The term “Lazarus Group,” once used to describe a singular Advanced Persistent Threat (APT) actor, has evolved to represent a complex network of sub-groups operating under shared objectives and tactics.
This shift reflects the growing scale and diversification of their cyber activities, making traditional classifications increasingly obsolete.
Security analysts now argue that “Lazarus” serves as an umbrella term encompassing multiple specialized units rather than a single cohesive entity.
The reclassification stems from the challenges of accurately attributing cyberattacks.
Various sub-groups under the Lazarus umbrella, such as APT38, Bluenoroff, Andariel, and others, have overlapping tactics, techniques, and procedures (TTPs).
These overlaps complicate efforts to distinguish between individual actors and campaigns.
For instance, sub-groups like Citrine Sleet and Moonstone Sleet share similar attack vectors, such as using LinkedIn to lure targets into downloading malicious npm or Python packages.
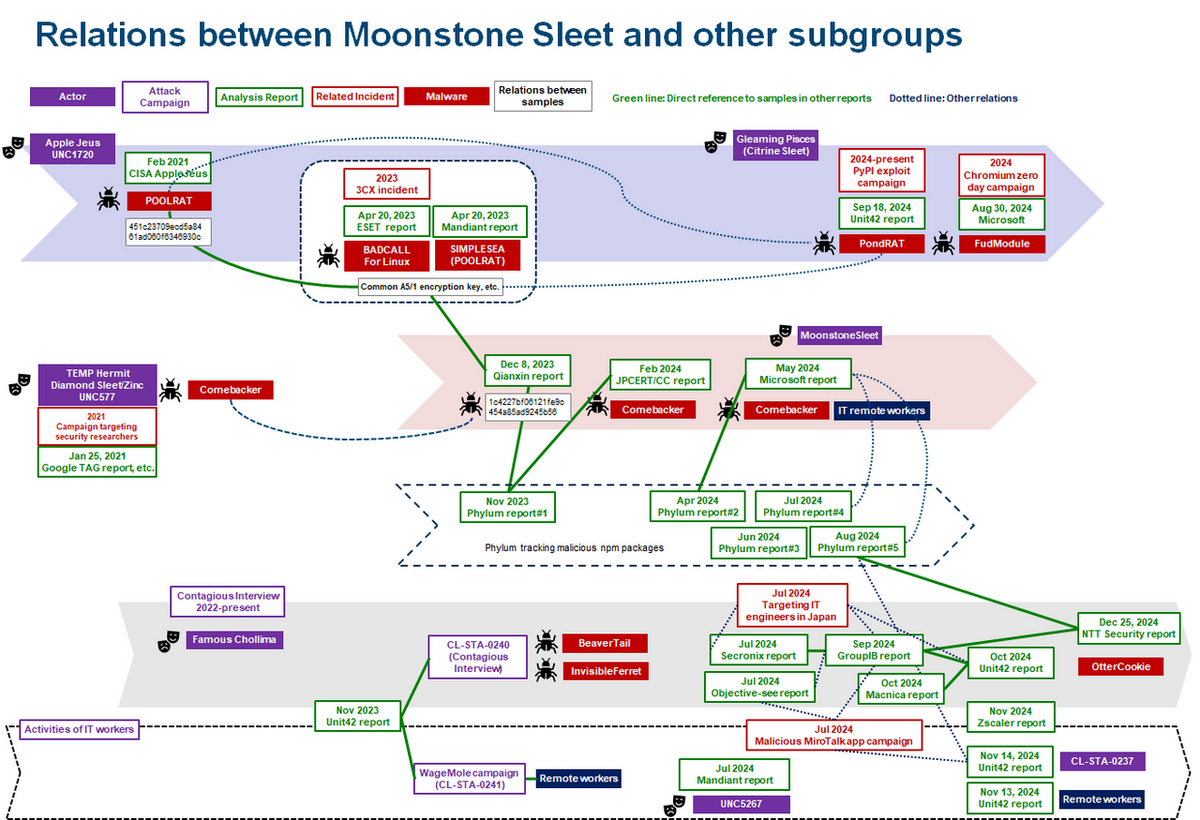
Despite these similarities, their objectives ranging from cryptocurrency theft to ransomware deployment often diverge.
Characteristics of Lazarus Sub-Groups
The proliferation of sub-group classifications highlights the complexity of this network.
Security vendors have introduced numerous labels for both attack campaigns and sub-groups, further muddying the waters.
For example:
- Campaign Names: Operation Dreamjob, AppleJeus, and Contagious Interview.
- Sub-Group Labels: TEMP.Hermit, Sapphire Sleet, TA444, and Silent Chollima.
Some labels initially referred to specific campaigns but later came to denote entire sub-groups or successor entities.
According to the Report, this inconsistency underscores the difficulty of maintaining a unified taxonomy across the cybersecurity community.
Adding to the complexity is the emergence of task force-like entities such as Bureau325, which operate outside traditional subgroup structures but share TTPs with Lazarus-affiliated units.
Such developments blur the lines between distinct groups and collaborative efforts.
Why Sub-Group Identification Matters
Detailed identification at the subgroup level is critical for several reasons:
- Targeted Alerts: By understanding the specific objectives and industries targeted by each subgroup (e.g., cryptocurrency businesses or defense sectors), security professionals can issue more precise warnings.
- Effective Countermeasures: Tailoring responses to the unique characteristics of each subgroup enhances the efficacy of defensive strategies.
- Strategic Messaging: Accurate attribution sends a deterrent message to attackers by demonstrating defenders’ analytical capabilities.

For example, Moonstone Sleet’s ransomware activities differ significantly from Citrine Sleet’s cryptocurrency-focused exploits.
Identifying these distinctions enables more effective resource allocation for mitigation efforts.
The Lazarus Group’s evolution into a constellation of sub-groups reflects broader trends in cyber threat landscapes.
As attackers adopt more sophisticated organizational structures, defenders must refine their attribution methodologies to keep pace.
While subgroup-level analysis may seem overly granular, it offers invaluable insights for long-term threat mitigation and strategic counter-operations.
The cybersecurity community must continue adapting its frameworks to address these challenges effectively.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!



.png
)
