The education and publishing giant Scholastic has fallen victim to a significant data breach affecting approximately 8 million people.
The breach, which has been attributed to a self-proclaimed “furry” hacker going by the alias “Parasocial,” was first reported by the Daily Dot.
Scholastic is a household name and a global leader in educational materials for pre-kindergarten through grade 12 students.
It is also known for publishing iconic children’s book series such as Harry Potter, The Hunger Games, Clifford the Big Red Dog, and Goosebumps.
However, this reputation has been marred by the news of the breach, which reportedly exposed a mix of names, email addresses, phone numbers, and home addresses for U.S.-based customers and educators.
Some of the compromised data even included the full names of children registered by their parents.
Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free
How the Breach Unfolded
The hacker allegedly gained access to the data by stealing login credentials from a Scholastic employee who had been infected with malware.
Parasocial claimed that they infiltrated the company’s employee portal and managed to extract a vast dataset before being thwarted by an export limit on Scholastic’s servers.
The breach primarily included 4,247,768 unique email addresses, of which over 1 million belonged to “education contacts.” Teachers and administrators were reportedly among the most affected groups, as the breach included school-related information.
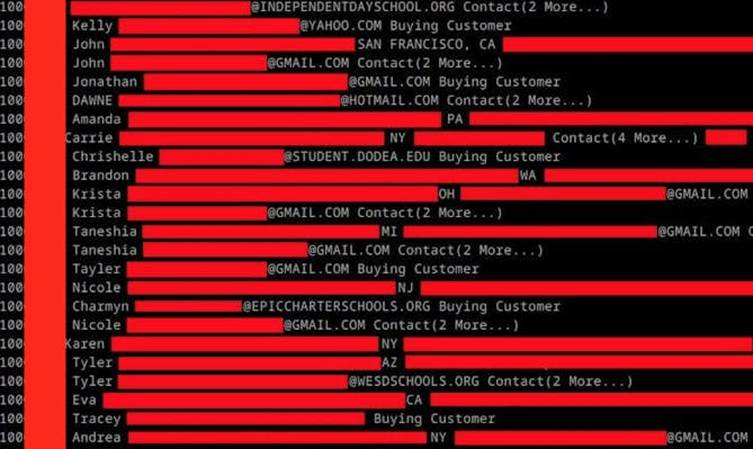
Parasocial shared their motivation in a statement to the Daily Dot, remarking that the attack stemmed from boredom rather than financial gain.
The hacker indicated they had no intention of making the data public but issued a stern critique of Scholastic’s lax security practices. “To Scholastic; lol get pwned.
This is a lesson to be learned the hard way. … Use MFA,” Parasocial said, urging the company to implement multi-factor authentication.
Adding an unusual twist, Parasocial requested a shout-out to “the puppygirl hacker polycule,” an apparent nod to the furry community—a subculture known for its interest in anthropomorphic animal characters.
While the furry community is not typically associated with cybercrime, it has, in the past, intersected with tech-savvy groups. One of them is SiegedSec, a hacktivist collective that disbanded after carrying out similar high-profile breaches.
Scholastic’s Response
In response to the breach, Scholastic stated they are taking the matter seriously and have launched a thorough investigation.
“Scholastic takes the security of our customers’ data seriously with extensive systems and protocols, and [we] are investigating this claim thoroughly,” a company representative noted, by DailyDot.
This incident underscores the growing need for robust cybersecurity measures, particularly for organizations managing sensitive data related to children and education.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!



.png
)
