempt to break your password.
Sponsored: – Manage all the Endpoint networks from a single Console.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.



.png
)
