Cybersecurity researchers have discovered that multiple state-sponsored threat actors have been exploiting an eight-year-old vulnerability in Windows shortcut files.
This security flaw, identified as ZDI-CAN-25373, allows malicious actors to embed hidden commands within .lnk files, which can execute when opened, potentially compromising sensitive data and systems.
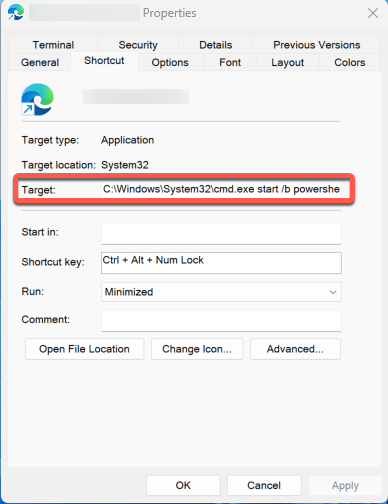
The vulnerability in question exploits how Windows displays shortcut files, often used to launch applications or open files.
By embedding command line arguments in the .lnk files, attackers can execute malicious payloads without alerting the user. Despite being identified years ago, this flaw has not been patched by Microsoft, leaving users at risk.
State-Sponsored Actors Involved
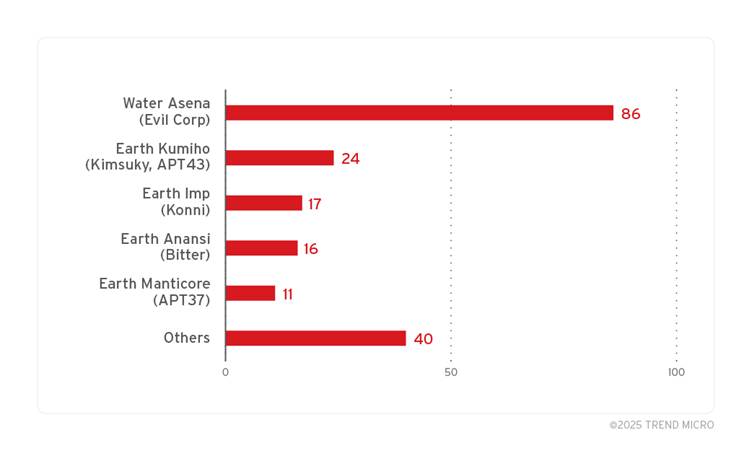
The exploitation of ZDI-CAN-25373 has been linked to at least 11 state-sponsored groups from countries including North Korea, Iran, Russia, and China, as per a report by Trend Micro.
These advanced persistent threat (APT) groups have used the vulnerability to target organizations across various sectors, including government, finance, telecommunications, military, and energy.
The widespread use of this exploit underscores the increasing sophistication of state-sponsored cyber threats.
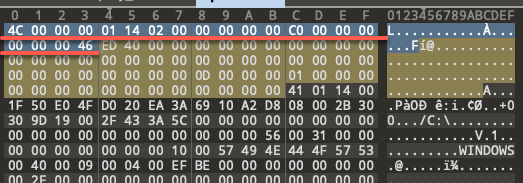
Threat actors have cleverly manipulated .lnk files by padding the COMMAND_LINE_ARGUMENTS structure with whitespace characters, making it difficult for users to detect malicious content through normal Windows UI inspections.
This UI misrepresentation flaw, classified as CWE-451, prevents users from seeing critical information about the commands executed by the .lnk file, highlighting a broader issue of UI vulnerabilities that obscure security-critical information.
The impact of this vulnerability is substantial. With no patch available, organizations must rely on vigilance and security measures to prevent exploitation.
Affected sectors are advised to scan for suspicious .lnk files and ensure comprehensive endpoint and network protection.
The lack of a security patch leaves these organizations vulnerable to data theft and cyber espionage, which are the primary motivations behind these attacks.
Global Reach
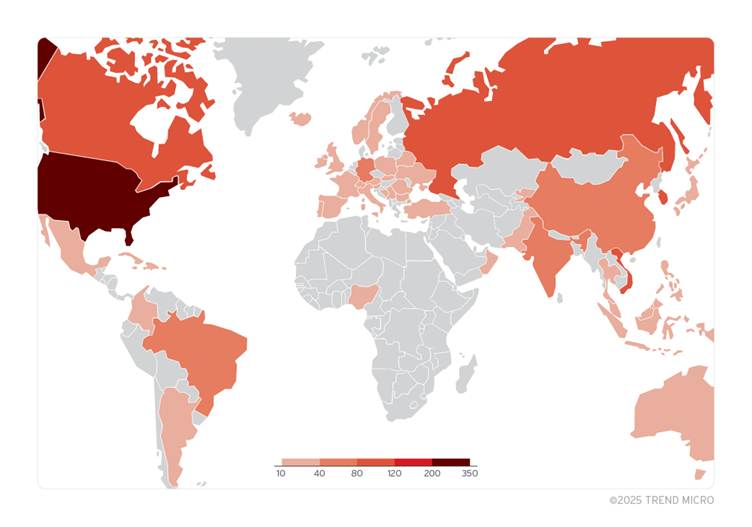
Victimology data indicates that while most samples were submitted from North America, the exploitation affects organizations across North America, Europe, Asia, South America, Africa, and Australia.
This global reach underscores the need for a coordinated response to mitigate this threat.
As geopolitical tensions escalate, the exploitation of vulnerabilities like ZDI-CAN-25373 will likely become more prevalent.
State-sponsored threat actors continue to refine their tactics, often leveraging zero-day exploits to gain strategic advantages.
The absence of a security patch for this eight-year-old vulnerability highlights the importance of proactive cybersecurity strategies for organizations to protect against evolving threats.
Ensuring robust security measures, monitoring suspicious activities, and educating users about potential risks are critical steps in mitigating these sophisticated attacks.
Recommendations for Organizations
- Monitor for Suspicious Files: Regularly scan networks for .lnk files with unusual characteristics.
- Implement Comprehensive Security Measures: Use antivirus software and intrusion detection systems to identify and block malicious activity.
- Educate Users: Inform users about the risks of opening unknown or suspicious .lnk files.
- Deploy Incident Response Plans: Be prepared to respond quickly in case of a detected attack.
The ongoing exploitation of the ZDI-CAN-25373 vulnerability by state-sponsored actors underscores the urgent need for enhanced cybersecurity vigilance globally.
As threats evolve, organizations must adapt by leveraging advanced security tools and strategies to safeguard against these sophisticated attacks.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
