Web-based applications security relies on a number of factors among them is a Web Application Firewall (WAF). Cyberattacks are pouring in numbers and users will need an effective WAF to take care of their web-accessible data.
Organizations that are in-route to procure a Web Application Firewall should first understand the business demands, technical aspects of the WAF tool, and the offerings.
While measuring a WAF provider, organizations should check for its detection and mitigation capabilities, reporting options, logging routines, reliance on the environment, integrity, and how easy are they to be managed.
Once the organizations know what to look for while choosing their WAF provider then the rest of web-accessible data can be assured of security and vigilance.
In this article we’ll look into five key capabilities one should look for while choosing a WAF provider
Web Application Firewall Integration with Business
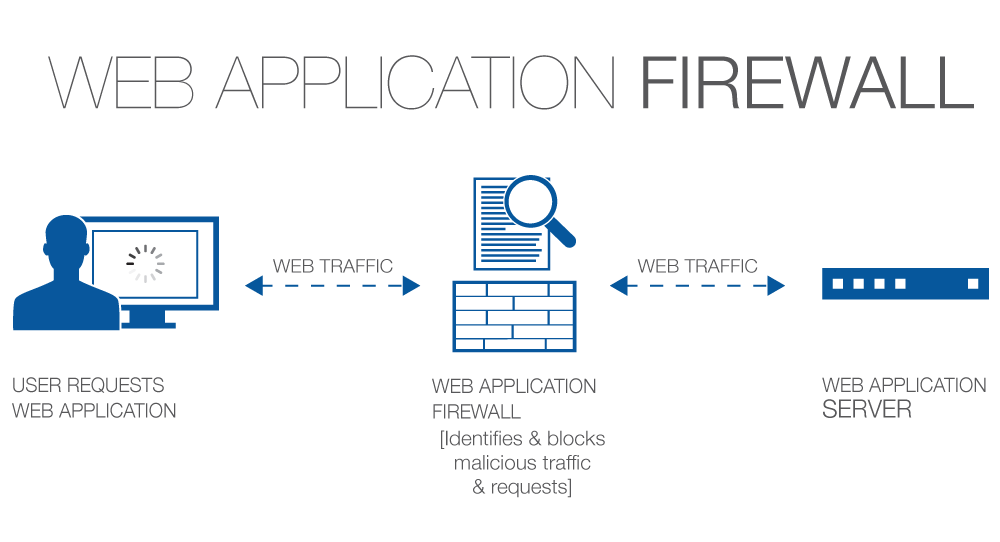
The first capability would be WAF’s integration with your business environment, i.e.; how easily this WAF can be employed in your network to ease further routines. There are different methods to employ a WAF, this could be inline appliance, cloud-based or integrated WAF.
Inline Appliance
In this method, a device is placed between the users and the web application. This type of WAF will require additional expertise apart from the IT administration, something like network administration or firewall management will do. Organizations will need expert tech staff to get this implemented.
Cloud-based WAF
In this method, a DNS redirection is designed from the vendors IP address to the web application hosts IP address. Decrypting happens at vendor end and hence the SSL keys have to be provided by the organizations for transferring the data.
Integrated WAF
In this type of WAF, the process is handled mostly in coding at enterprise web application or web servers. However, this would also need technically strong staff to implement, but does not require any DNS redirections or change in network architecture.
WAF Detection and Response
WAF takes care of requests by analyzing the type of content and communication that is requested. The strength of this WAF depends on its ability to protect enterprise data. The Web
WAF can employee a blacklist or whitelist approach to keep the network safe, along with the cross-site scripting, and SQL injection detection, which usually happens using a common character and demeanor. Hence the Web Application Firewall should always be kept updated for new threats.
The blacklist approach blocks any anonymous and notorious demeanor, and the white list approach allows only trusted requests to pass through the WAF. Along with these, the
At times Web Application Firewall may need to be well-matched with other network devices to block and implement its daily routines. So organizations should measure these capabilities and compatibleness before making their choice. WAF should provide visibleness over the network risks and provide security accordingly.
WAF Logging and Alerting
Web Application Firewall should be able to log and alert the IT administrators whenever there is some infamous
These logs will help analyze the how, when and where scenarios of a data breach or potential threat and understand the root cause for an issue and fix it effectively using the right solution.
WAF Management
WAF being an application firewall it will be impractical to expect it to be a one-time configuration effort and expect the applications to be secure. Applications are changing very frequently and integrate with
Key Aspects of Management Include
- Do you have the expertise or does the vendor provide it as part of the product to update rules based on security risk postures in the application tied with your security and vulnerability management program.
- Do you have process, time and expertise to test for false positives before doing policy
updates. Vendors such as AppTrana as part of their managed services provide managed custom rules with a Zero WAFFalse – positive gu a rantee backed with SLA and penalty clauses - Do you have 24×7 support and ability to work closely when
a n incident happens and isolate the problem and take corrective actions
Other Checklists
Businesses should also analyze the management layer of the Web Application Firewall, whether they are taken care of themselves or by a third party vendor. And their reporting capabilities, which may even include reporting from other detection solutions.
Checking the tool’s case studies with other enterprises can help your organization decide how good was this Web Application Firewall in real-time. Also checking the options for Zero FP promise backed with SLA and penalty clauses could be a rewarding evaluation to be noted.
Purchasing WAF for your Business
The purchase decision should be made only after a detailed evaluation of predefined checklists of features and network requirement, matchmaking could be another better option approach. Your technical team along with the R&D should help decide the better WAF provider in the market by trial evaluating different products during the time. Five things that will summarize WAF providers is
1. management
2. Compatibility
3. Security
4. Reporting
5. Support
So readers, make sure you define your requirement, understand the possible solution, gather the list of WAF providers, evaluate each of them for their features and restrictions, and finally choose your piece only with guidance from your tech and finance team.
There are a couple of good WAF providers like Indusface, who as part of their AppTrana product offers a fully-managed Web Application Firewall that includes Web Application Scanning, Penetration testing , DDOs protection and a CDN that helps to detect web vulnerabilities, protect against them instantly, accelerate your website speed and get continuous monitoring as part of the managed service bundled under a single offering
Please read through this article, understand the five key capabilities to look for in a WAF provider and let us know if you have any better suggestion regarding evaluating the right WAF for your business.



.png
)
