A comprehensive survey conducted by Keeper Security, in partnership with TrendCandy Research, has shed light on the growing concerns within the cybersecurity community.
The survey, which gathered insights from over 800 IT and security executives globally, reveals a stark reality: 92% of respondents have observed a surge in cyber-attacks compared to the previous year.
The complexity and frequency of these attacks are putting unprecedented pressure on organizations, with a significant 73% having suffered monetary losses due to cyber incidents.
Vulnerable Sectors Under Siege
Cybercriminals are not indiscriminate in their targets. The survey identifies IT services, financial operations, and supply chain management as the most frequently attacked sectors within organizations.
The hospitality/travel, manufacturing, and financial services industries are also facing weekly and monthly attacks, with ransomware and phishing topping the list of concerns.
Industries at Risk

The New Wave of Sophisticated Attacks
The findings from Keeper Security’s survey highlight the urgent need for organizations to adapt their cybersecurity strategies to counter both existing and emerging threats.
A staggering 95% of IT leaders acknowledge that cyber-attacks are increasing in frequency and sophistication.
The most serious emerging threats include AI-powered attacks, deepfake technology, supply chain attacks, cloud jacking, IoT attacks, 5G network exploits, and fileless attacks.

AI-powered attacks are particularly concerning, as they enable cybercriminals to automate and scale traditional attack techniques like phishing and password cracking.
This has led to a call for a proactive cybersecurity approach that combines advanced defense mechanisms with fundamental best practices.
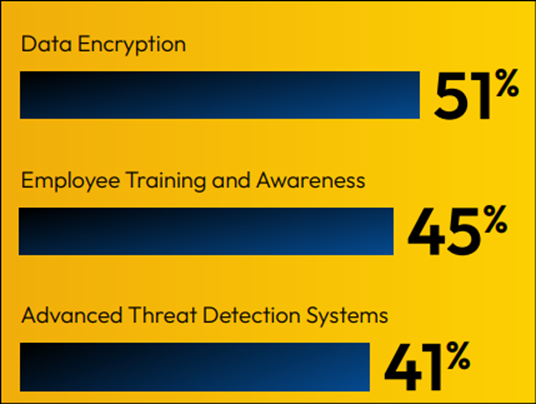
To combat these threats, IT leaders are planning to increase their AI security measures through data encryption (51%), employee training and awareness (45%), and advanced threat detection systems.
In North America, the focus is equally split between threat detection systems and data encryption, each at 50%.AI Security Measures
Phishing remains a significant challenge, with 67% of companies struggling to combat these attacks.
The rise of AI tools has made phishing scams more believable and harder to detect, with 84% of respondents finding them more difficult to identify.
Insider Threats and the Importance of PAM
Not all threats come from the outside; 40% of respondents have faced attacks from within their organization.
Privileged Access Management (PAM) solutions are crucial for managing and securing privileged credentials and enforcing the principle of least privilege to minimize damage from potential insider threats.
Despite the evolving threat landscape, fundamental cybersecurity practices remain crucial. Organizations are encouraged to adopt password and PAM solutions to prevent prevalent attacks.
A password manager can enforce strong password practices, while PAM solutions control and monitor high-level access.
These measures create a layered security approach that enhances overall cybersecurity resilience.
As cybercriminals continue to refine their tactics, IT and security leaders must remain vigilant and proactive in their defense measures to protect their organizations’ digital landscapes.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
%20(1).webp?w=696&resize=696,0&ssl=1)


.png
)
