Kali Linux, the renowned cybersecurity-focused Linux distribution, has just ushered in the new year with the release of Kali Linux 2025.1a.
This update builds upon the existing features, offering myriad enhancements and improvements designed to give users a streamlined experience.
Whether you’re already a seasoned Kali user or about to dive into the world of ethical hacking, this release promises exciting new tools and significant desktop environment upgrades.
Key Updates in Kali Linux 2025.1a
Desktop Environment Updates
- KDE Plasma 6.2
Kali Linux now comes equipped with KDE Plasma 6.2, marking a significant leap from the previous version 5.27. This update brings a fresh look to the desktop, including floating panels and a modern interface that enhances user interaction.
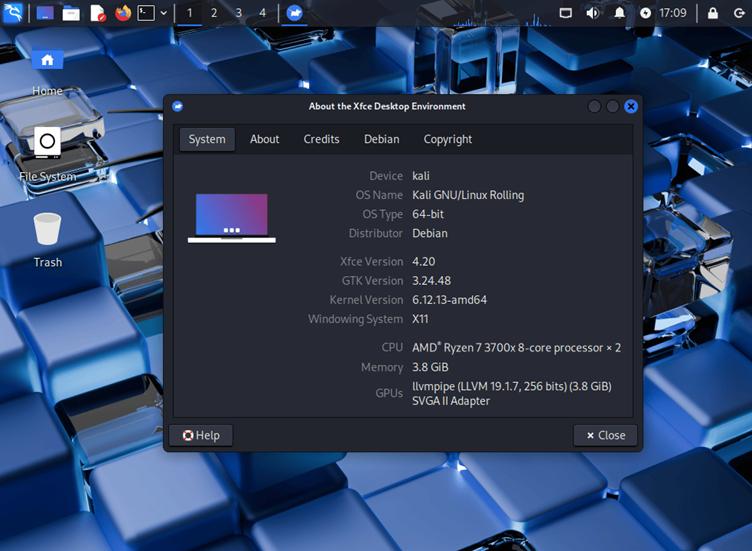
- Xfce 4.20
For users who prefer the lightweight Xfce environment, Kali Linux 2025.1a offers a bump to version 4.20. This update, released on December 15, 2024, includes a host of minor improvements and stability enhancements.
New Keyboard Shortcuts
To enhance user experience, several new keyboard shortcuts have been added to Xfce. Some notable additions include:
- File Manager: Ctrl + Alt + F, Super + E, and Super + F
- Run Command: Super + R (in addition to the traditional Alt + F2)
- Open Terminal: Super + T
- Open Browser: Super + W
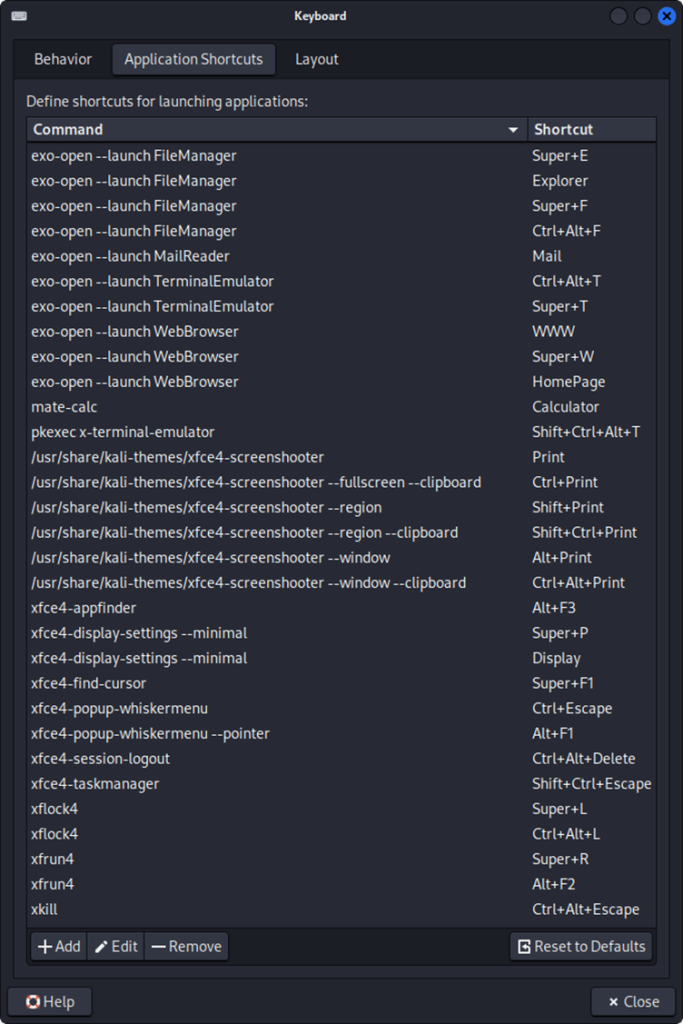
Window management shortcuts have also been expanded for easier handling in multi-monitor setups.
Raspberry Pi Enhancements
For Raspberry Pi users, Kali Linux 2025.1a introduces several significant changes:
- New Kernel: Based on version 6.6.74 from the Raspberry Pi OS kernel, providing support for the Raspberry Pi 5.
- Updated Firmware: Adoption of the raspi-firmware package, aligning with Raspberry Pi OS.
- Partition Layout: Mirrors Raspberry Pi OS images with changes to the /boot/firmware directory.
Kali NetHunter Updates
Kali NetHunter, the smartphone version of Kali Linux, sees exciting developments:
- CAN Arsenal: A new tab allows car hacking directly from your pocket, courtesy of V0lk3n.
- New Kernels: Updated kernels for various Samsung and Xiaomi devices.
One of the highlights of this release is the inclusion of hoaxshell, a Windows reverse shell payload generator that exploits HTTP(S) protocols for a beacon-like reverse shell.
Website and Documentation
The Kali Linux website now hosts additional wallpaper pages showcasing themes from past versions and community contributions. Documentation has also been expanded with guides on configuring kernels for CAN and NetHunter-specific articles.
Getting Started with Kali Linux 2025.1a
Whether you’re upgrading an existing installation or downloading a fresh image, getting started with Kali Linux 2025.1a is straightforward:
Upgrading an Existing Install
If you already have Kali Linux installed, you can upgrade using the following commands:
echo "deb http://http.kali.org/kali kali-rolling main contrib non-free non-free-firmware" | sudo tee /etc/apt/sources.list
sudo apt update && sudo apt -y full-upgrade
cp -vrbi /etc/skel/. ~/
[ -f /var/run/reboot-required ] && sudo reboot -fFor those looking for the latest builds or specific hardware support, Kali Linux provides weekly images in addition to the standard release images.
These images are perfect for users wanting the most recent packages and bug fixes without waiting for the next major release.
Kali Linux 2025.1a represents a significant step forward, blending security-focused tools with a modern, user-friendly interface.
With its enhancements in desktop environments, Raspberry Pi support, and NetHunter updates, this release is poised to be a favorite among cybersecurity professionals and enthusiasts alike.
Whether you’re diving into the world of ethical hacking or updating from a previous version, Kali Linux 2025.1a has something for everyone.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
