A new wave of cybercrime is surfacing as hackers exploit compromised emails and digital advertising platforms to create a thriving underground economy.
This illegal marketplace, primarily hosted on the dark web, trades in aged and pre-verified accounts, offering tech-savvy criminals tools to bypass security mechanisms and perpetrate malicious activity.
The Illicit Trade of Verified Accounts
Following a detailed investigation, researchers uncovered over 100 newly registered domains in December 2024, predominantly marketing pre-verified and aged accounts for platforms such as Google Ads, email providers, and social media networks.
These accounts, often obtained via phishing scams, hacking, or other nefarious means, are highly sought after for their ability to evade account verification processes and utilize the inherent trust associated with aged profiles.
While some purchasers seek these accounts for benign uses, such as targeting specific regions or enhancing social media marketing, many turn them into tools of fraud, spam, and disinformation dissemination.
These activities underline the new challenges posed by these underground marketplaces in an increasingly interconnected digital world.
Notable Domains in the Illicit Ecosystem
Several domains have been identified as key players in this ecosystem, offering everything from cloud service accounts to social media pages.
These websites claim to provide “pre-verified” and “aged” accounts to buyers, with promises of complete control over the purchased accounts.
Cloud and Advertising Accounts for Sale
- Topcloudacc[.]com
- Offers accounts for platforms like AWS, Google Ads, and Oracle Cloud.
- Website Title: “Buy AWS Account | Best 32-vCPU & Credit Account – 2025″
- Acctrusted[.]com
- Claims to specialize in cloud services, including AWS, Azure, and DigitalOcean accounts.
- Website Title: “Buy AWS Accounts | Best Vcpu & Credit Account For Sale 2024″
- Buybhwaccounts[.]xyz
- Markets ads accounts and cloud accounts alongside BHW profiles.
- Website Title: “Buy BHW Accounts – BHW Accounts For Sale – buybhwaccounts[.]xyz”
Social Media and Email Accounts
- Regularpva[.]com
- Sells social media and dating accounts, including Facebook, Instagram, Gmail, and Yahoo.
- Website Title: “Buy Social Media Accounts – Social Media Pages for Sale – SecurePVA”
- Discordarena[.]com
- Redirects from other domains and sells “premium aged Discord accounts.”
- Redditaccsbuy[.]com
- Specializes in aged and verified Reddit accounts with built-up karma.
- Website Title: “Reddit Accounts with Karma for Sale”
The investigation reveals a troubling development in the sale of aged Google Ads accounts. Research shows that 128 nearly identical websites, created in December 2024, operate as interconnected networks to sell these accounts.
Using private blog networks (PBNs) to manipulate search engine rankings, these sites aim to direct maximum traffic to their illicit marketplaces.
Aged Google Ads accounts are particularly valuable to buyers trying to bypass Google’s robust review mechanisms.
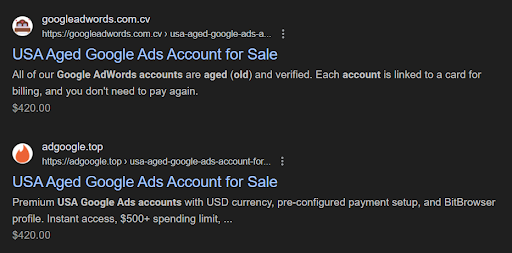
These accounts, perceived as less likely to be flagged for suspicious activity, are often used for unauthorized advertising campaigns or black-hat marketing tactics.
The sale of pre-verified and aged accounts poses a significant cybersecurity threat. These accounts fuel criminal enterprises, from financial fraud to the spread of disinformation, and create complexities for digital platforms striving to ensure user security.
As the underground market for these accounts grows, cybersecurity experts and tech companies face mounting pressure to address this evolving threat.
Enhanced security protocols, detection of account irregularities, and proactive measures against phishing scams may hold the key to combating this alarming trend in cybercrime.
Collect Threat Intelligence with TI Lookup to improve your company’s security - Get 50 Free Request



.png
)
