Cybersecurity researchers at Cisco Talos have uncovered a large-scale smishing campaign targeting toll road users across the United States.
The campaign, which has been active since October 2024, impersonates toll road payment services, luring unsuspecting victims into revealing their personal and financial information through fraudulent payment requests.
The Scam Unveiled
The smishing campaign revolves around deceptively simple tactics. Targeted individuals receive SMS messages claiming they owe a small toll payment of less than $5.
These messages often warn of steep late fees, compelling recipients to act quickly by visiting a link included in the text.
The fraudsters use typosquatted domains resembling legitimate toll payment websites, displaying state-specific abbreviations like “FL” for Florida or “TX” for Texas to appear authentic.
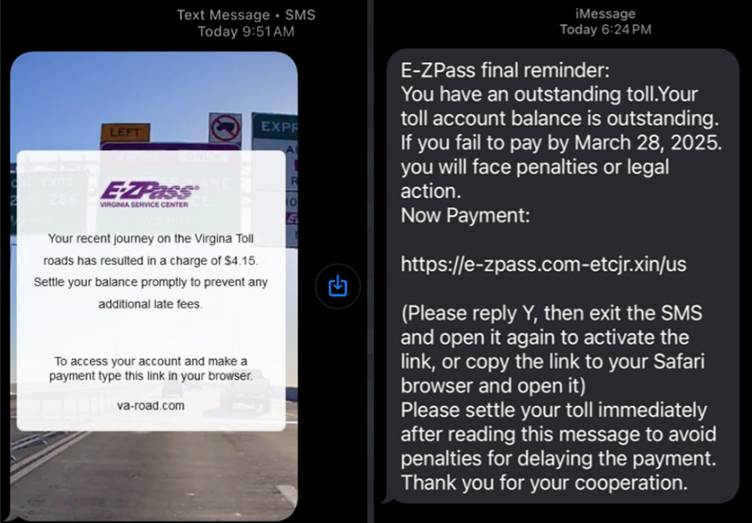
Once victims click the link, they’re directed to a fake webpage that uses logos and branding mimicking official toll services, such as EZPass.
The site prompts users to complete a CAPTCHA verification and enter their name, ZIP code, and other details. Victims are then presented with a fabricated toll bill and a warning of hefty penalties for delayed payments.
Clicking “Proceed Now” transfers individuals to another fake webpage, where they are asked to input sensitive information like their address, phone number, and credit card details – all of which are ultimately stolen by the attackers.
A Deep Web Operation
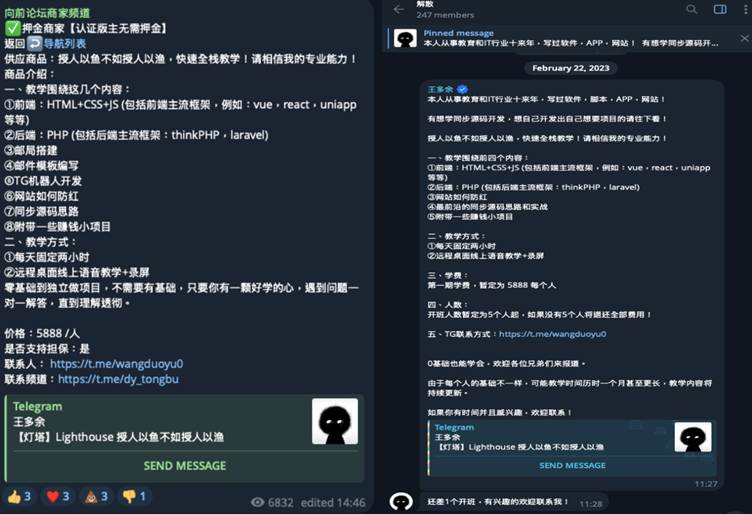
Cisco Talos’ investigation reveals that the smishing campaign is likely driven by financially motivated cybercriminal groups using smishing kits developed by an individual known as “Wang Duo Yu.”
These kits, found in underground Telegram channels and forums, enable threat actors to conduct sophisticated phishing operations targeting toll systems, banks, and postal services.
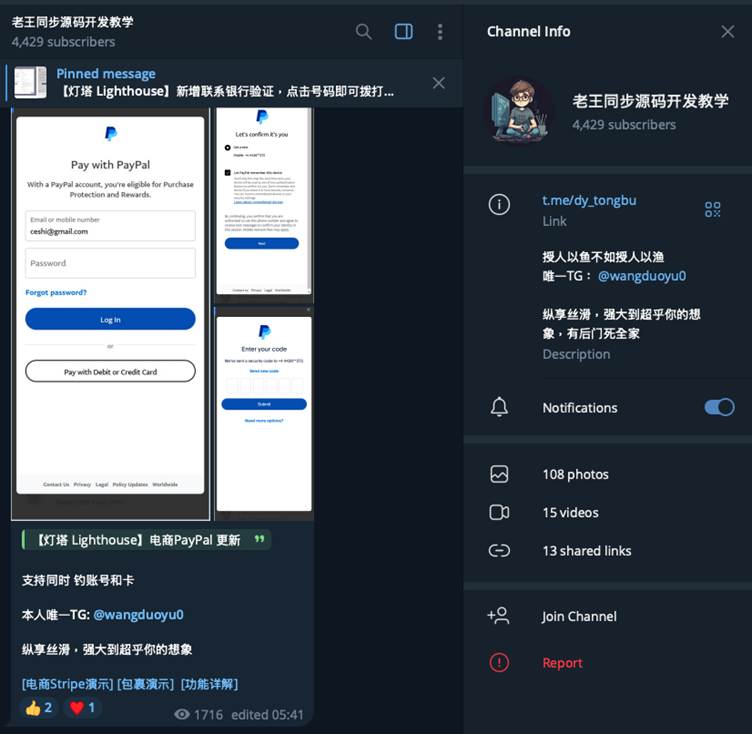
The phishing modules are highly customizable, allowing attacks to scale across multiple states and entities.
Talos further notes that the domains used in this campaign were registered in October and November 2024, with ongoing activity observed as recently as March 2025.
The infrastructure supporting the attacks appears well-maintained, reflecting a high degree of organization among the perpetrators.
Implications and Security Measures
This smishing campaign is a stark reminder of the growing prevalence of SMS phishing schemes and the need for vigilance among users.
Threat actors are leveraging publicly leaked information from large data breaches to tailor their attacks, though there is no definitive evidence linking these campaigns to specific data leaks, such as the 2024 National Public Data breach.
Users are advised to stay cautious when receiving payment requests via SMS and avoid clicking on suspicious links.
Legitimate toll authorities rarely send payment reminders through unsolicited texts. Instead, users should verify outstanding bills directly on the official websites of toll road operators.
Authorities and cybersecurity firms are urging businesses to bolster their defenses against such attacks.
Cisco recommends tools like Secure Endpoint, Secure Firewall, and Umbrella to detect and block malicious activities associated with smishing campaigns.
Multi-factor authentication, network traffic monitoring, and secure internet gateways are among the measures that can safeguard users and organizations from phishing threats.
As cybercriminals continue to refine their tactics, the emergence of toll road-related smishing scams underscores the importance of awareness, robust security measures, and vigilant online behavior.
By educating users and deploying advanced cybersecurity solutions, the risks posed by such campaigns can be minimized, protecting personal and financial information from exploitation.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
