A newly disclosed vulnerability in Substack’s custom domain setup could allow malicious actors to hijack inactive subdomains, putting thousands of blogs at risk of serving unauthorized content.
The flaw, discovered by an independent security researcher, exploits misconfigured DNS records to enable domain takeover attacks – a scenario where attackers gain control of web domains through technical loopholes.
While not a direct security flaw in Substack’s infrastructure, the issue highlights risks associated with improper domain management practices.
How Substack’s Custom Domains Work
Substack allows writers to replace default subdomains (e.g., username.substack.com) with custom domains like www.example.com.
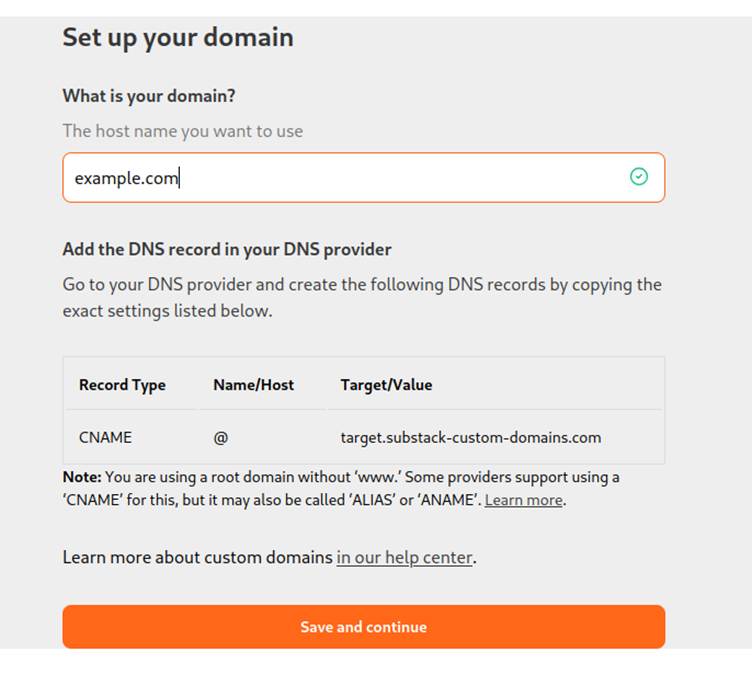
To configure this, users must create a CNAME DNS record pointing their domain to target.substack-custom-domains.com and pay a one-time $50 fee.
Behind the scenes, Substack leverages Cloudflare for SaaS to route traffic from these domains to the appropriate blogs.
However, if a user abandons a Substack blog but neglects to remove the CNAME record, the domain remains pointed to Substack’s infrastructure without active verification.
This creates a critical window where attackers can register the orphaned domain on their own Substack account, pay the fee, and serve malicious content under the victim’s domain.
The Hijacking Mechanism
The attack hinges on Substack’s lack of domain ownership authentication. Unlike services that require TXT record verification or other validation methods, Substack only checks for the presence of the CNAME record.
This means any domain with a valid CNAME – even those no longer linked to active blogs – can be claimed by new users.
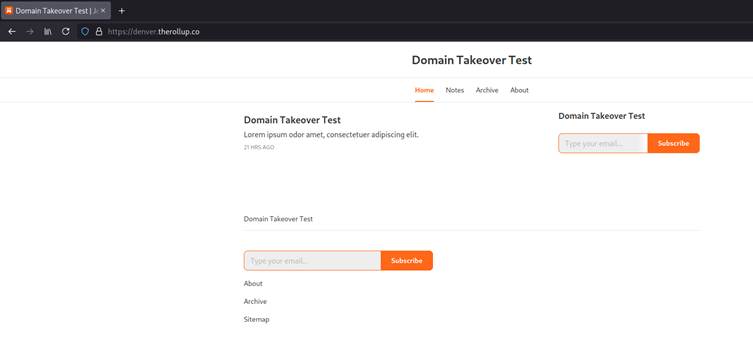
For example, the domain denver.therollup.co had a valid CNAME record pointing to Substack but was not associated with any active blog.
An attacker could add this domain to their Substack account, pay the $50 fee, and host content as if they owned denver.therollup.co.
Compounding the risk, wildcard CNAME records (e.g., *.example.com) expose all subdomains under a parent domain to takeover attempts.
The researcher analyzed 16,925 domains pointing to Substack’s infrastructure via DNS databases like SecurityTrails.
Of these, 1,426 domains (8.4%) were no longer linked to active blogs, leaving them vulnerable to hijacking. Eleven of these were wildcard domains, exponentially increasing potential attack surfaces.
While the $50 fee acts as a deterrent against casual misuse, determined attackers could exploit high-value domains for phishing, disinformation campaigns, or malware distribution.
Notably, hijacked domains would display valid SSL certificates issued by Cloudflare, adding a veneer of legitimacy.
Substack could resolve this issue by implementing Cloudflare for SaaS’s built-in domain authentication, which requires users to prove ownership via TXT records.
This added step would prevent unauthorized claims even if CNAME records remain active. However, the platform has yet to announce changes to its workflow.
For now, users abandoning custom domains must manually remove CNAME records to prevent takeover attempts.
Organizations using wildcard records should transition to explicit subdomain entries where possible.
As one security expert noted, “DNS hygiene is as critical as locking your front door – neglected records are an open invitation to attackers”.
Substack’s reliance on a $50 fee as a security measure underscores the platform’s balancing act between usability and safety.
As content platforms increasingly democratize publishing tools, robust domain validation must become a non-negotiable feature – not an optional safeguard.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
