A fast, secure, and private internet experience is essential to navigate the vast digital landscape. The Domain Name System (DNS) is a foundational element influencing your web browsing efficiency. Gcore Public DNS emerges as a powerful solution that elevates your internet experience by offering superior speed, enhanced security, and increased privacy.
The Gcore Public DNS service stands out for its impressive response times, being notably swift in Europe (9.36 ms), South America (5.44 ms), and Africa (11.32 ms). Leveraging a vast edge network with over 150 Points of Presence (PoPs) globally, it ensures an optimal browsing experience for users everywhere.
Easy Configuration Across Devices
Setting up Gcore Public DNS is a breeze, regardless of your device. Below are detailed instructions for a smooth setup:
iOS Devices Setup
For illustration, we’re using iOS version 17.3; note that steps may vary based on your iOS version.
- Navigate to Settings > Wi-Fi and select your network.
- Tap on Configure DNS, switch to Manual, and input the DNS addresses:
- Primary DNS: 95.85.95.85
- Secondary DNS: 2.56.220.2
- Confirm by tapping Save.
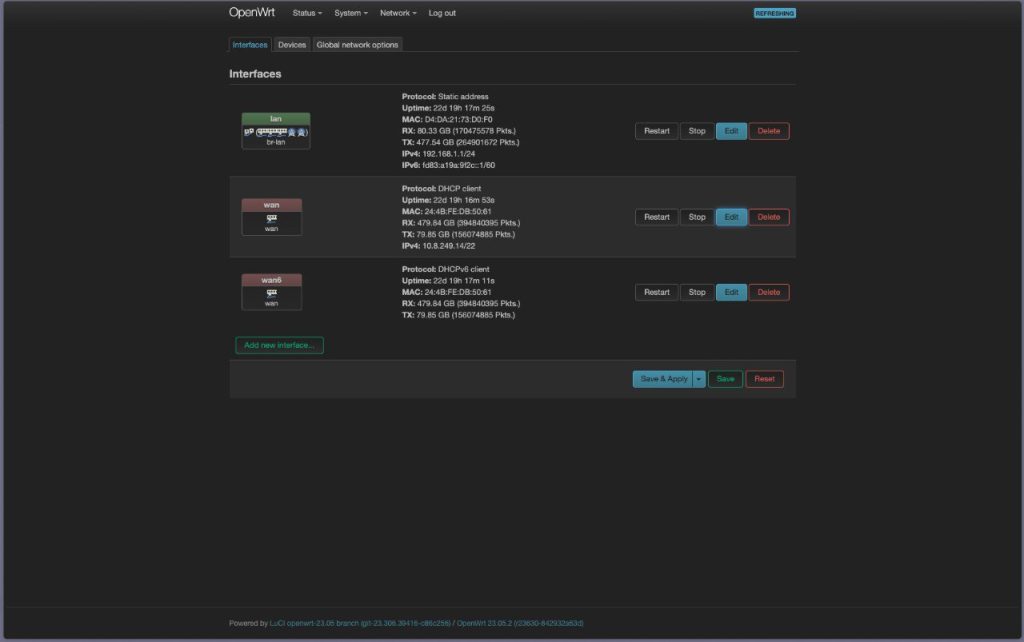
OpenWRT Router Configuration
This example uses OpenWRT version 23.05.2, with potential variations for other versions.
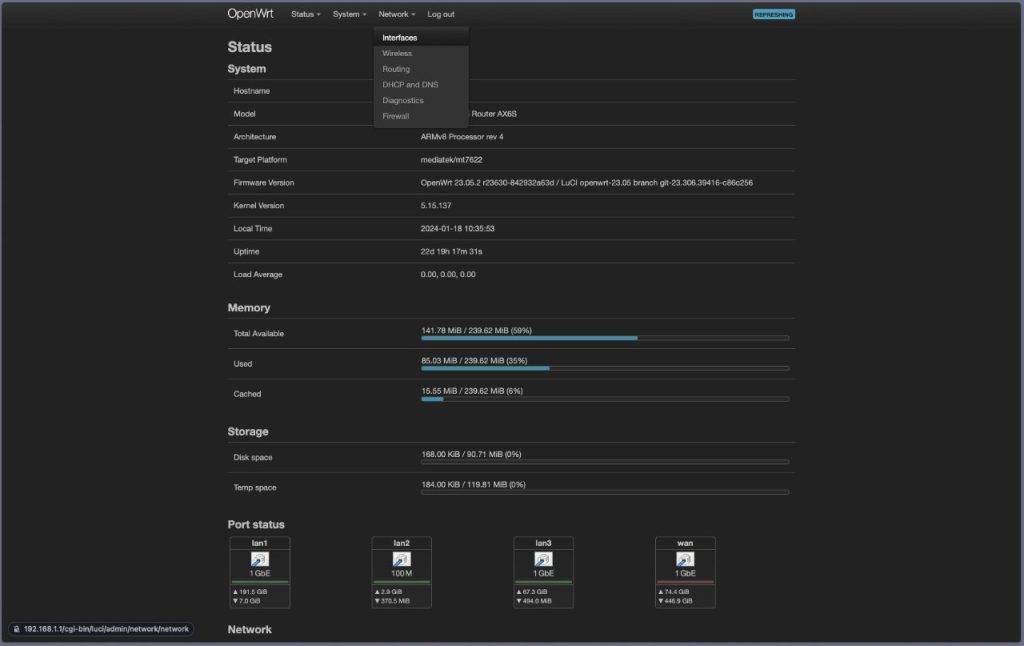
- Go to Network > Interfaces, then select WAN and click Edit.
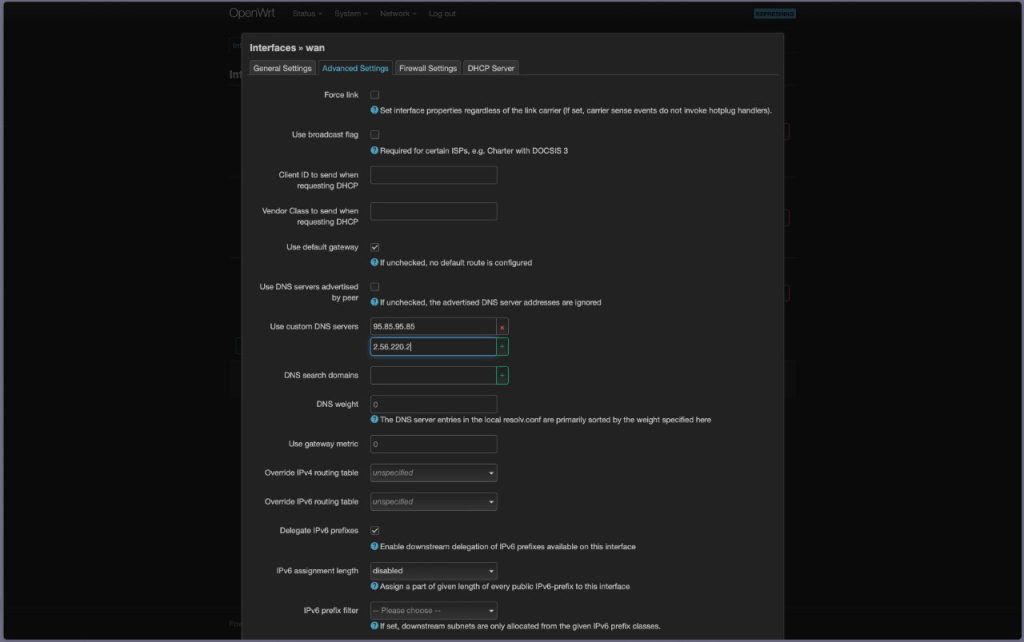
- In Advanced Settings, opt for Use custom DNS servers and enter:
- Primary DNS: 95.85.95.85
- Secondary DNS: 2.56.220.2
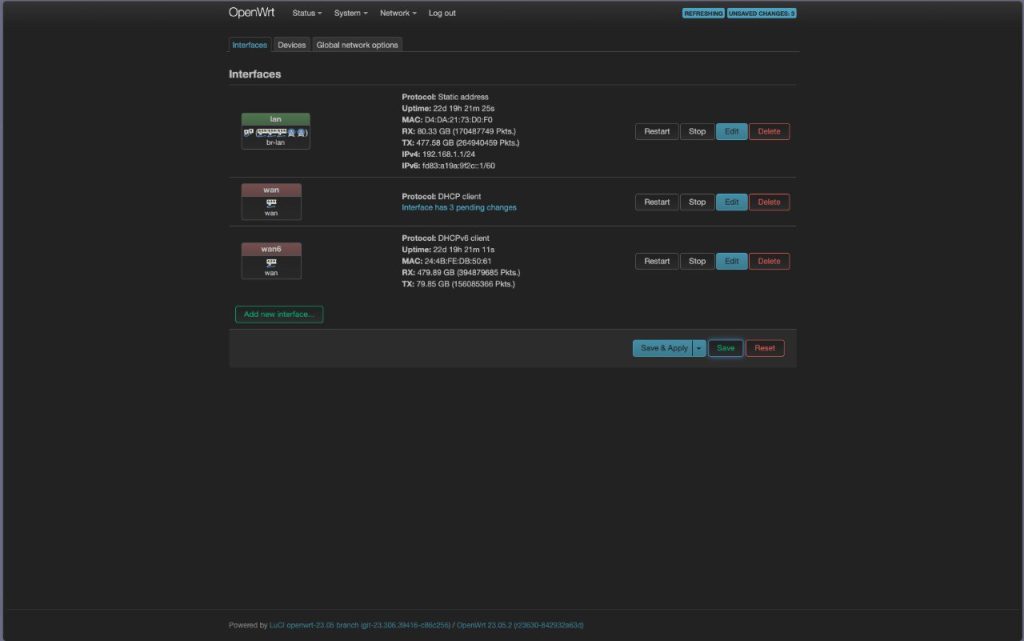
- Finalize by clicking Save on both the DNS settings and the interface list.
Enhancing Your Online Experience
Adopting Gcore Public DNS not only accelerates your web browsing but also fortifies your online security and privacy. By integrating this guide into your setup, you’re set to embark on a more efficient, secure, and private digital exploration.
.webp?w=696&resize=696,0&ssl=1)


.png
)
