Over 1 million payment card records that stolen from south Korea sold on the dark web market for the past few months and the price fixed approximately $24.
Cybercriminals posted the stolen records in Dark web since May 2019, and these stolen payment card data have been obtained from breach of a parent company that operates several different businesses.
Stolen data’s are South Korean-issued CP records, and the data believed to be leaked from point-of-sale (POS) integrator breach, where attackers possibly stole many merchants data.
Cyber attacks on E-commerce business are continuously growing in APAC, especially in South Korea, but the exact compromised point of purchase (CPP) remains unclear.
Based on the research report, 42,000 compromised South Korean-issued CP records posted for sale in the dark web in May 2019, 230,000 records in, June 2019 and 890,000 records were posted in the dark web in July month alone.
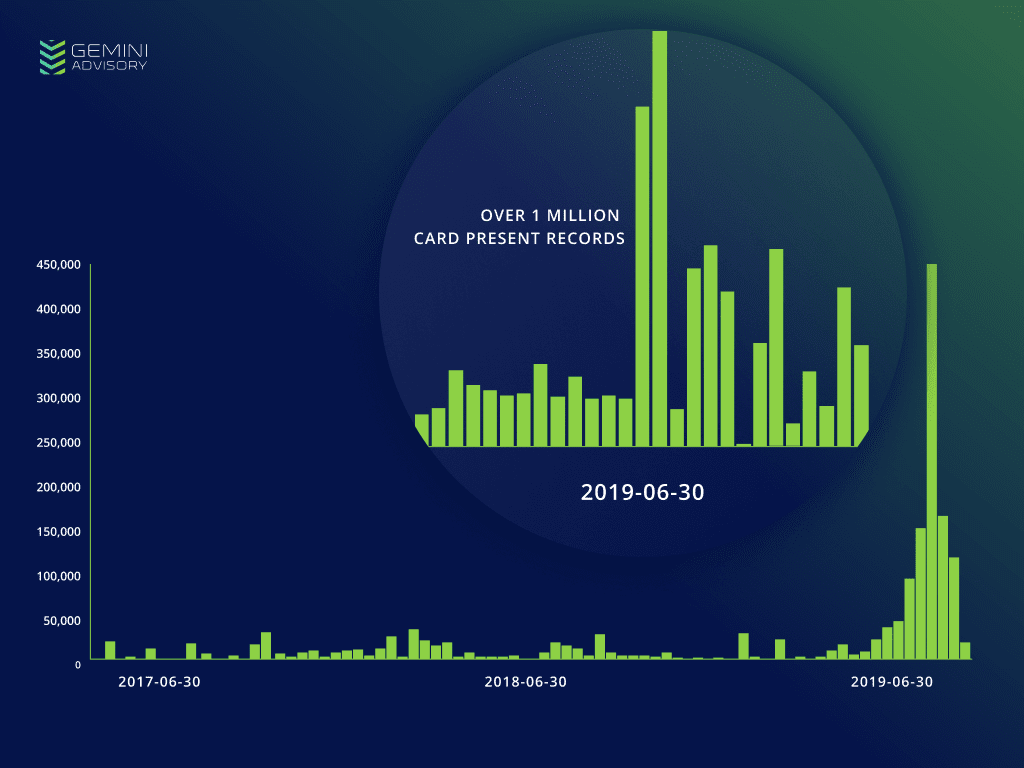
According to Gemini advisory research, This spike currently consists of over 1 million compromised South Korea-issued CP records posted for sale in the dark web since May 29, 2019.
“Among these records, 3.7% of card records issued by the US. One of the most affected US financial institutions was a credit union that primarily serves the US Air Force; the Air Force maintains multiple air bases in South Korea.”
Card records posted on the dark web mostly belong to US cardholders since 1 million U.S visitors had been visited South Korea in the past 12 months.
Cybercriminals charging $40 for single payment card data and the price is higher than the median price of South Korean CP records across the dark web overall, which is approximately $24 in last year.
The researcher believes that card data was obtained from a POS integrator breach, if threat actor gained access to a single integrator service then they possibly gain access the individual POS devices that issued by integrator service.
Eventually, The threat actor would then have access to payment data from multiple sources, accounting for the lack of a common merchant among the compromised payment card.
you can read the 10 Important Components of PCI Compliance Checklist for Protecting the Customers Payment Card Data.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.



.png
)
