A newly discovered technique allows threat actors to circumvent Microsoft Outlook’s spam filters to deliver malicious ISO files, exposing organizations to sophisticated phishing campaigns.
The bypass leverages hyperlink obfuscation to disguise malicious links as benign URLs, enabling attackers to distribute malware-laden disk image files directly to victims’ inboxes.
As per a report by Afine, Security researchers warn that this method undermines email security defenses, particularly for organizations reliant on Outlook’s native spam filtering.
Evolving ISO File Exploitation Tactics
This development follows recent revelations about attackers exploiting ISO files to bypass Microsoft Defender SmartScreen, a security feature designed to block untrusted executables.
In earlier campaigns, threat actors used social engineering to trick users into extracting and running malware from ISO files after they were downloaded.
However, the newly identified method focuses on evading email-level defenses, allowing malicious files to reach users’ primary inboxes undetected.
Researchers highlight that ISO files remain attractive to attackers due to their ability to bypass traditional endpoint detection mechanisms.
Unlike executable (.exe) files, disk images are not inherently flagged as malicious, enabling threat actors to embed scripts, ransomware, or spyware within them.
How the Bypass Works
Outlook’s spam filtering system typically quarantines emails containing direct links to high-risk file extensions like .iso or .exe.
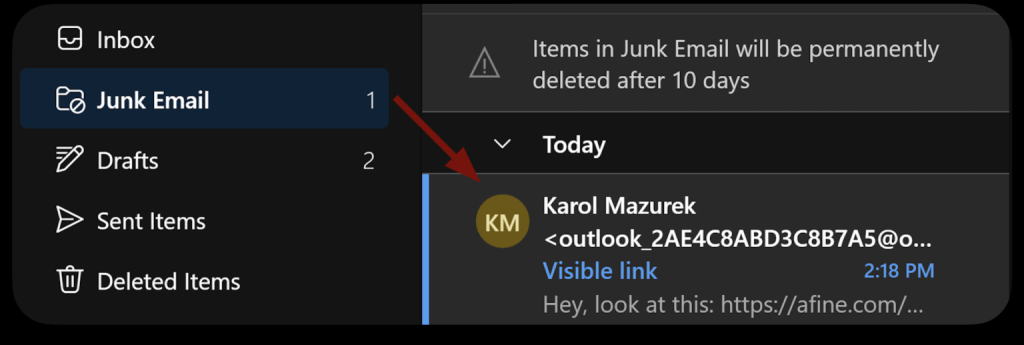
For example, an email with a visible link to https://malicious[.]com/update.iso would almost always be flagged and routed to the junk folder.
However, attackers now embed malicious URLs under seemingly harmless hyperlinks using HTML obfuscation:
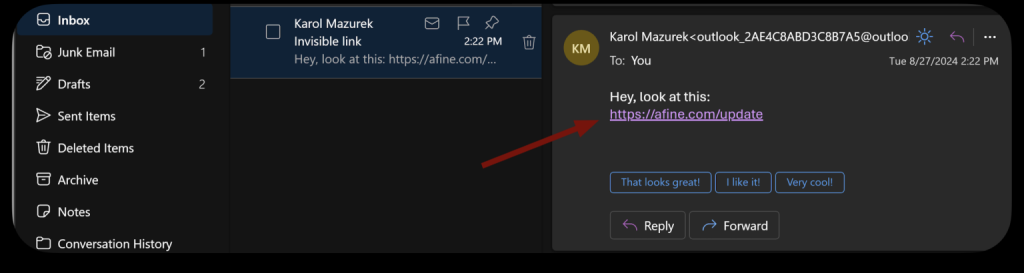
<a href="https://malicious[.]com/update.iso">https://trusted[.]com/security-update</a>Here, the visible text appears to link to a legitimate security update, but clicking it triggers the download of update.iso, a disk image containing malware.

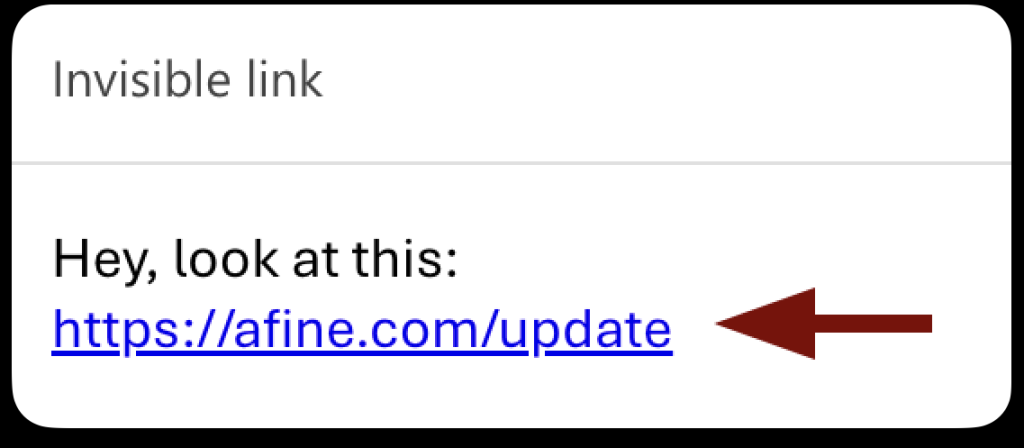
Proof-of-concept testing confirmed that Outlook’s filters fail to analyze the underlying href attribute, allowing such emails to bypass spam detection.
Widening the Attack Surface
This vulnerability significantly lowers the barrier for phishing campaigns, as attackers no longer need to rely on compromised websites or secondary payloads.
By delivering ISO files directly via email, threat actors can:
- Bypass Real-Time URL Reputation Checks: Many email security tools scan linked domains for known malicious activity but ignore the file path or extension.
- Exploit User Trust: Disguised links mimic legitimate software updates or document-sharing portals, increasing the likelihood of user interaction.
- Evade Post-Download Protections: As demonstrated in prior attacks, ISO files can bypass SmartScreen warnings when users manually extract and execute contained files.
Organizations without advanced email security infrastructure—particularly small and medium-sized businesses—are disproportionately at risk.
Microsoft has yet to comment on whether it will update Outlook’s spam filtering logic.
Independent researchers argue that the solution requires parsing href attributes and cross-referencing file extensions with threat intelligence feeds.
Until then, organizations must assume heightened risk and prioritize endpoint detection and response (EDR) tools to identify malicious ISO file activity.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here



.png
)
