Hackers reportedly gained unauthorized access to the cutting-edge DeepSeek-V3 model within just 24 hours of its high-profile release.
DeepSeek-V3, a state-of-the-art large language model (LLM) developed by the renowned AI research lab Nexus-AI, was expected to redefine benchmarks in natural language processing.
However, this security breach raises alarming questions about the vulnerabilities of advanced AI systems and the safety protocols relied upon by tech giants.
What Happened?
According to credible sources within Nexus-AI, the attackers—dubbed “LLM Hijackers” by the cybersecurity community—were able to bypass the model’s licensing restrictions and gain full operational control of DeepSeek-V3.
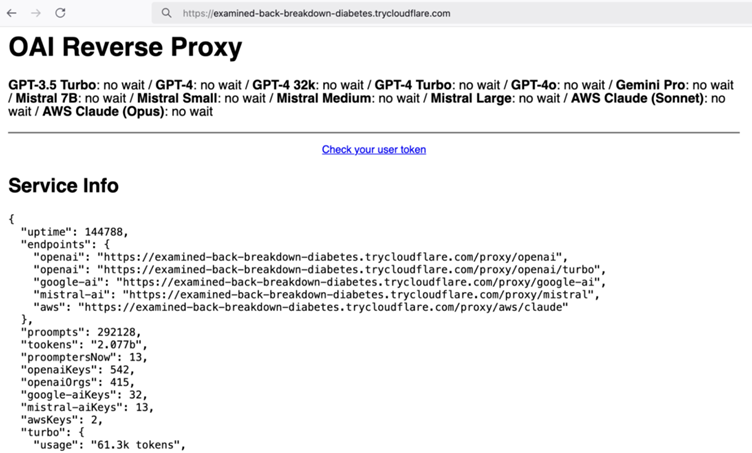
Reports suggest that the hackers exploited a vulnerability in the model’s cloud-based deployment infrastructure, allowing them to download the entire model architecture and weights.
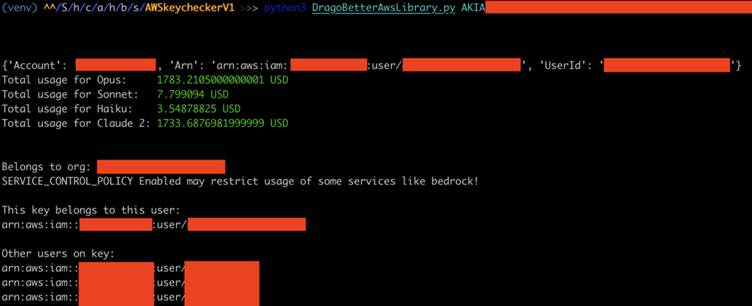
This breach gives unauthorized users access to the proprietary technology, which could be used for malicious purposes such as generating fake content, launching phishing scams, or advancing their own AI development.
Nexus-AI released a public statement acknowledging the breach. “We regret to confirm that a cybersecurity incident has compromised parts of our DeepSeek-V3 architecture.
While our internal team is working around the clock to contain the issue, we also want to assure our users and partners that we are reviewing all aspects of our security protocols to ensure this does not happen again,” said Dr. Emily Carter, the company’s CTO.
The Significance of DeepSeek-V3
DeepSeek-V3 was designed to be a transformative step forward in AI development, boasting features such as real-time reasoning, mathematical computation, and nuanced contextual understanding.
Unlike its predecessors, it was equipped with advanced “self-guard” mechanisms meant to prevent misuse and ensure ethical deployment. The model’s release generated widespread excitement in the tech world, with early adopters hailing its unprecedented capabilities.
However, this breach undermines the public’s confidence in such innovations. The stolen model could potentially end up on the black market or in the hands of malicious actors.
Experts warn that unauthorized access to such powerful technology poses a significant risk to information security and could lead to the proliferation of harmful AI applications.
How Did Hackers Break In?
Preliminary investigations indicate that the breach occurred due to a zero-day vulnerability in Nexus-AI’s cloud hosting platform.
The attackers reportedly utilized sophisticated techniques, including AI-driven exploitation tools, to identify and exploit the weakness just hours after the model went live.
Industry experts are concerned about the possibility that the LLM Hijackers may have been monitoring the release for weeks to strike at an opportune moment.
As per a report by Sysdig, Cybersecurity analyst Marcus Wong said, “This incident underscores the growing sophistication of cybercriminals.
As AI systems become more powerful, so do the tools available to those looking to exploit them. Companies must take proactive measures, including penetration testing and more rigorous encryption protocols.”
The unauthorized access to DeepSeek-V3 has sparked debate within the tech community. Critics argue that companies like Nexus-AI should prioritize more robust security measures before launching such highly anticipated tools.
Meanwhile, others believe the breach highlights the need for global regulatory frameworks around advanced AI technologies.
To combat the crisis, Nexus-AI is reportedly working with cybersecurity firms and government agencies to trace the perpetrators and prevent further misuse of the stolen model.
Additionally, the company has announced that new updates and patches will be released in the coming days to secure DeepSeek-V3’s infrastructure.
While AI represents a monumental leap forward in technological progress, the DeepSeek-V3 incident serves as a stark reminder of the vulnerabilities such advancements entail.
Nexus-AI’s response to this crisis will likely set a precedent for how the industry handles breaches in the future.
For now, the spotlight is on the company to not only recover from the setback but also to reassure stakeholders about the safety and ethical deployment of its flagship model.
Are you from SOC/DFIR Team? - Join 500,000+ Researchers to Analyze Cyber Threats with ANY.RUN Sandbox - Try for Free



