A chilling new development in the cybersecurity landscape has emerged, as a threat actor has reportedly advertised an alleged zero-day exploit targeting Fortinet’s FortiGate firewalls on a prominent dark web forum.
This exploit purportedly enables unauthenticated remote code execution (RCE) and full configuration access to FortiOS, unlocking the potential for attackers to seize control of vulnerable devices without credentials.
This discovery has set off alarm bells, given Fortinet’s widespread use in enterprises and government agencies globally.
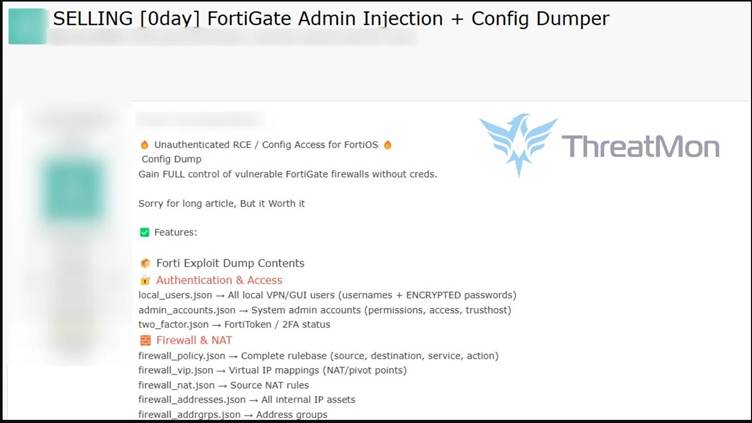
The claimed zero-day exploit, observed by cybersecurity firm ThreatMon, boasts the ability to extract sensitive configuration files from compromised devices, offering access to critical data such as:
- Local user credentials: Encrypted passwords stored in local_users.json.
- Admin account details: Permissions and trust relationships documented in admin_accounts.json.
- Two-factor authentication (2FA) status: Details on FortiToken configurations from two_factor.json.
- Firewall policies and network configurations: Rule sets, NAT mappings, and internal IP asset details.
The implications are severe. Such information could allow attackers to bypass security measures, infiltrate networks, and potentially launch secondary attacks.
This exploit appears to target FortiOS versions potentially affected by authentication bypass vulnerabilities—a persistent issue in Fortinet’s products.
Historical Context of Fortinet Vulnerabilities
Fortinet has faced its share of challenges with security vulnerabilities in recent years.
Earlier this year, the Belsen Group—a newly identified hacking entity—leaked configuration files for over 15,000 FortiGate firewalls, exploiting CVE-2022-40684, an authentication bypass vulnerability disclosed in 2022.
Despite being over two years old, this vulnerability continued to impact systems with outdated configurations.
More recently, Fortinet disclosed another critical vulnerability, CVE-2024-55591, which allowed attackers to gain super-admin privileges through crafted requests.
Affecting FortiOS and FortiProxy versions, this flaw underscored a troubling pattern of exploitation surrounding Fortinet products.
Potential Risks and Mitigation
The advertised zero-day exploit poses several risks to organizations:
- Unauthorized Access: Attackers can gain administrative control over devices, modify configurations, and steal sensitive data.
- Network Compromise: Firewalls may serve as entry points for lateral movement within networks.
- Data Breaches: Leaked credentials and configuration files increase the risk of confidential information exposure.
- Operational Disruption: Altered firewall policies could disrupt normal network operations or create future vulnerabilities.
With over 300,000 potentially vulnerable Fortinet firewalls in use worldwide, the scope of possible damage is daunting.
Fortinet has urged users to promptly apply patches, monitor network traffic, implement strict access controls, and conduct regular audits of firewall configurations.
This zero-day exploit highlights the growing sophistication of cyber threats and the persistent vulnerabilities within even trusted security products.
As attackers continue targeting widely-used enterprise solutions, organizations must prioritize robust cybersecurity measures—including proactive updates, traffic monitoring, and comprehensive access controls—to stay one step ahead of evolving cyber risks.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
