The popular open-source platform Grafana, widely used for monitoring and observability, has been found to contain a severe SQL injection vulnerability.
This flaw allows attackers with valid user credentials to execute arbitrary SQL commands, potentially leading to data leakage and other security breaches.
Vulnerability Description and Impact
The vulnerability resides in the Grafana SQL package, specifically within the SqlDatasource.ts file, where SQL queries are handled and executed.
Attackers can exploit this by sending a malicious POST request to the /api/ds/query endpoint with a specially crafted raw SQL parameter.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
This flaw affects all versions of Grafana, including the latest releases.
As reported by GitHub, this vulnerability’s risk level is high because an attacker could access or manipulate sensitive data stored in the connected databases.
The impact is widespread as it affects all previous and current versions of Grafana, posing a significant threat to organizations relying on this data analytics and monitoring tool.
Vulnerability Analysis
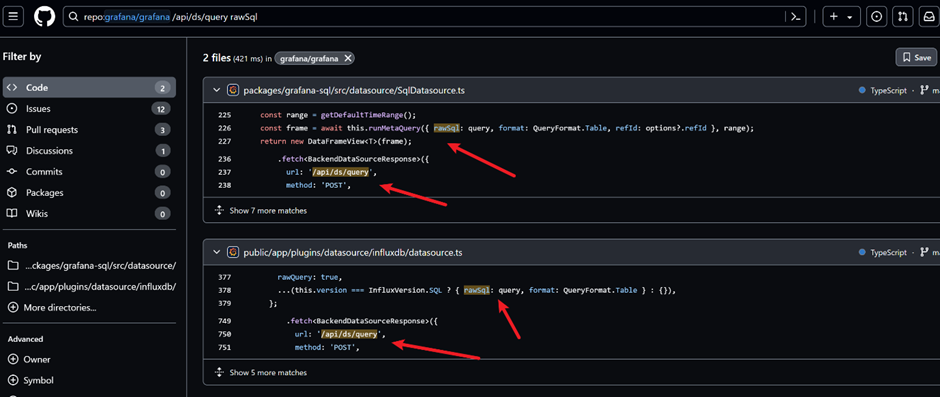
The issue’s core lies in the lack of proper validation of the SQL queries sent through the Grafana backend.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
The affected code blocks allow SQL statements to be executed without adequate checks, allowing attackers to inject malicious SQL code.
This is demonstrated in the source code from SqlDatasource.ts and datasource.ts files, where the run SQL and metricFindQuery functions, respectively, handle the SQL query executions.
The vulnerability explicitly allows time-based blind SQL injection, a more stealthy form of SQL injection that can be particularly difficult to detect and prevent as it does not return errors from the database.
Recurrence and Bug Repair
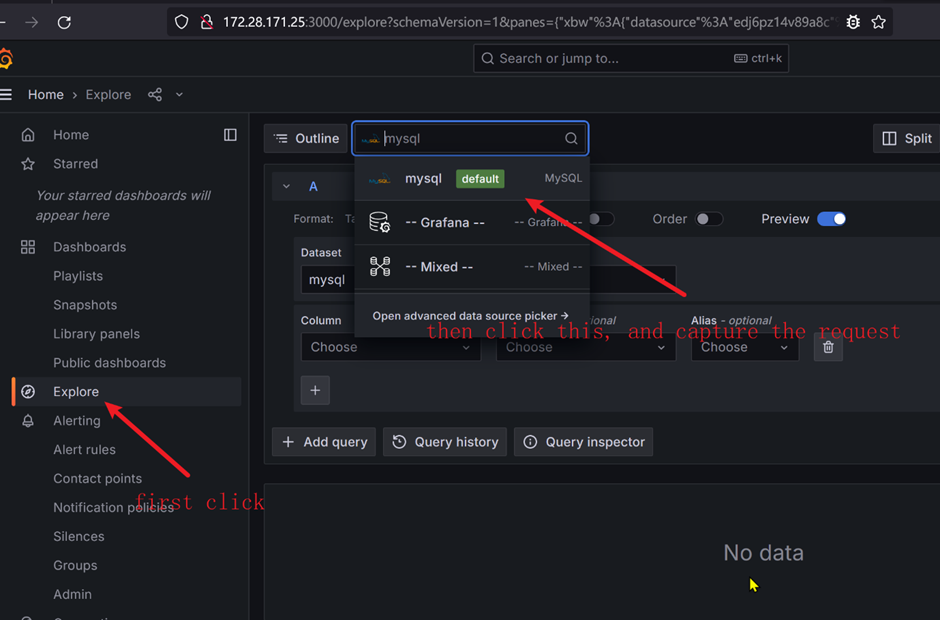
This is not the first time vulnerabilities have been reported in Grafana, and the recurrence of such security issues raises concerns about the overall security practices and vulnerability management within the Grafana development team.
Despite the severity, the Grafana security team does not recognize this flaw as a vulnerability but rather as a feature of the backend system.
This controversial stance highlights the challenges in perceiving and managing security risks in open-source projects.
Regarding mitigation, since Grafana does not validate queries sent to the DataSource proxy, the data sources connected to Grafana must have robust filtering and validation mechanisms to prevent SQL injection attacks.
The discovery of this SQL injection vulnerability in Grafana underscores the critical need for continuous security assessment and improvement, especially in open-source software used in sensitive environments.
Organizations using Grafana should implement additional security measures and stay vigilant for unusual activities in their systems.
As the debate continues about recognizing a feature versus a vulnerability, the security community will likely closely monitor how Grafana addresses this and future security issues.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training -> Try Free Demo
.webp?w=696&resize=696,0&ssl=1)


.png
)
