Radware’s comprehensive research into the cybersecurity landscape has uncovered significant trends shaping the financial services industry’s vulnerabilities in 2024.
The analysis, conducted across 46 deep-web hacker forums, identified over 26,000 threat actors’ discussions that revealed increasingly sophisticated cyberattack methods.
The study highlights the adoption of advanced tools and strategies by cybercriminals, underscoring the urgent need for financial institutions to reinforce their defenses against a rapidly evolving threat landscape.
Underground Infostealer Economy Thrives
One major finding is the rise of the “infostealer economy,” which underscores the growing sophistication of cybercriminal marketplaces.
Radware’s research revealed that deep-web forums frequently discussed information-stealing malware, with an average of 3-4 daily mentions of “infostealer-as-a-service” offerings.
These malware services are tailored for different market segments, ranging from individual threat actors to Advanced Persistent Threat (APT) groups.
Infostealer developers emphasize compatibility with other hacking tools and modularity in their offerings.
Many products come with plug-ins and enhanced user interfaces designed to cater to individual hackers with low-price plans and full technical support.
For APT groups, specialized features such as capabilities to compromise corporate Outlook accounts are being marketed.
One noteworthy example, Mystic Stealer, demonstrates the ability to target email credentials, which could pave the way for ransomware attacks using stolen enterprise credentials.

Credential-as-a-Service Platforms Expand
Another alarming trend is the growth of credential-as-a-service (CaaS) platforms, which operate through subscription models to distribute freshly breached credentials.
These services are becoming increasingly sophisticated, evident in the shift away from traditional text-based lists to more advanced distribution methods.
Radware’s analysis found that Combo Cloud, one such platform, experienced a 46% increase in mentions between 2022 and 2024.
The service provides credentials sorted by industry and geographic location, offering cybercriminals streamlined access to targeted financial accounts.
This evolution in credential marketplaces signals a growing risk to financial institutions as attackers gain access to increasingly tailored tools for breaching protected systems.
The emergence of One-Time Password (OTP) bot services represents a new frontier in social engineering attacks.
Operated primarily through Telegram, these bots automate the theft of two-factor authentication (2FA) codes, making the process scalable.
Attackers first gather a list of potential targets through credential stuffing and subsequently use OTP bots to impersonate legitimate entities like banks or customer service representatives.
Victims are lured into sharing 2FA codes under the guise of fraud alerts or account verification, enabling cybercriminals to gain full control of accounts by locking out legitimate users.
Radware’s research identified 38 distinct OTP bot services available on the dark web, ranging from $10 to $50 per attack.

Mentions of these services increased by 31% over the past year, with 1,354 references recorded during the study period.
Distributed Denial-of-Service (DDoS) attacks have also become more accessible and potent, fueled by advancements in AI technology.
The DDoS-as-a-service ecosystem has expanded, with 34 tools available to over 196,000 followers.
For as little as $50, attackers can now generate traffic of up to 35,000 requests per second directly from mobile devices.
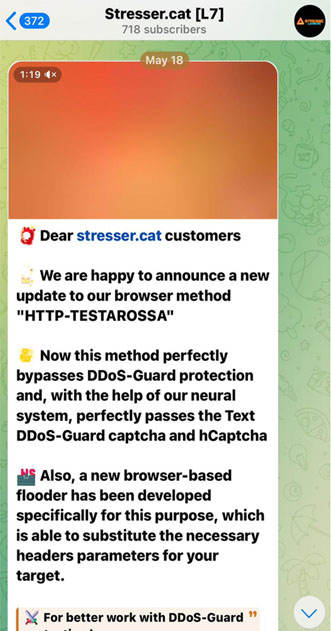
Radware documented the debut of “Stressed Cat,” a new DDoS tool incorporating AI-driven captcha-solving capabilities.
Unlike traditional DDoS methods that attempt to bypass captchas, AI-enabled tools can actively solve them, increasing attack efficiency and circumventing captcha-reliant defense mechanisms.
This innovation marks a significant escalation in the capabilities of DDoS attacks, making them harder to detect and mitigate.
Radware’s findings highlight the decentralization of cybercrime, with clear separations between attack developers and executors.
This fragmentation complicates attribution and hampers law enforcement efforts.
For financial organizations, the stakes are higher than ever, as cybercriminals continue to refine their tactics and develop highly specialized tools to breach security measures.
The report emphasizes the need for cybersecurity professionals to shift from reactive approaches to proactive strategies that leverage external threat intelligence.
By understanding the dynamics of dark web forums and emerging cybercrime trends, organizations can better anticipate threats and implement defenses that address the evolving tactics of adversaries in the cyberspace.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
