A recent investigation by Kaspersky ICS CERT has uncovered a sophisticated cyberattack targeting industrial organizations across the Asia-Pacific region, particularly those in Taiwan, Malaysia, China, Japan, Thailand, South Korea, Singapore, the Philippines, Vietnam, and Hong Kong.
The attackers are using a highly advanced version of the FatalRAT malware, delivered through a complex multi-stage payload framework designed to evade detection.
Sophisticated Infection Chain
The malware is typically introduced via zip archives disguised as invoices or tax filing applications, distributed through email, WeChat, and Telegram.
These archives contain a first-stage loader packed with tools like UPX, AsProtect, or NSPack to complicate detection and analysis.
Once executed, the loader contacts Youdao Cloud Notes to download a dynamically updated list of links to configurators and second-stage loaders.

According to Kaspersky ICS CERT Report, this approach allows the attackers to frequently change command and control (C2) addresses and payload locations, making it challenging for security systems to track and block the malware.
The configurator module, named Before.dll, collects system information and sends it to the attacker’s server.
It also downloads configuration data from another Youdao note, which contains encrypted settings for the malware’s operation.
The second-stage loader, Fangao.dll, uses this configuration to download and execute the FatalRAT payload.
To maintain persistence, the malware exploits legitimate software like PureCodec and DriverAssistant, employing techniques such as DLL sideloading to hide in legitimate process memory.
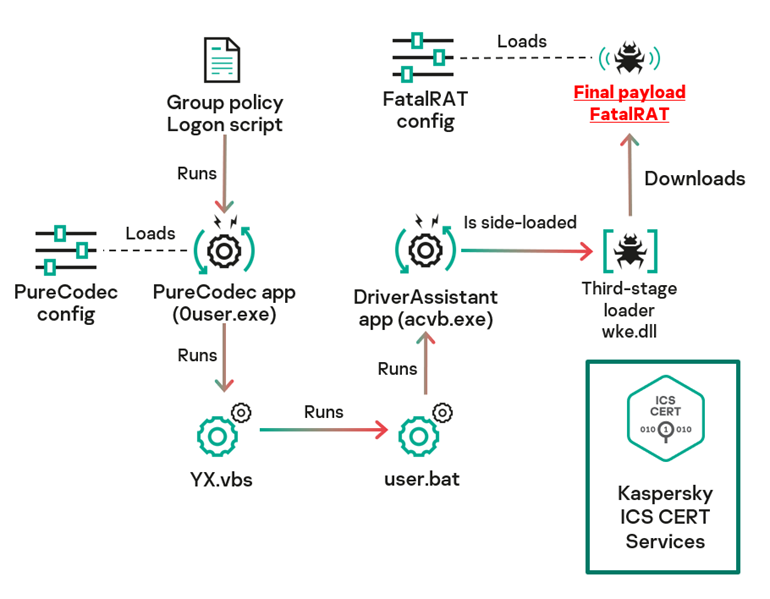
Advanced Malware Capabilities
FatalRAT is equipped with extensive capabilities, including keylogging, system information collection, and the ability to execute commands from its C2 server.
It can manipulate system settings, delete data, and even corrupt the Master Boot Record (MBR).
The malware also checks for indicators of virtual machines or sandbox environments, terminating itself if detected to prevent analysis.
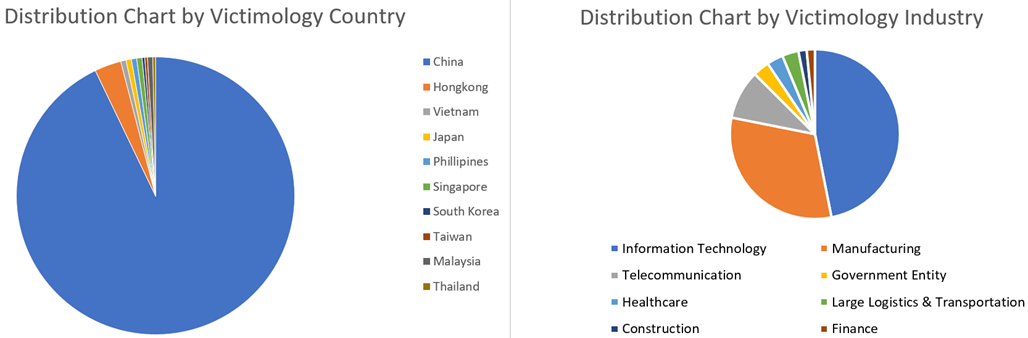
The attackers leverage legitimate cloud services like myqcloud and Youdao Cloud Notes to host their infrastructure, further complicating detection efforts.
While the exact group behind these attacks remains unclear, indicators suggest involvement by a Chinese-speaking threat actor.
The use of Chinese language interfaces, exploitation of regional cloud services, and specific targeting of Chinese-speaking targets support this hypothesis.
To mitigate these threats, organizations are advised to implement robust security measures, including regular software updates, two-factor authentication, and application whitelisting.
Enhancing network segmentation and using advanced threat detection solutions can also help protect against such sophisticated attacks.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here



