A 20-year-old U.S. Army soldier, Cameron John Wagenius, has been arrested and indicted by federal authorities for allegedly selling confidential customer call records stolen from major telecommunications companies AT&T and Verizon.
Known online as “Kiberphant0m,” Wagenius was apprehended near an Army base in Fort Hood, Texas, on December 20. He faces two criminal counts of unlawfully transferring sensitive phone records.

Cybercrime Allegations and Shocking Ties
Wagenius, who served as a communications specialist in the U.S. Army and was recently stationed in South Korea, is accused of using his technical expertise to orchestrate a series of cybercrimes.
The indictment links him to the sale and leakage of sensitive data from at least 15 telecommunications companies. These records allegedly included call logs belonging to high-profile individuals, such as government officials.
According to Grebs On Security, the investigation gained traction in November 2024 after cybersecurity journalist Brian Krebs identified Wagenius as a potential suspect.
The trail of evidence, found in Telegram messages and hacker forums like BreachForums, pointed to his involvement in various criminal activities, including SIM-swapping services and distributed denial-of-service (DDoS) attacks.
Wagenius reportedly collaborated with Canadian cybercriminal Connor Riley Moucka, also known as “Judische,” who was arrested in October for extorting companies and stealing data from cloud service provider Snowflake.
Moucka had entrusted Kiberphant0m to sell stolen information, including data from AT&T and Verizon customers, as well as offering access to U.S. defense contractor systems.
After Moucka’s arrest, Kiberphant0m escalated his activities, posting AT&T call logs allegedly belonging to President-elect Donald Trump and Vice President Kamala Harris, further threatening to leak additional government call records.
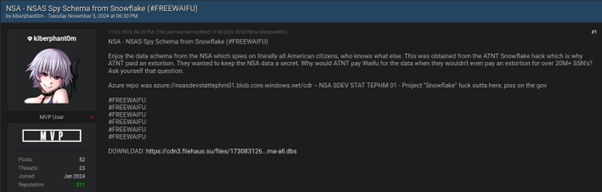
On November 5, he offered Verizon push-to-talk (PTT) call logs — a service frequently used by U.S. government agencies and emergency responders.
In his final online activities, Kiberphant0m claimed to have stolen data from the National Security Agency (NSA) and advertised compromised credentials of a U.S. defense contractor.
Wagenius’ digital footprint, including Facebook photos showing him in uniform, further linked his real-world identity to his online persona.
Cybersecurity analyst Allison Nixon, from Unit 221B, played a key role in uncovering Wagenius’ identity.
She highlighted the unprecedented speed of law enforcement response, stating it was the fastest resolution to a U.S. federal cyber case in her experience.
Nixon also warned other young cyber criminals of the severe consequences of engaging in illegal activities.“This should serve as a wake-up call,” Nixon said. “Law enforcement is getting better and faster at unmasking cybercriminals. It’s not worth the risk.”
The case has been transferred to the U.S. District Court for the Western District of Washington in Seattle, where Wagenius will face trial.
If convicted, this case will underscore the growing sophistication of law enforcement in tackling cybercrime and the risks posed by insiders with access to sensitive systems.
Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free



.png
)
