Kr00k, a security flaw in Wi-Fi chips allows attackers to decrypt the WPA2-encrypted traffic.
The vulnerability affects Broadcom and Cypress chips, these are the most common chips used by several client devices including top brands such as Amazon (Echo, Kindle), Apple (iPhone, iPad, MacBook), Google (Nexus), Samsung (Galaxy) and others.
Not only client devices this vulnerability also affects the Wi-Fi Access points and routers.
Kr00k Vulnerability
Security researchers from ESET discovered the vulnerability dubbed Kr00k and assigned CVE-2019-15126. An attacker can exploit the vulnerability by eavesdropping the communication of an unpatched device.
If the attack is successful then attackers can exfiltrate sensitive data from the target device. The attack abuses implementation flaws with Wi-Fi chips.
Generally, packets are encrypted with a unique key based on the Wi-Fi network password. When a device disassociated from the Wi-Fi network, with the vulnerable chips keys are zeroed out and then buffered data sent with zero encryption.
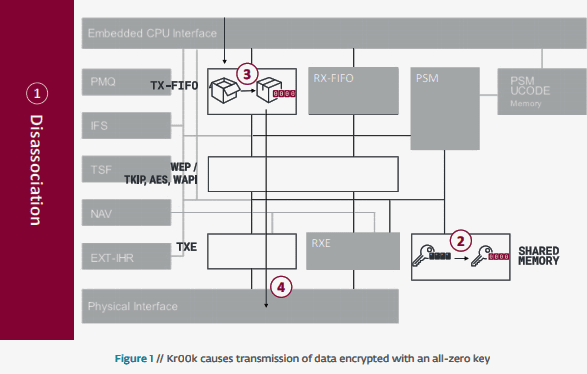
By triggering the disassociation continuously the attacker can decrypt some wireless network packets transmitted by a vulnerable device.
The vulnerability affected both WPA2-Personal and WPA2-Enterprise protocols, with AES-CCMP encryption.
Kr00k also related to KRACK vulnerability which was founded in 2017. “Kr00k is one of the possible reasons behind the “reinstallation” of an all-zero TK, which has been observed while testing for KRACK attacks.”
Here is the difference between KRACK and Kr00k

ESET reported the vulnerability to chip manufacturers Broadcom and Cypress who fixed the issue, also ESET worked ICASI to make sure all the vendors aware of Kr00k.
The vulnerability is no way associated with the Wi-Fi password, changing the Wi-Fi password is not a fix for the vulnerability.
If you are using affected chips, it is recommended to update devices with Broadcom or Cypress chips to the latest software versions.
Device manufacturers are recommended to chip manufacturer for details about patches for the Kr00k vulnerability.



.png
)
