A new extension for Burp Suite has been released, integrating the powerful secret scanning capabilities of TruffleHog.
This innovative integration aims to enhance the detection of live, exploitable credentials within HTTP traffic, making it a valuable tool for security professionals.
In this article, we will delve into the features, usage, and benefits of the TruffleHog Burp Suite extension.
What is TruffleHog?
TruffleHog is a widely recognized command-line tool designed to find and verify sensitive information in data streams, including Git repositories.
By integrating TruffleHog with Burp Suite, developers, and security professionals can seamlessly identify and exploit critical secrets embedded in web traffic.
Why Integrate TruffleHog with Burp Suite?
The integration was motivated by the surprising prevalence of hardcoded sensitive information, such as AWS credentials, in web applications.
A recent discovery of over 12,000 live secrets in public web traffic underscored the need for a more robust solution to detect these vulnerabilities.
Burp Suite, known for analyzing HTTP traffic, is the perfect platform to leverage TruffleHog’s capabilities.
How to Use the TruffleHog Extension
Installation
Using the TruffleHog Burp Suite extension involves a straightforward two-step process:
- Install TruffleHog Locally: Users must first install TruffleHog on their local machine. Instructions for this step are provided with the extension documentation.
- Install the Extension: The TruffleHog Burp Suite extension can be installed directly from the Burp Suite Extensions Store. Alternatively, users can clone the extension repository and load it manually within Burp Suite. This method requires Python support via a Jython JAR file.
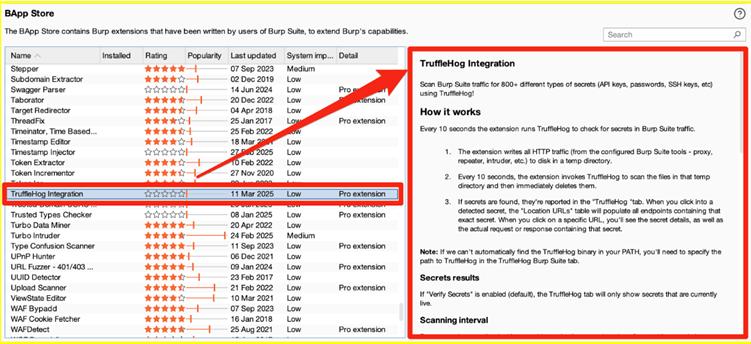
Configuration and Usage
- Secret Verification: The extension is configured by default to verify each detected secret via an HTTP request, ensuring only active and exploitable credentials are reported. Users without internet access can disable this feature for manual review.
- Traffic Scanning: Burp Suite’s default proxy traffic is scanned automatically, with options to include repeater, intruder, and other traffic. There is a slight delay between when a secret appears in the browser and when it is reported by TruffleHog, due to the extension’s design.
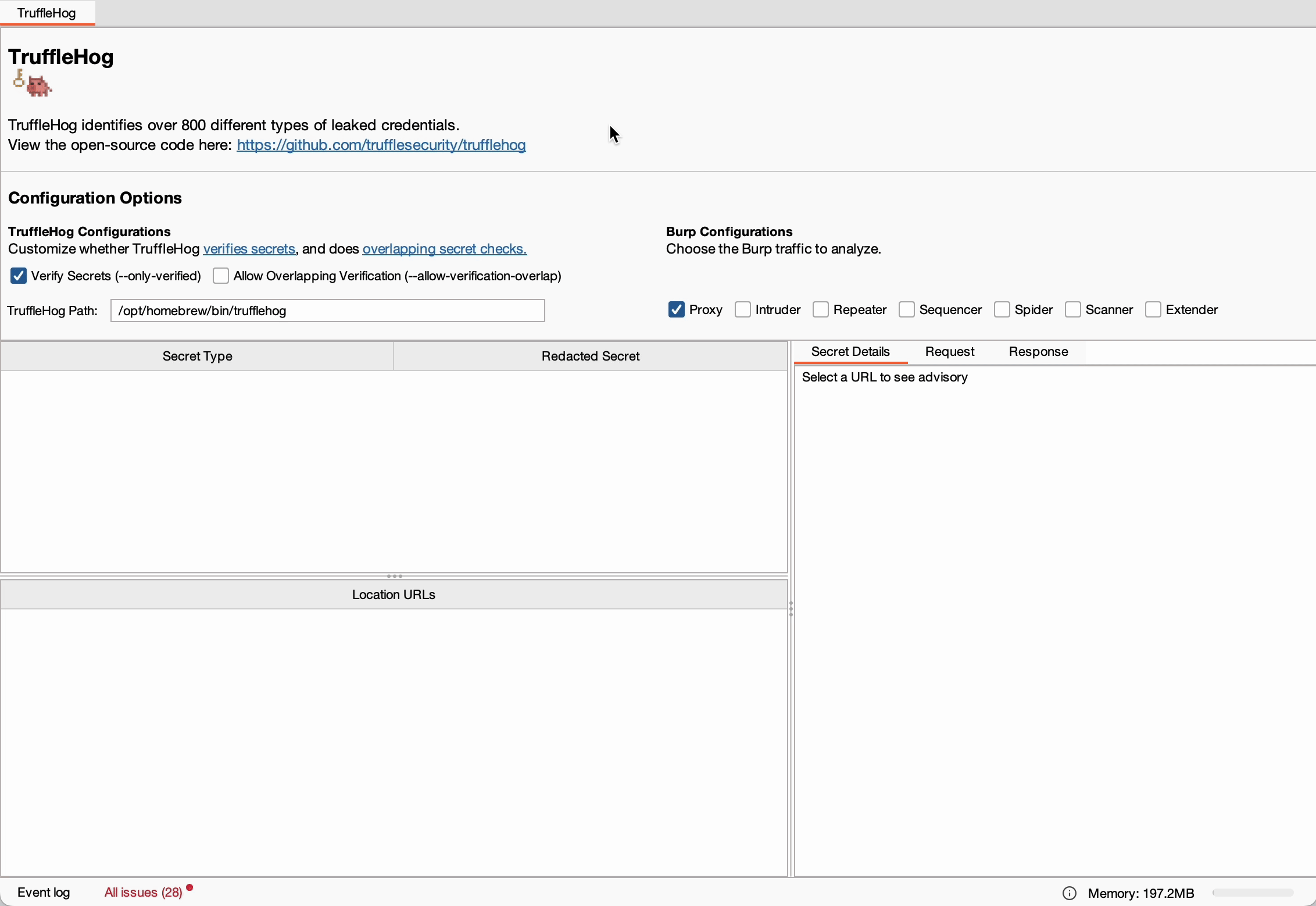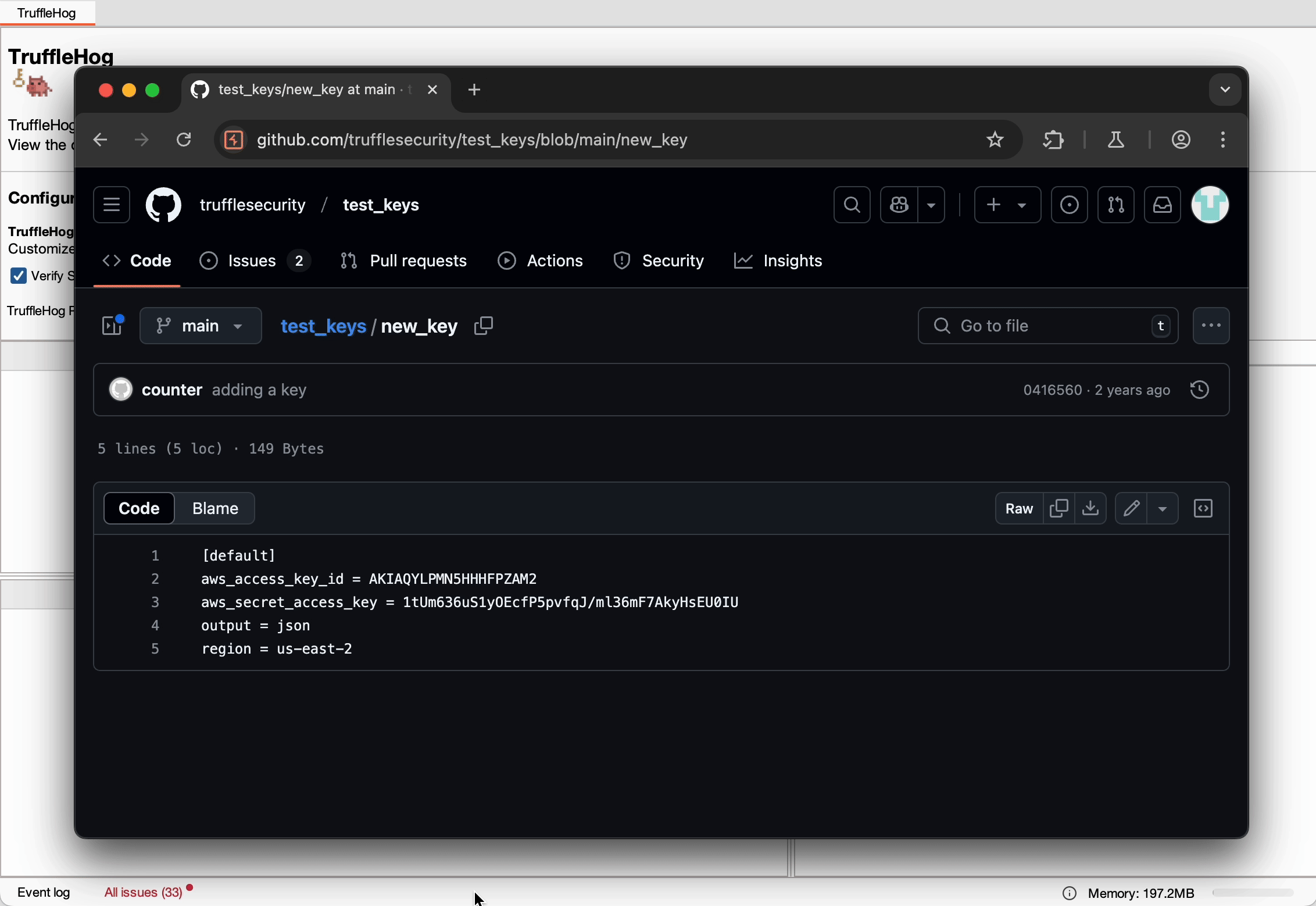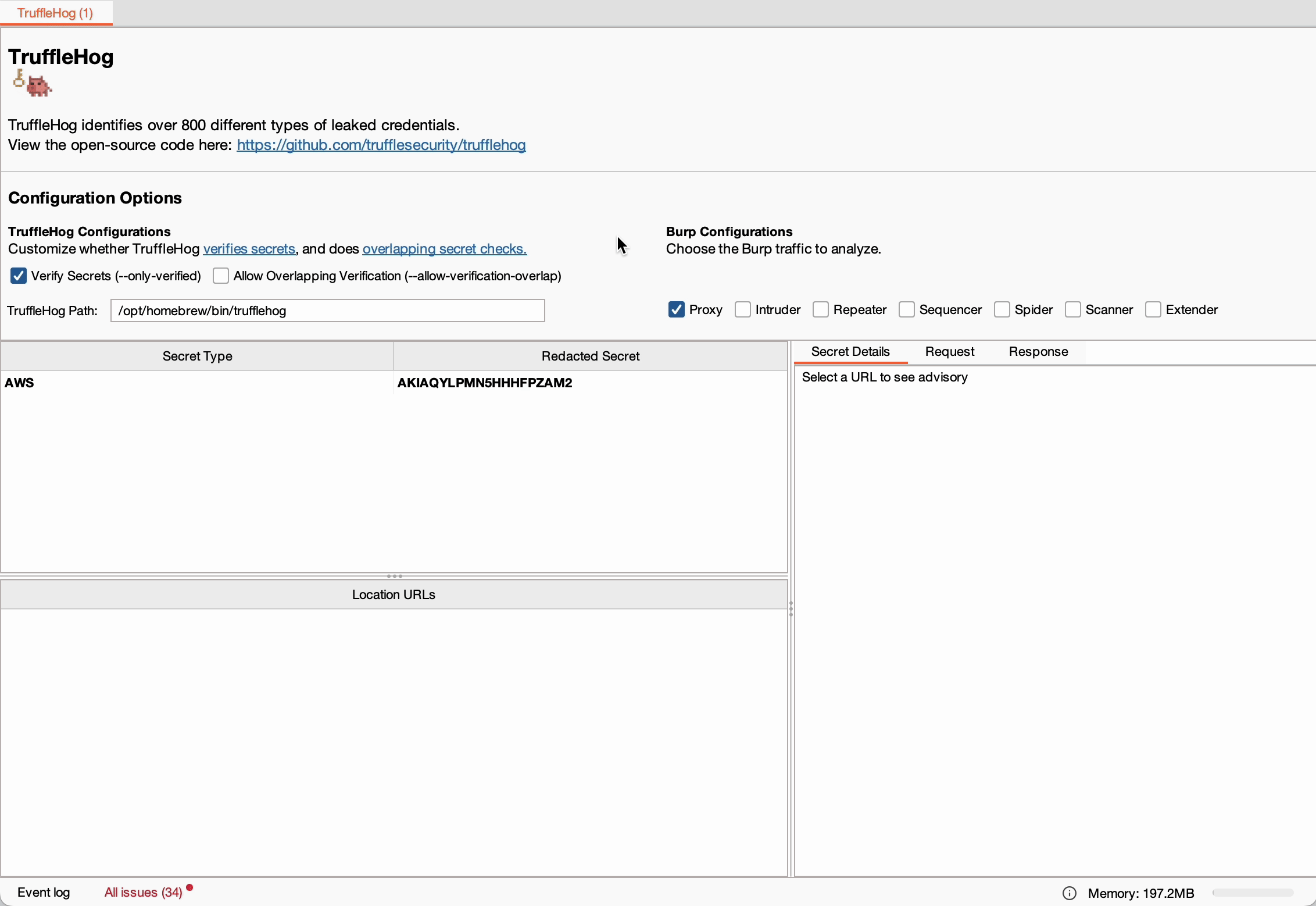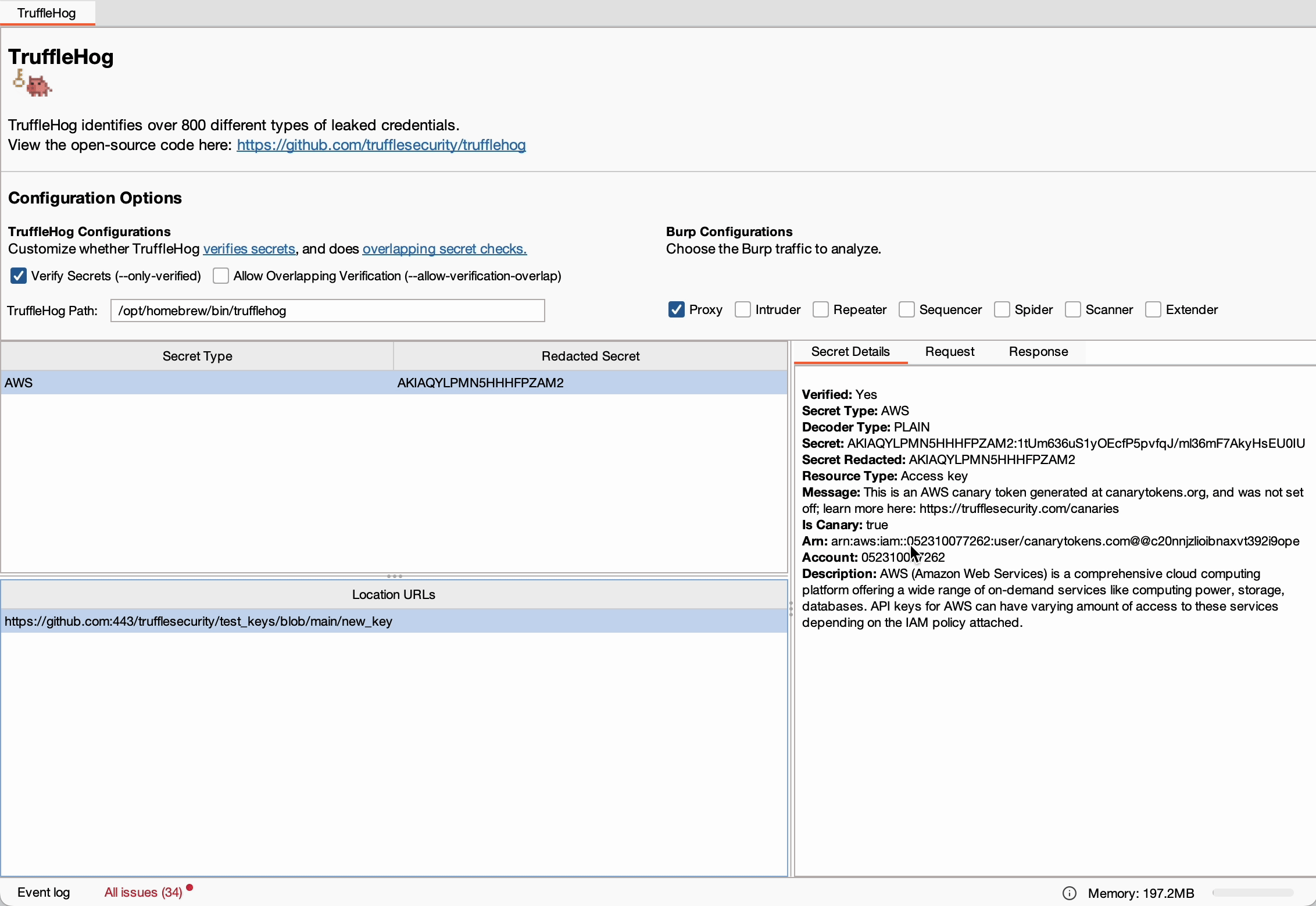
- Result Interpretation: Detected secrets are displayed in the TruffleHog tab, allowing users to click on a secret to view all associated URLs and detailed information about its location in request or response data.
Benefits and Architecture
The TruffleHog Burp Suite extension offers several key benefits:
- Seamless Integration: It fits seamlessly into the Burp Suite workflow, requiring minimal configuration.
- Automatic Updates: Users can take advantage of the latest TruffleHog updates without relying on extension updates.
- Customization: The ability to use custom TruffleHog implementations allows for detecting non-standard secrets.
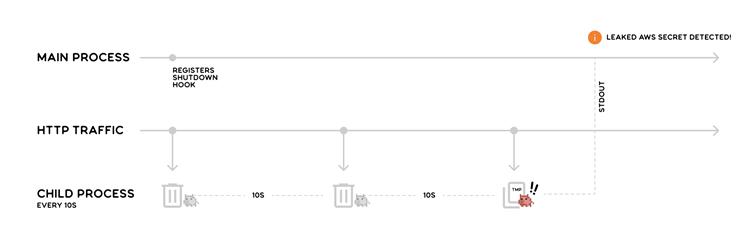
The extension operates by creating a child process that runs TruffleHog on temporary files containing HTTP traffic every ten seconds.
This approach ensures that detected secrets are efficiently reported in the Burp Suite UI without requiring manual intervention.
One notable limitation is the lack of support for scanning WebSocket traffic. This presents an opportunity for future development and could be a rewarding project for those interested.
The release of the TruffleHog Burp Suite extension marks a significant step forward in enhancing web security by providing an accessible tool for detecting and managing sensitive information in HTTP traffic.
By leveraging the strengths of both TruffleHog and Burp Suite, security professionals can now more effectively identify and address potential security vulnerabilities in web applications.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
