Hackers are exploiting a vulnerability in Microsoft’s Azure App Proxy by manipulating the pre-authentication settings to gain unauthorized access to private networks.
The Azure App Proxy is designed to securely publish on-premises applications to the public internet without requiring firewall port openings, leveraging Microsoft Entra ID for authentication,.
How Azure App Proxy Works
For organizations to use Azure App Proxy, a private network connector must be installed on a system within their private network.
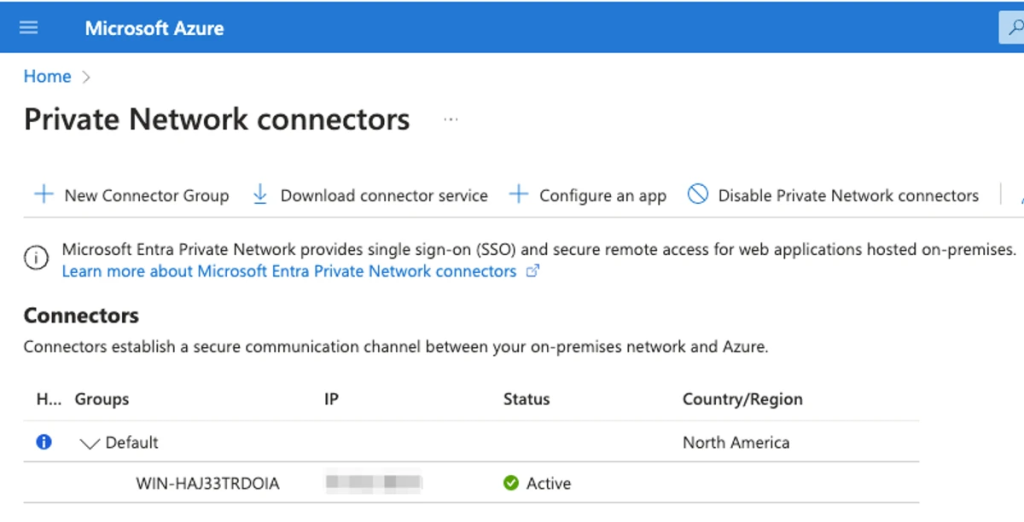
This connector establishes an outbound connection to Azure, allowing applications to be published through the proxy.
According to the TrustedSec report, the pre-authentication setting is crucial here, as it determines how users are authenticated before accessing published applications.
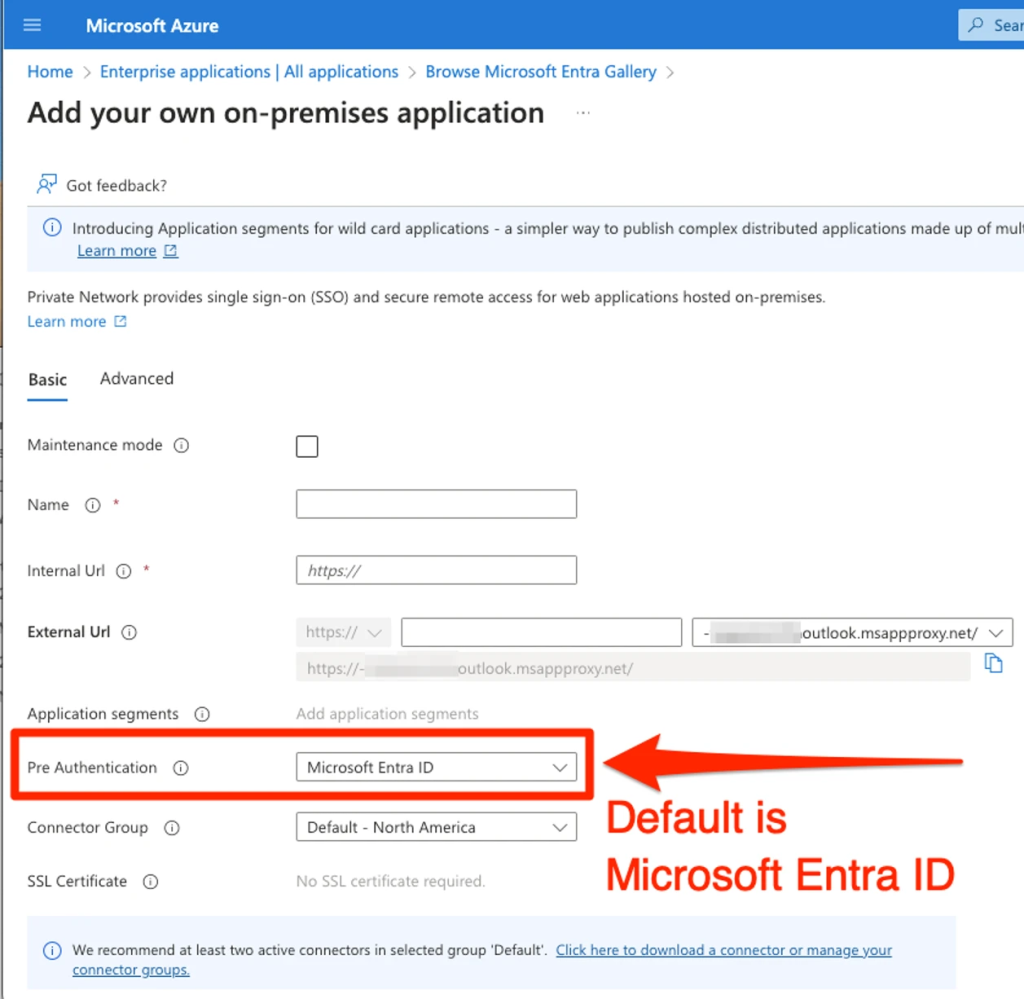
Pre-Authentication Settings
Azure App Proxy offers two pre-authentication options: Microsoft Entra ID and Passthrough.

Microsoft Entra ID is the default, providing robust authentication by redirecting users to Microsoft’s authentication services before accessing the application.
This ensures that all paths within the application are protected by Entra ID authentication.
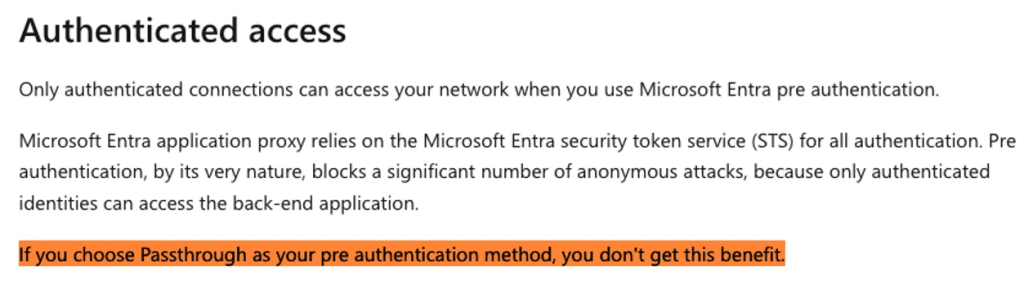
On the other hand, Passthrough does not require authentication before forwarding requests to the application.
While this option might seem useful for publicly accessible applications, it leaves them vulnerable to unauthorized access.
Microsoft’s documentation warns that Passthrough does not protect against anonymous attacks, similar to exposing a server port directly to the internet.
Risks and Exploits
In a demonstration setup using a Windows Server 2022 VM hosting a basic HTTP website, two applications were configured with different pre-authentication settings:
- MSENTRAID-redactedoutlook.msappproxy.net used Microsoft Entra ID for authentication, requiring users to authenticate before accessing the application.
- PASSTHROUGH-redactedoutlook.msappproxy.net, as expected, did not require authentication, allowing direct access to the application and its resources.
When using the Passthrough option, not only is the intended public application accessible, but so are other resources on the server. This can lead to unintentional exposure of sensitive private network resources.
For instance, if a sales quoting application at the root of the site uses Entra ID for authentication, while a customer portal at a different path is intended to be publicly accessible, using Passthrough could inadvertently make the entire server accessible.
Forced Browsing and Brute-Force Attacks
Hackers can easily exploit this vulnerability by engaging in forced browsing for content discovery.
Each request to the Passthrough URL reveals responses directly from the VM, including potentially sensitive applications or directories that were not intended to be public.
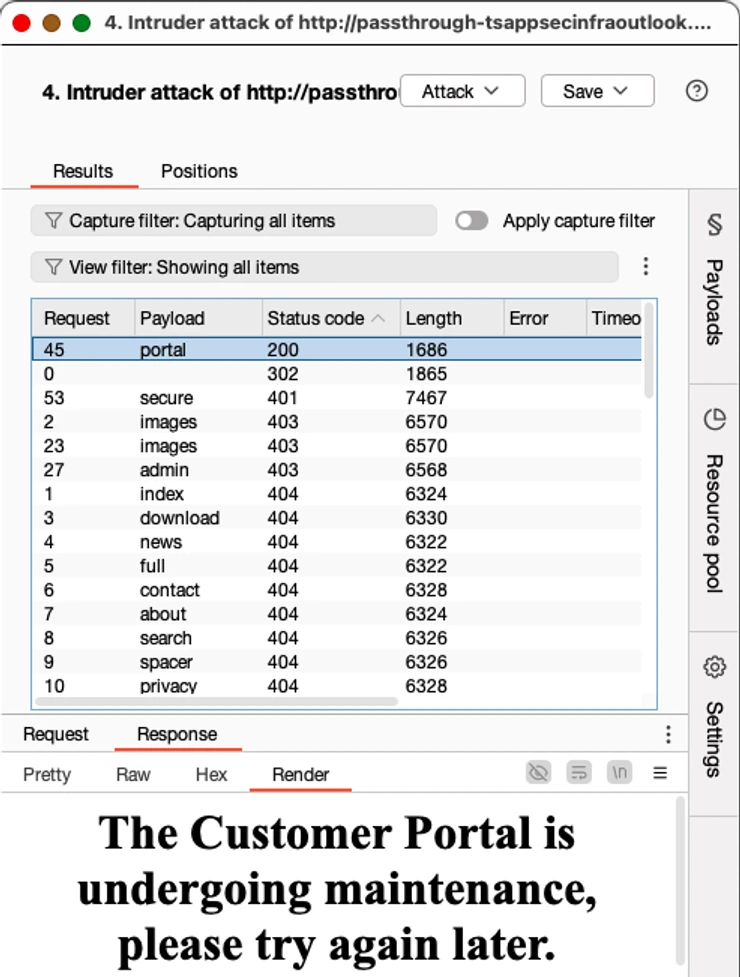
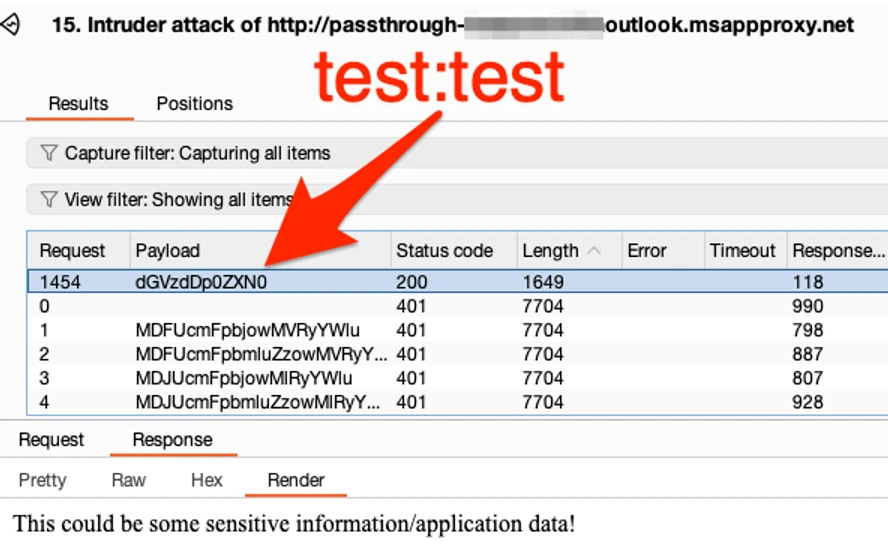
In the scenario where a path prompts for HTTP Basic authentication, attackers can use tools like Burp Suite’s Intruder to brute-force common default credentials such as admin:admin.
If weak credentials are used, unauthorized access to data or applications can occur, providing an entry point for malicious activities.
While the Azure App Proxy is a powerful tool for securing remote access to applications, misconfiguring pre-authentication settings can have severe consequences.
Organizations must carefully evaluate their use of Passthrough, ensuring that they understand the risks involved and take additional measures to secure applications and resources that are not intended for public access.
Regular security audits and strong authentication practices are crucial to mitigating these vulnerabilities and protecting sensitive private network resources.
By adopting these practices, organizations can effectively use Azure App Proxy while safeguarding their private network resources against unauthorized access.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
