North Korean Hackers Abuse DMARC To Legitimize Their Emails
DMARC is targeted by hackers as this serves to act as a preventative measure against email spoofing and phishing attempts. They compromise DMARC (Domain-based Message...
TA558 Hackers Compromised 320+ Organizations’ FTP & SMTP Servers
TA558, a financially motivated threat actor identified in 2018, is targeting several countries but with utmost priority in Latin America.Over 320 attacks have been...
Beware of Encrypted Phishing Attack With Weaponized SVG Files
Attackers are now leveraging encrypted phishing emails that utilize Scalable Vector Graphics (SVG) files to execute malicious JavaScript code.The phishing campaign begins with an...
Microsoft Two-Step Phishing Campaign Attack LinkedIn Users
The professional and personal online spheres are merging as social media platforms like Facebook, LinkedIn, and WhatsApp are now commonly used for work communication....
5 Major Phishing Campaigns in March 2024
March saw many notable phishing attacks, with criminals using new tactics and approaches to target unsuspecting victims.It is time to explore some of...
Werewolf Hackers Exploiting WinRAR Vulnerability To Deploy RingSpy Backdoor
Active since 2023, the Mysterious Werewolf cluster has shifted targets to the military-industrial complex (MIC) by using phishing emails with a weaponized archive. The archive...
iPhone Users Beware! Darcula Phishing Service Attacking Via iMessage
Phishing allows hackers to exploit human vulnerabilities and trick users into revealing sensitive information and grant unauthorized access.It's an effective social engineering technique...
New Tycoon 2FA Phishing Kit Attacking Microsoft 365 & Gmail Users
Hackers use 2FA (Two-Factor Authentication) phishing kits to overcome the additional security layer provided by 2FA. These kits typically mimic legitimate login pages and prompt...
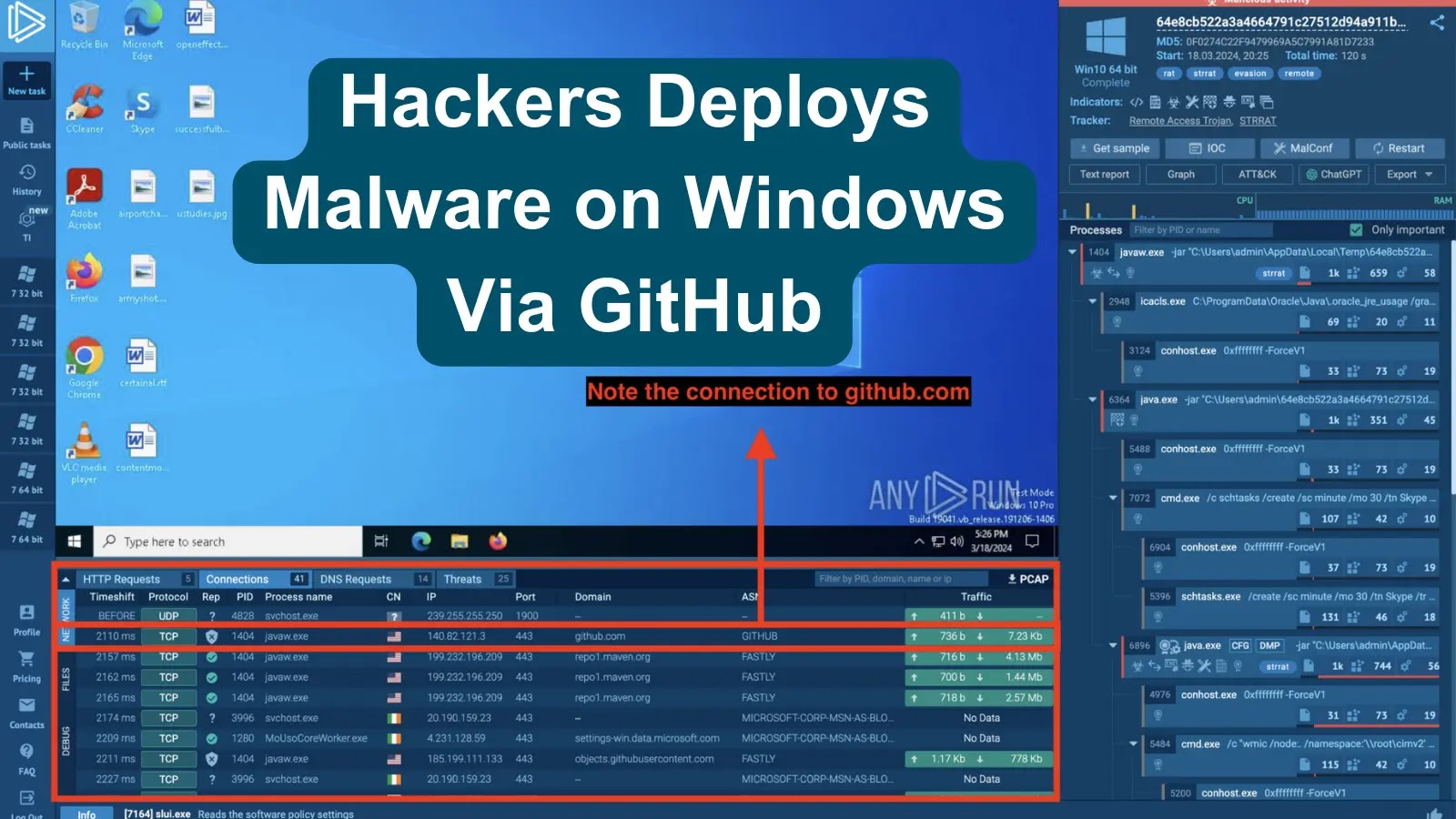
Hackers Deploy STRRAT & VCURMS Malware on Windows Via GitHub
A new phishing campaign targets users with emails containing a button to "verify payment information." Clicking the button triggers the download of a malicious...
Beware! Disguised Adobe Reader Installer That Installs Infostealer Malware
An infostealer disguised as the Adobe Reader installation has been observed. The file is disseminated in PDF format and prompts users to download and run...






.webp)









.webp)
.webp)