RCS expanded as Rich Communications Services is the next generation SMS protocol aimed to replace the SMS and MMS services. It was taken over by GSM Association in the year February 2008.
Starting from April 2018 Google started integrating RCS with its instant messaging mobile app Google Allo. RCS is the IP-based messaging service based on SIP and HTTP to provide various services such as group chats, video calls, file transfers and more.
RCS Hacking Attacks
According to the Security Research Labs report with some implementations RCS functionality not properly protected and it allows a range of different hacking attacks.
The improper implementation of RCS functionality in many networks let hackers gain complete control over the user accounts by stealing RCS configuration files that include SIP and HTTP credentials.
The implementation lack in certificate and domain validation which allows an attacker to intercept and manipulate communication in the middle and they also failed to validate user identity, which allows caller ID spoofing.
Following are the RCS hacking attacks possible with some implementations
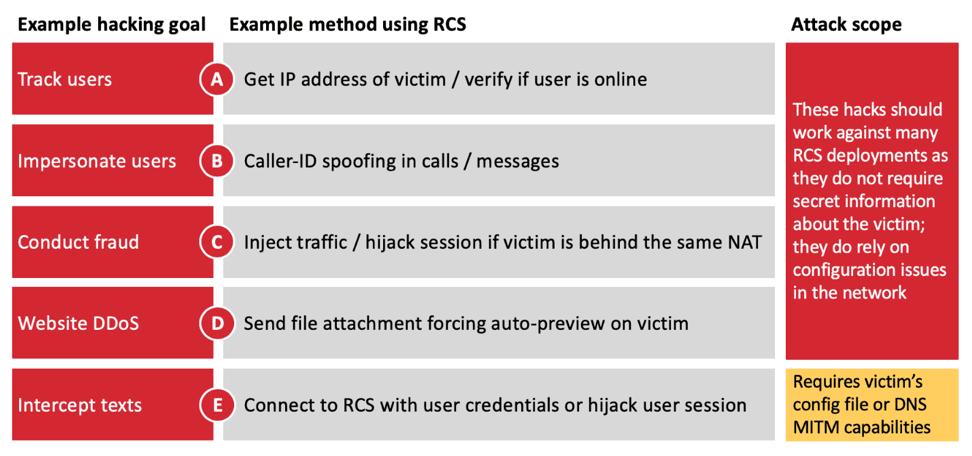
These vulnerabilities can be exploited by a remote or local attacker to intercept an OTP message and to host fraudulent transactions and to take over your online accounts.
An attacker can also launch a MITM attack to intercept and manipulate the user communications with some deployments that failed to validate identity.
SRLabs researchers said that the “attacks make current RCS deployments as vulnerable to hacking as legacy mobile technologies, such as 2G and SS7.”
According to GSMA, 310 million active users already using RCS services.it currently launched by 84 operators worldwide and expected to be launched by another 27 operators in the first quarter of 2020.
It is currently supported only with the Android device if the RCS message received in a device or network that doesn’t support then it will be a regular text message.
Rich Communication Services allows advertisers to send interactive & personalized messages with full interactive functions without any additional apps.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.
Also Read
861 Million SIM cards in 29 Countries are Vulnerable to Simjacker Attacks
Simjacker Vulnerability – Attackers take Control Over Mobile Phones via an SMS Message



.png
)
