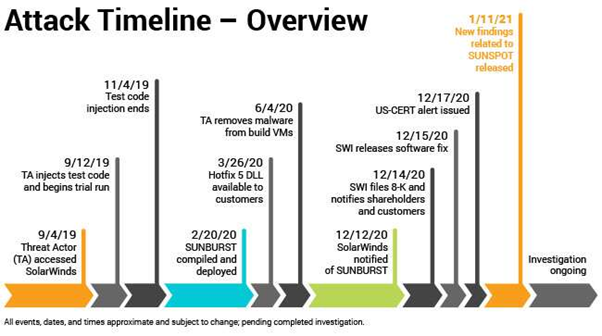
A month after the discovery of the Solorigate hack, investors continue to unearth new facts about the attack, which goes on to show the sophistication and complexity of the attack.
Microsoft’s analysis of the attack reveals that the attackers are highly skilled operators who had put in a lot of time and effort to execute the attack and remain elusive while maintaining persistence.
The attackers appear to be very knowledgeable regarding operations security and performing malicious activity with a minimal footprint.
A link missing in the complicated Solorigate attack chain is the handover from the Solorigate DLL to backdoor to the Cobalt Strike loader.
Cobalt Strike is a legitimate penetration testing tool that is used by threat actors in the post-exploitation tasks and to deploy beacons that enable them to gain continuous remote access.
The attackers have gone to great lengths to separate the Solorigate DLL from the Cobalt Strike loader to avoid detection.
A fully functional Solorigate DLL backdoor was compiled at the end of February 2020 and was distributed to the systems in the end of March 2020, and the Solorigate backdoor code was removed from SolarWinds’ build environment in June 2020.
It is believed that the attackers spent a month or so selecting the victims and preparing unique Cobalt strikes. It is likely that the real hands-on-keyboard activity commenced in early May 2020.
From the Solorigate backdoor to Cobalt Strike implants
Microsoft investigated potential patient-zero machines running the backdoored version of SolarWinds DLL. The process can be explained in the following steps:

Transition from Solorigate backdoor to Cobalt Strike
Step 1: Most of the machines communicate with the initial randomly generated DNS domain avsvmcloud.com but without significant activity
Step 7: The initial DNS network communication was closely followed by network activity on port 443 (HTTPS) to other legit-looking domains (step #7)
Step 2: When the Solorigate backdoor activates for victim profiles, the executing process (usually SolarWinds.BusinessLayerHost.exe) creates two files on disk.
- A VBScript, typically named after existing services or folders to blend into legitimate activities on the machine
- A second-stage DLL implant, a custom Cobalt Strike loader, typically compiled uniquely per machine and written into a legitimate-looking subfolder in %WinDir% (e.g., C:\Windows
Step 3: The attackers made the SolarWinds process create an Image File Execution Options (IFEO) Debugger registry value for the process dllhost.exe
Step 4: This execution triggers a process launch of wscript.exe configured to run the VBScript file
Step 5: The VBScript turn runs rundll32.exe and activates the Cobalt Strike DLL
Step 6: the VBScript removes the previously created IFEO value to clean up any traces of execution
The post from Microsoft goes on to recommend its own products such as Microsoft 365 Defender and Azure Sentinel to mitigate such attacks.
Conclusion
As a note of attack, the attackers behind the Solorigate seem to be very skillful and methodic operators. Microsoft has advised about their defender tool Microsoft 365 Defender advanced hunting or Azure Sentinel queries to search for potential traces of past activity and defend the attacks.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity, and hacking news updates.
Also Read
SolarWinds Hack – Multiple Similarities Found Between Sunburst Backdoor and Turla’s Backdoor
DOJ Says SolarWinds Hackers Accessed 3% of it’s Office 365 Mailboxes
New Malware Discovered in SolarWinds Attack that Used 7-Zip Code to Hide



.png
)
