Researchers at Graz University of Technology have uncovered a groundbreaking software-based side-channel attack, KernelSnitch, which exploits timing variances in Linux kernel data structures.
Unlike hardware-dependent attacks, KernelSnitch targets hash tables, radix trees, and red-black trees, enabling unprivileged attackers to leak sensitive data across isolated processes, as per a report by a Researcher Published on Github.
The Vulnerability: Kernel Data Structures as Silent Leakers
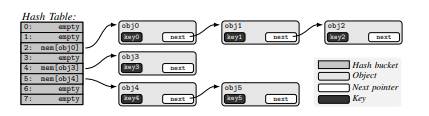
Operating systems rely on dynamic data structures like hash tables and trees to manage metadata for user-space locks, timers, and inter-process communication (IPC).
KernelSnitch exploits a critical architectural oversight: the time required to access these structures depends on their occupancy (number of elements).
By measuring syscall execution times, attackers infer occupancy levels and extract secrets.
How KernelSnitch Works
- Timing Measurement: Attackers trigger syscalls (e.g., futex, msgget) that interact with kernel structures.
- Occupancy Inference: Longer syscall durations indicate higher occupancy due to iterative searches (e.g., traversing linked lists in hash buckets).
- Amplification: Minimal timing differences (as low as 8 CPU cycles) are magnified via cache thrashing (flushing CPU caches to exacerbate memory latency) or structure manipulation (artificially inflating occupancy).
Three Real-World Exploits Demonstrated
1. Covert Channel (580 kbit/s Transmission)
Malicious processes communicate by modulating hash bucket occupancy. On an Intel i7-1260P, KernelSnitch achieved 580 kbit/s with 2.8% error rates using the futex subsystem.
2. Kernel Heap Pointer Leak
By forcing hash collisions, attackers deduce secret kernel addresses (e.g., mm_struct) used in hash functions. This enables precise heap manipulation for privilege escalation, leaking pointers in under 65 seconds.
3. Website Fingerprinting (89% Accuracy)
Monitoring Firefox’s futex activity during webpage loads created unique timing fingerprints. A convolutional neural network (CNN) identified sites from the Ahrefs Top 100 list with 89.5% F1 score.
Why KernelSnitch Matters
- Hardware-Agnostic: Unlike Spectre or Meltdown, KernelSnitch exploits software design flaws, bypassing hardware mitigations.
- Broad Impact: All major OSes using dynamic kernel structures are vulnerable. Tested on Linux 5.15–6.8.
- Stealth: Requires no privileges or shared memory, evading existing sandboxes.
Mitigation Challenges
Fixing KernelSnitch demands fundamental changes:
- Constant-Time Structures: Eliminate occupancy-dependent operations (e.g., precompute worst-case traversal steps).
- Namespace Isolation: Restrict structure sharing across security domains.
- Randomized Hashing: Obfuscate kernel address inputs in hash functions.
As co-author Lukas Maar noted, “Constant-time coding is impractical for general-purpose kernels. We need architectural shifts, not patches.”
KernelSnitch exposes a pervasive blind spot in OS security: performance optimizations that inadvertently create side channels.
With PoC code already public, developers must prioritize structural hardening over incremental fixes.
As kernel-level attacks grow sophisticated, rethinking core design paradigms becomes urgent—before exploitation eclipses mitigation.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here



