PandaBuy, a popular online shopping platform, has been the victim of a significant data breach.
This breach has resulted in the leak of personal information belonging to more than 1.3 million customers.
The incident has raised serious concerns about cybersecurity practices and consumer data protection in the digital age.
The breach was first brought to light by members of the BreachForums, an infamous cybercrime forum.
Two threat actors, known by pseudonyms ‘Sanggiero’ and ‘IntelBroker,’ claimed responsibility for the hack.
AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
They alleged that they exploited several critical vulnerabilities in PandaBuy’s platform and API to gain unauthorized access to the company’s database.
The leaked data is extensive and includes sensitive personal information such as User IDs, first and last names, phone numbers, email addresses, login IPs, order details, home addresses, zip codes, and countries of residence.
According to the announcement on BreachForums, the dataset comprises over 3 million rows of data, indicating the scale and severity of the breach.
Evidence and Confirmation
To substantiate their claims, Sanggiero published a sample of the stolen data on the cybercrime forum and offered it for sale.
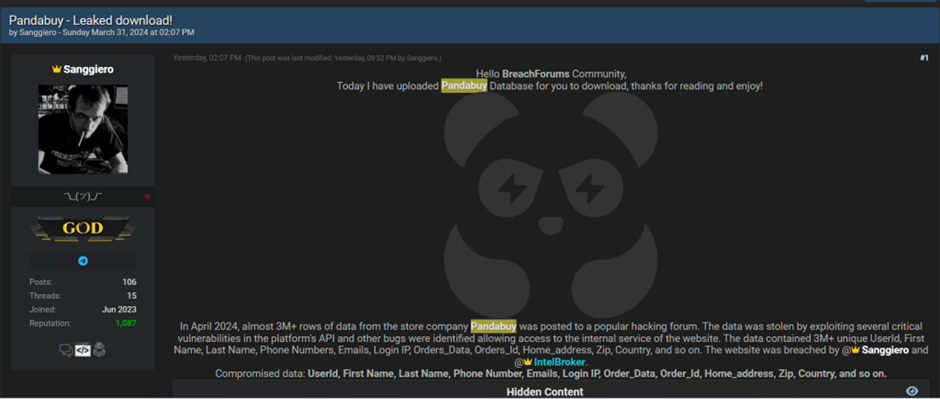
@Sanggiero and @IntelBroker breached the website.” reads the announcement published by BreachForums.
This action has confirmed the breach and exposed the affected customers to potential further cybercrimes, including identity theft and phishing attacks.
Troy Hunt, the founder of Have I Been Pwned (HIBP), tweeted that a website that allows internet users to check whether data breaches have compromised their personal information confirmed the validity of 1.3 million email addresses from the leaked dataset.
Hunt has since added these addresses to HIBP, enabling individuals to check if the breach impacted them.
PandaBuy’s Response and Controversy
PandaBuy has not officially acknowledged the security breach.
Troy Hunt confirmed allegations that the company might be attempting to downplay or hide the incident.
Speaking on a Discord channel, a company representative claimed that the security breach occurred in the past and insisted that no data breach had occurred this year.
This statement has done little to assuage the concerns of PandaBuy customers and cybersecurity experts.
This incident is a stark reminder of the ever-present threat of cyberattacks and the importance of robust cybersecurity measures.
Companies, especially those handling vast amounts of consumer data, must prioritize the security of their platforms to protect against such breaches.
For consumers, the breach underscores the need for vigilance and the adoption of best practices for digital security, such as using strong, unique passwords and being cautious of phishing attempts.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
%20(1).webp?w=696&resize=696,0&ssl=1)


.png
)
