Scammers use sophisticated AI technology to impersonate tech giants like Google, aiming to take over unsuspecting users’ Gmail accounts.
A recent incident highlights these fraudsters’ cunning tactics, underscoring the need for heightened vigilance.
The Initial Contact: A Suspicious Notification
The trouble began with an unexpected notification. The user received a prompt to approve a Gmail account recovery attempt originating from the United States. Wisely, the request was denied.
However, just 40 minutes later, a missed call appeared on the user’s phone, displaying a caller ID of “Google Sydney.” Although initially dismissed, this was just the beginning of a calculated scam attempt.
Analyse Any Suspicious Links Using ANY.RUN’s New Safe Browsing Tool: Try for Free
The Follow-Up: A Deceptive Call
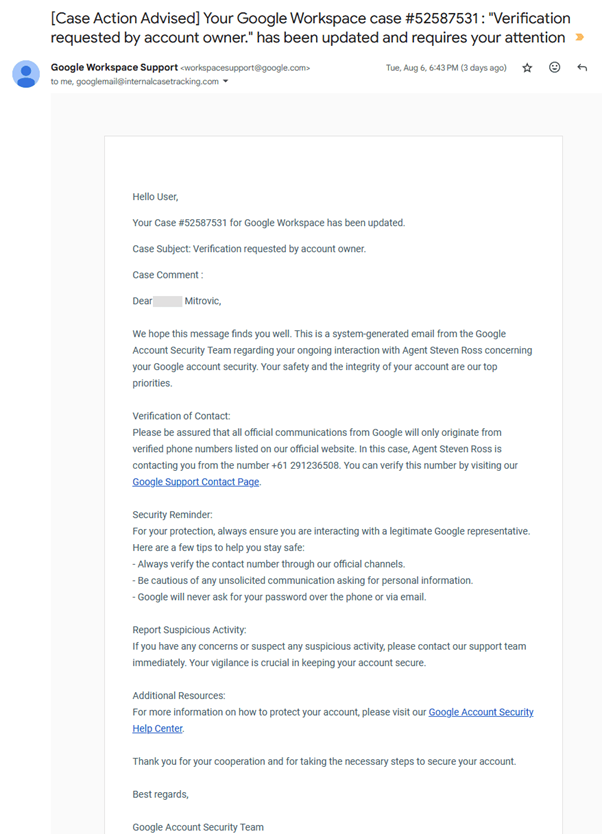
According to the Sam Mitrovic blog report, exactly one week later, another recovery notification from the United States arrived, followed by a call from an Australian number. This time, the user answered.
On the line was a polite and professional American voice claiming to be from Google, warning of suspicious activity on the account. The caller inquired about recent logins from Germany and claimed that account data had been downloaded over the past week.
While speaking, the user searched for the phone number online and found it linked to official Google documentation. Despite this, awareness of number spoofing kept suspicions alive.
When asked to send an email, the caller complied, and an email, seemingly from a Google domain, arrived shortly after.
Unmasking the Deception: AI and Email Spoofing
Despite appearances, several red flags emerged. The email’s “To” field contained an address cleverly disguised as GoogleMail at InternalCaseTracking dot com—a non-Google domain.
Additionally, the caller’s voice exhibited uncanny precision in pronunciation and spacing, suggesting AI generated it.
Realizing this could be an AI-driven scam, the user hung up and investigated further. At home, they checked recent sign-in activity and found no unauthorized access.
Examining email headers revealed that Salesforce CRM was used to spoof the sender’s address over Gmail servers.
This incident is a stark reminder of the lengths scammers will go to deceive their targets. Here are some key takeaways to protect yourself:
- Verify Notifications: Always scrutinize unexpected account recovery notifications. If you didn’t initiate them, it’s likely a scam.
- Be Skeptical of Calls: Google typically doesn’t call users without a Google Business Profile. Be wary of unsolicited calls claiming to be from tech companies.
- Check Email Domains: Legitimate emails from Google will not use non-Google domains in their addresses.
- Inspect Email Headers: Look for inconsistencies that might indicate spoofing.
- Research Caller Information: Conduct reverse phone number searches to see if others have reported similar scam attempts.
Despite numerous red flags, such scams can appear convincing enough to trick many people.
By staying informed and cautious, you can protect yourself from falling victim to these sophisticated schemes.
While technology continues to advance and offer incredible benefits, it also provides new tools for scammers.
Awareness and vigilance are your best defenses against these evolving threats. Stay informed and protect your digital life from those who seek to exploit it for malicious gain.
How to Choose an ultimate Managed SIEM solution for Your Security Team -> Download Free Guide(PDF)



.png
)
