Web application security refers to the measures taken to safeguard web applications from potential attacks.
It involves strategies and processes to secure web applications from external threats that could compromise their functionality, safety, and data integrity.
An effective web application security strategy involves identifying possible vulnerabilities, assessing their associated risks, and implementing measures to prevent attacks.
Many businesses rely heavily on web applications for their operations. A security breach could lead to significant financial loss, damage to the company’s reputation, and potential legal repercussions. Therefore, organizations must ensure that their web applications are secure.
Table of Contents
FAQ
Common Vulnerabilities in Web Applications
SQL Injection
Cross-Site Scripting (XSS)
Cross-Site Request Forgery (CSRF)
Insecure Direct Object References (IDOR)
Security Misconfigurations
The Role of Security Frameworks and Standards
OWASP (Open Web Application Security Project)
ISO/IEC 27001
PCI DSS (Payment Card Industry Data Security Standard)
NIST Cybersecurity Framework
CIS Critical Security Controls (CIS CSC)
Best Practices for Web Application Security
FAQ
1.What is the Web application security?
Web application security protects web-based apps and services from vulnerabilities. Security is crucial in today’s digital world, as businesses and consumers use web apps for many purposes. Web applications can be attacked by SQL injection, XSS, CSRF, and more.
Web application security requires procedures and technology to discover, mitigate, and prevent vulnerabilities and attacks. Web application firewalls, software updates and patches, input validation, access controls, and vulnerability monitoring and testing may be used.
Organizations can protect sensitive data, maintain user trust, and reduce financial and reputational risk from security breaches by prioritizing web application security.
2. What is data security in web application?
When sensitive information is kept, processed, or sent within a web application or between the program and its users, data security in web applications refers to the deployment of methods and policies to prevent the information from being accessed, disclosed, altered, or destroyed by unauthorized parties.
User credentials, personal data, financial information, and any other data that must be kept confidential are examples of the types of sensitive information that may be required to be kept confidential.
3. Why do we need web application security?
Today’s digital landscape requires web application security to secure sensitive data, user privacy, and web-based service integrity and availability.
Cyberattacks and data breaches have escalated as more organizations and consumers use web apps. Web applications must be secured against XSS, SQL injection, CSRF, and other threats.
Without strong web application security, hostile actors can steal data, hijack user accounts, disrupt services, or gain unauthorized access to systems.
Thus, web application security policies must be implemented and updated to assure online platforms’ trustworthiness and safeguard enterprises and their users from emerging cyber threats.
4. How a web application is developed?
A functioning and interactive web application is developed using a systematic method that blends technologies and programming languages.
The method usually involves numerous steps. The planning and conceptualization phase defines the project’s goals, requirements, and audience.
The design process then creates the application’s visual and interactive features, including the user interface (UI) and user experience (UX).
After designing the app, developers code its frontend and backend using HTML, CSS, JavaScript, Python, Ruby, or Node.js. Testing is essential for finding and fixing bugs, security vulnerabilities, and performance concerns.
User access is granted after the program is delivered to a web server or cloud platform after testing. Updates and maintenance are needed to meet user needs, security threats, and program improvements.
This method requires collaboration between designers, developers, testers, and project managers to guarantee a successful web application development project.
Common Vulnerabilities in Web Applications
Despite the best efforts of developers and security experts, no web application is entirely immune to security risks.
Several common vulnerabilities often exploited by attackers include SQL Injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), Insecure Direct Object References (IDOR), and Security Misconfigurations.
SQL Injection
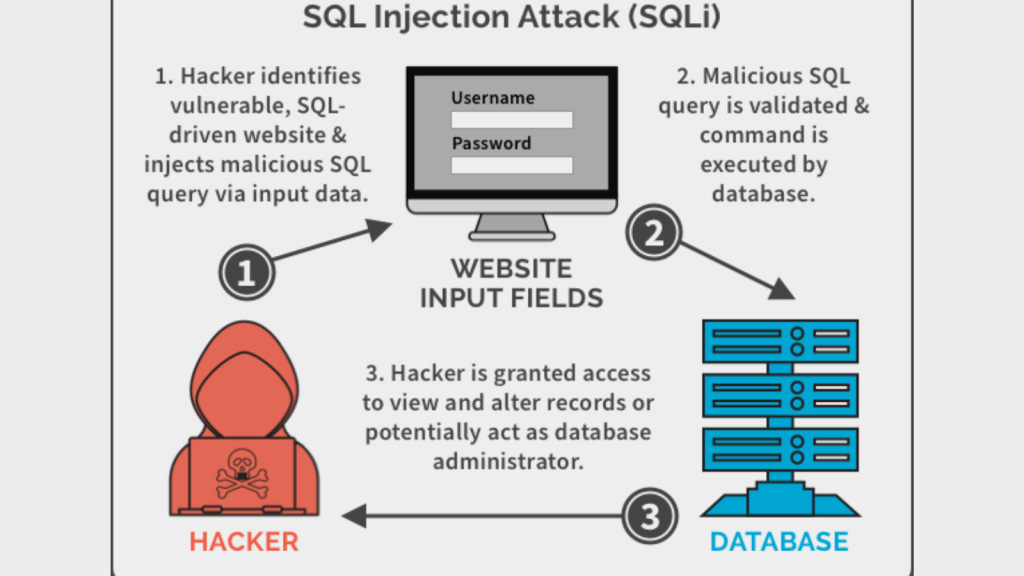
SQL Injection is a web security vulnerability that allows an attacker to interfere with an application’s database queries. It generally occurs when a developer uses unvalidated or unencoded user input within a database query.
An attacker can manipulate the SQL query to view sensitive information, modify the database, or even execute administrative operations on the database.
Cross-Site Scripting (XSS)
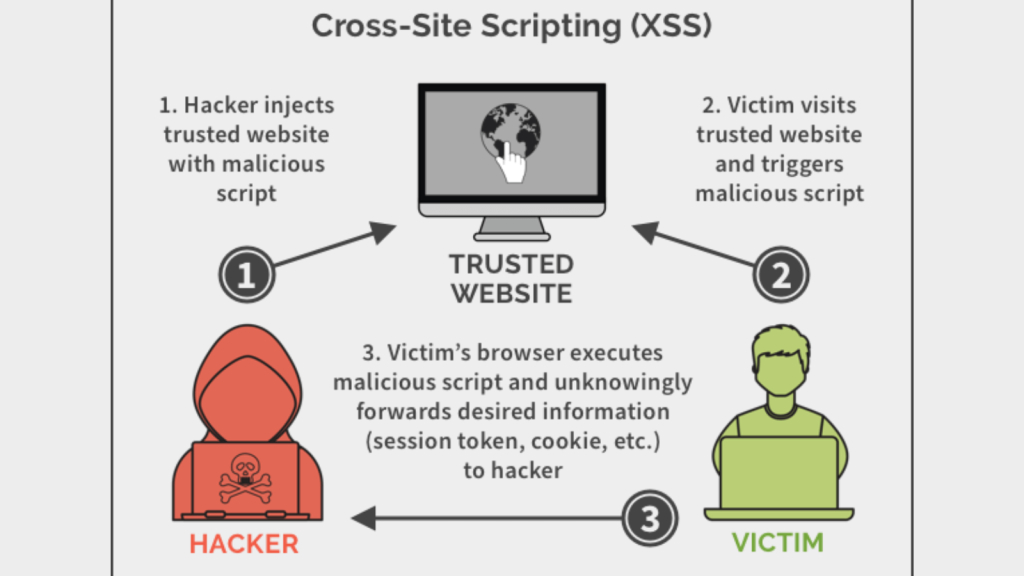
Cross-site scripting (XSS) occurs when an attacker injects malicious scripts into web pages viewed by other users.
The attacker uses these scripts to steal sensitive information like session cookies, enabling them to impersonate the victim and perform actions on their behalf.
The consequences of a successful XSS attack range from minor annoyance to significant security breaches.
Cross-Site Request Forgery (CSRF)

Cross-Site Request Forgery (CSRF) is an attack that tricks the victim into submitting a malicious request. This is achieved by including a link or script in a webpage that accesses a site to which the user is authenticated.
A successful CSRF attack can lead to unauthorized changes in data, such as email addresses, passwords, and more.
Insecure Direct Object References (IDOR)
Insecure Direct Object References (IDOR) occur when a developer exposes a reference to an internal implementation object, such as a file, directory, or database key.
Attorneys can manipulate these references to access unauthorized data without an access control check or other protection.
Security Misconfigurations
Security Misconfigurations are the most commonly seen issue. This typically happens when an application or its platform is configured insecurely.
An attacker can exploit these misconfigurations to access unauthorized information or functionality.
The Role of Security Frameworks and Standards
Security frameworks and standards are fundamental in ensuring web application security.
By providing a systematic approach to managing security risks, these guidelines serve as roadmaps for organizations aiming to fortify their cybersecurity posture.
Adherence to these frameworks and standards allows organizations to tackle various security issues and ensure their web applications’ confidentiality, integrity, and availability.
OWASP (Open Web Application Security Project)

OWASP is an open community that enables organizations to develop, purchase, and maintain applications and APIs that can withstand security threats.
One of their most unique resources is the OWASP Top 10, a standard awareness document for developers and web application security.
It represents a broad consensus about web applications’ most critical security risks. Using the OWASP Top 10 guide, developers can prioritize security measures, focus on the most significant threats, and significantly improve their web application’s security.
ISO/IEC 27001
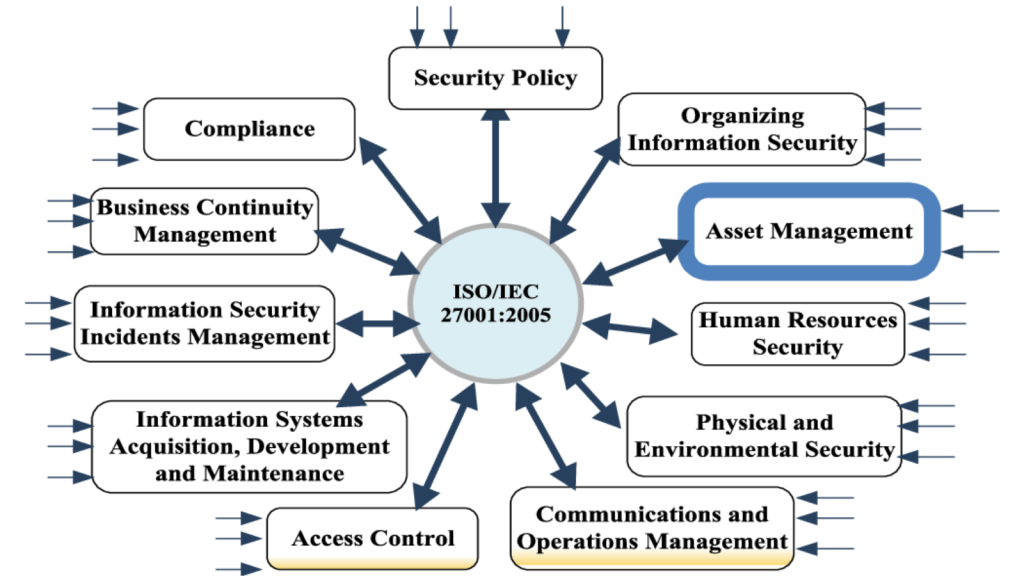
This is a globally recognized standard for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS).
This standard helps organizations consistently and cost-effectively manage their security practices in one place.
It covers various security controls, from risk assessment to access control to incident management.
Compliance with ISO/IEC 27001 demonstrates that an organization is committed to following the best information security practices.
PCI DSS (Payment Card Industry Data Security Standard)
If your web application involves processing, storing, or transmitting cardholder data, adhering to the PCI DSS is mandatory.
This standard aims to secure credit card transactions against data theft and fraud.
It comprises 12 requirements, including regular security audits, secure networks and systems, access control measures, and more.
Organizations can protect sensitive cardholder data and build customers’ trust by complying with PCI DSS.
NIST Cybersecurity Framework
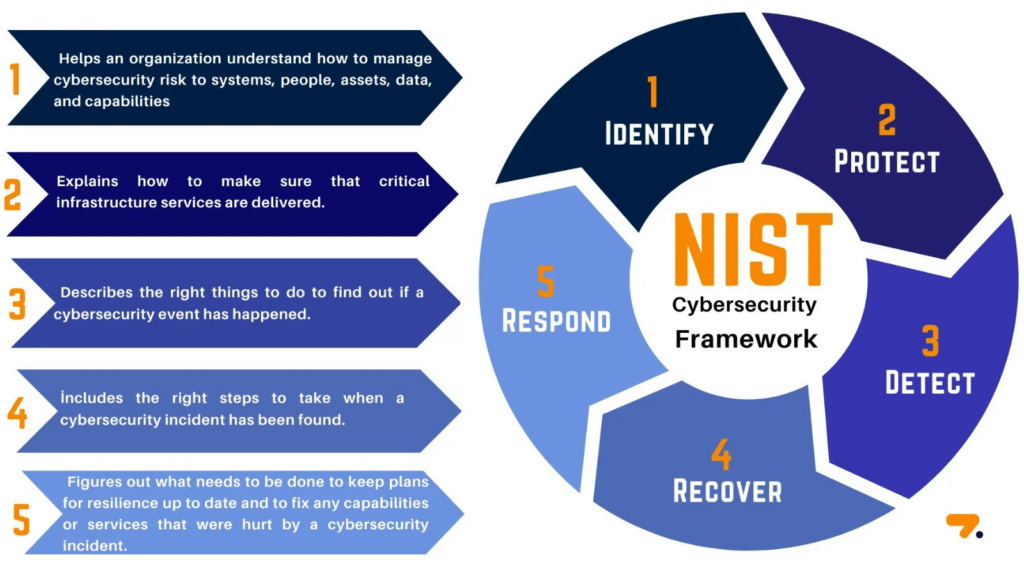
Developed by the National Institute of Standards and Technology (NIST), this voluntary framework provides a policy for managing cybersecurity risks.
It comprises standards, guidelines, and best practices to manage cybersecurity risk cost-effectively.
The framework core consists of five main functions: Identity, Protect, Detect, Respond, and Recover.
The NIST framework is widely adopted across various industries due to its flexibility and comprehensiveness.
CIS Critical Security Controls (CIS CSC)
Developed by the Center for Internet Security, CIS CSC is a set of 20 actions designed to provide a roadmap for organizations to enhance their cybersecurity posture.
These controls are a series of well-vetted and supported security actions that, when implemented, can prevent the most pervasive and dangerous cyber attacks.
Best Practices for Web Application Security
The following best practices can help you secure web applications and reduce business risks.
Secure Coding Practices
Secure coding is the practice of writing code for systems, applications, and software in a way that guards against security vulnerabilities.
It involves a series of principles designed to eliminate categories of bugs that could lead to system vulnerabilities.
Secure coding helps protect a system from potential threats by identifying and eliminating software bugs or flaws that cybercriminals could exploit.
Safe coding practices have become more crucial in the current technology landscape. Security is often compromised as developers are pressured to deliver fast and efficient software.
However, developers must understand that secure coding practices can improve their code’s security, quality, and maintainability.
It can significantly reduce the time and cost associated with fixing bugs and vulnerabilities in the later stages of the software development life cycle.
User Input Validation and Sanitization
User input validation and sanitization are critical aspects of web application security. They check and clean user input to prevent security vulnerabilities such as SQL injection, cross-site scripting, and remote code execution.
Enhanced user input validation and sanitization techniques include using allow-lists instead of deny-lists, secure APIs, and context-sensitive output encoding.
These techniques can help prevent common web application security vulnerabilities and protect the application from potential attacks.
Automated Security Testing
Automation plays a crucial role in security testing by automating repetitive tasks, reducing human error, and speeding up the testing process.
Automated security testing tools can scan for known vulnerabilities, execute test cases, and generate reports, freeing up security teams to focus on more complex tasks.
Automation can also help businesses keep up with the rapid pace of software development and deployment.
As new code is committed, automated tools can quickly test for vulnerabilities, ensuring security is integrated throughout the software development lifecycle.
This is particularly important in an Agile or DevOps environment, where speed and efficiency are critical.
Patching and Updating Software
In a DevOps environment, continuous integration and deployment are the norms.
This means code is frequently updated and deployed, which can create potential security vulnerabilities.
Therefore, regular patching and updating are crucial to maintaining the application’s security.
Patching involves updating the software to fix security vulnerabilities. Regular patch management ensures that the application is protected against known threats.
It’s also essential to keep all software components, including third-party libraries and frameworks, up-to-date.
Data Encryption and Secure Data Transmission
Data encryption is the process of converting data into a format that is unreadable to unauthorized users. It’s essential to web application security as it protects sensitive data from cybercriminals’ access.
Secure data transmission with HTTPS is also critical for web application security. HTTPS, or Hypertext Transfer Protocol Secure, is an internet communication protocol that protects the integrity and confidentiality of data between the user’s computer and the site.
It ensures that data transmitted between the user and the web application is encrypted and secure.
Conclusion
In conclusion, understanding and implementing web application security best practices is imperative for businesses in today’s digital age.
Secure coding practices, automation in security testing, AI in WAFs, regular patching and updating, enhanced input validation and sanitization, data encryption, and secure transmission with HTTPS are all critical aspects of web application security that businesses must prioritize.
Remember, the security of your web application is not just about protecting your business; it’s also about safeguarding your customers’ trust and loyalty.



.png
)
