Over 39 million API keys, credentials, and other sensitive secrets were exposed on GitHub in 2024, raising considerable alarm within the developer community and enterprises globally.
The scale and impact of this leak have underscored the growing risks tied to improperly handled credentials and highlighted the urgent need for robust security practices.
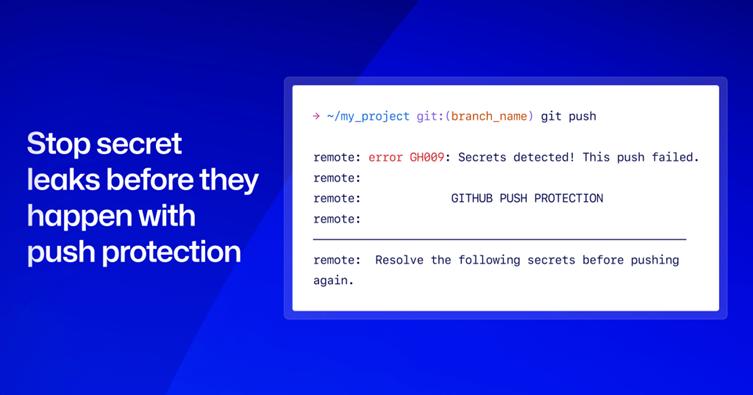
GitHub, the world’s largest platform for software collaboration, revealed that its systems intercepted millions of leaked secrets throughout last year using its push protection tools.
However, a significant number of sensitive assets were still inadvertently shared, often by well-meaning developers unaware of the risks.
Why Secret Leaks Are Critical
Secrets like API keys, tokens, and credentials are essential components of modern software development.
They allow systems to communicate securely, authenticate services, and manage sensitive data. Unfortunately, developers often expose these secrets accidentally when committing code, sharing repositories, or during collaborative development.
Even seemingly benign leaks can provide attackers with a foothold into larger systems. A single compromised API key often leads to lateral attacks across an organization, risking critical infrastructure and data.
Further complicating the issue, GitHub noted that accidental misconfigurations, such as making private repositories public, surged to record highs in 2024.
GitHub’s Enhanced Security Push
In response to escalating security challenges, GitHub has ramped up its efforts to mitigate secret leaks across its platform. Among its noteworthy initiatives:
- Push Protection by Default: To prevent exposed secrets before they occur, GitHub now automatically scans public repositories for sensitive information. This feature is built into its platform and effectively blocks secret-leak attempts in real time.
- Partnership Program with Token Issuers: GitHub collaborates with major providers like AWS, Google Cloud, and OpenAI to detect leaked secrets swiftly. If detected, these partners can quarantine or revoke compromised tokens immediately.
- Standalone Security Enhancements: GitHub has made its security tools, such as Secret Protection and Code Security, available as standalone products. Previously bundled under premium plans, this move aims to democratize access to security features for smaller teams and organizations.
A Path Forward for Developers
The incident serves as a wake-up call for organizations and developers to prioritize secure secret management. Experts suggest adopting best practices, including:
- Automation: Minimize human interaction with secrets by automating their creation, rotation, and revocation.
- Regular Scanning: Use continuous monitoring solutions, such as GitHub’s built-in secret scanning tools, to address leaks before exploitation occurs.
- Least Privilege Principle: Limit access to secrets only to users and apps that require them.
While GitHub’s efforts to bolster its security infrastructure are commendable, the responsibility to protect secrets ultimately lies with developers and organizations.
With cyberattacks increasingly exploiting exposed credentials, proactive measures are no longer optional—they’re a necessity. For developers, staying informed and adopting secure practices will remain critical to combating future threats.
GitHub’s recent advancements in security underscore the gravity of the issue and the need for collaborative solutions to safeguard the global software development ecosystem.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
