The Indian Post Office portal recently exposed the sensitive Know Your Customer (KYC) data of thousands of users due to a critical vulnerability known as Insecure Direct Object References (IDOR).
This alarming flaw allowed unauthorized individuals to access private user information, including Aadhaar numbers, PAN details, addresses, and other personal records, merely by manipulating numbers in the URL.
The Vulnerability Unveiled
A Security Researcher unveiled in Medium that an IDOR vulnerability occurs when a web application inadvertently allows users to access restricted information by altering parameters in the URL without proper authentication checks.
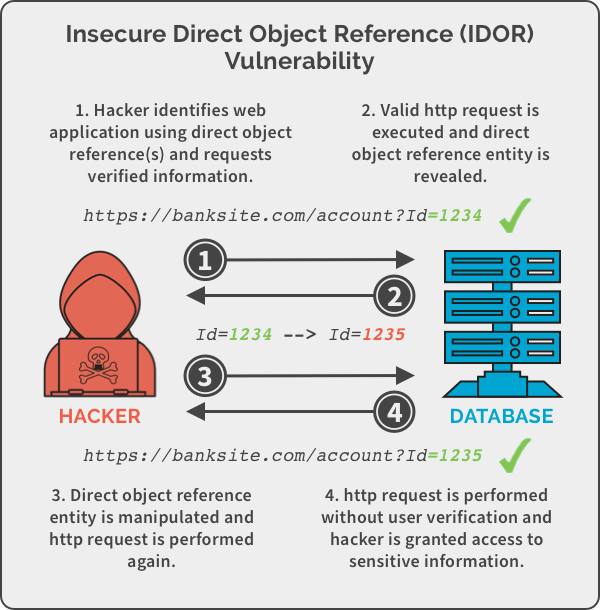
In this case, anyone with basic technical knowledge could retrieve sensitive KYC documents by incrementing or modifying document IDs in the URL, leaving confidential information unprotected.
For example, a sample request made to the Indian Post Office portal demonstrated how easily this data could be accessed.
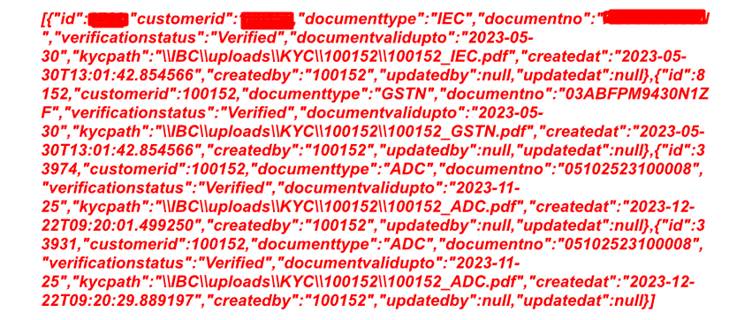
By sending a simple GET request without an authorization token, users were able to view sensitive information including user IDs, Aadhaar and PAN numbers, and links to downloadable KYC documents.
This lack of proper validation and authorization created a massive loophole for exploitation.
Sample Request and Response:
Request
text
GET /api/kyc/document?document_id=125678 HTTP/1.1
Host: govportal.in
Response
json
{
"status": "success",
"document_id": "125678",
"user_id": "345678",
"name": "Rahul Sharma",
"aadhaar_number": "XXXX-XXXX-1234",
"pan_number": "ABCDE1234F",
"kyc_document": "https://govportal.in/kyc_docs/125678.pdf"
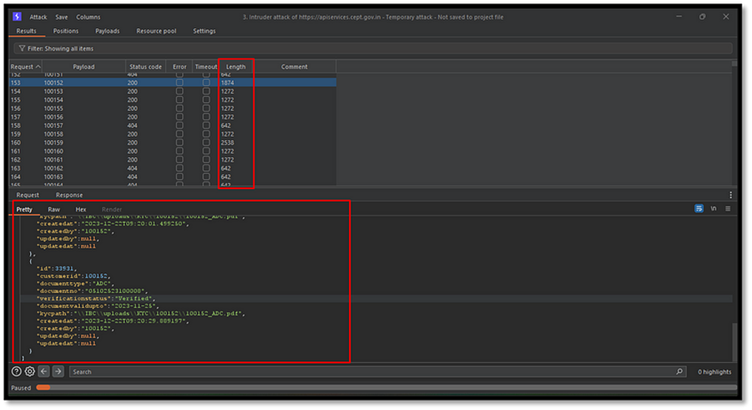
}The absence of authentication tokens made it possible to brute-force document IDs and retrieve the KYC records of other users, leaving critical personal data exposed.
Ethical Disclosure and Swift Action
Upon identifying the vulnerability, the researcher followed ethical protocols:
- The issue was immediately reported to the Indian Post Office and relevant cybersecurity authorities.
- The researcher highlighted the potential risks stemming from this flaw, including identity theft, phishing scams, and misuse of government data.
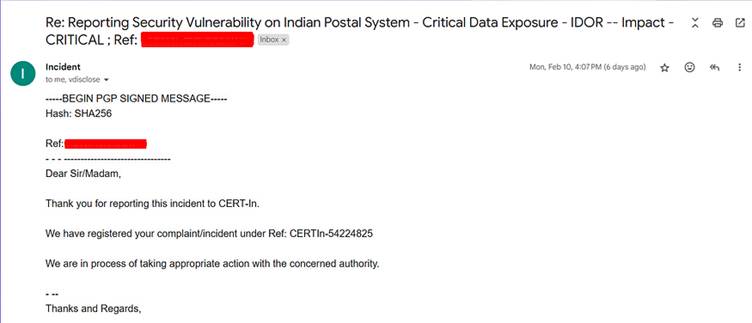
- The vulnerability was also shared with the Computer Emergency Response Team (CERT-In), India’s leading cybersecurity incident response team.
CERT-In responded promptly, acknowledging the report and coordinating efforts to secure the affected systems.
The Indian Post Office took swift action to address the issue, patching the vulnerability and securing its API endpoints.
Government platforms hold vast amounts of personal and financial data, making them prime targets for cyberattacks. A breach of this magnitude could lead to:
- Identity theft: Bad actors could misuse Aadhaar and PAN details for fraud.
- Phishing attacks: Access to personal data can enhance the effectiveness of scams.
- Legal repercussions: Mishandling KYC data risks violating privacy regulations under India’s impending Data Protection Act.
This incident highlights the urgent need for improved security measures in public sector platforms. Regular penetration testing, robust authentication protocols, and stronger API validations must be prioritized to prevent such breaches in the future.
The Indian Post Office’s proactive response and collaboration with CERT-In set an example of how organizations should handle disclosures responsibly.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
