Users of the Veeam Backup Server have encountered a significant issue following the Windows 11 24H2 update.
Specifically, the update has disrupted the connection between Veeam Recovery Media and the Veeam Backup Server.
This problem affects users who have created recovery media from Windows 11 version 24H2 (build 26100.3194) or higher.
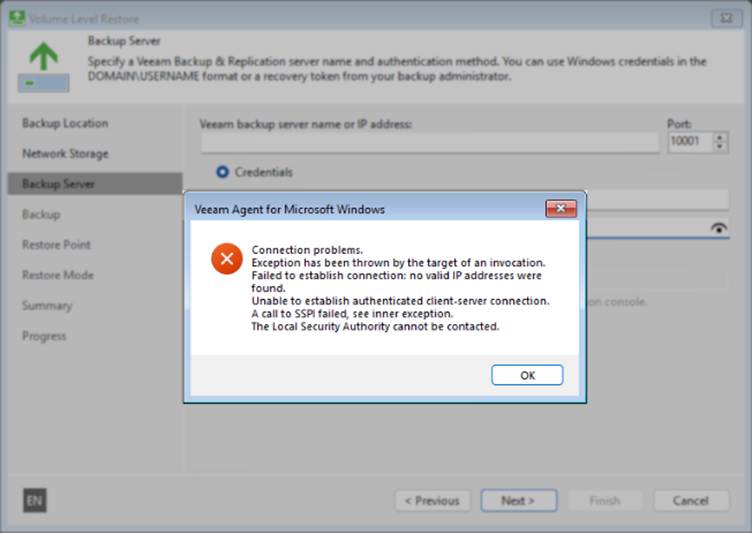
When attempting to restore systems using Veeam Recovery Media created from the latest Windows 11 build, users are met with a series of connection-related errors. These errors include messages such as:
- Connection problems
- The exception has been thrown by the target of an invocation
- Failed to establish connection: no valid IP addresses were found
- Unable to establish authenticated client-server connection
- A call to SSPI failed; see inner exception
- The Local Security Authority cannot be contacted
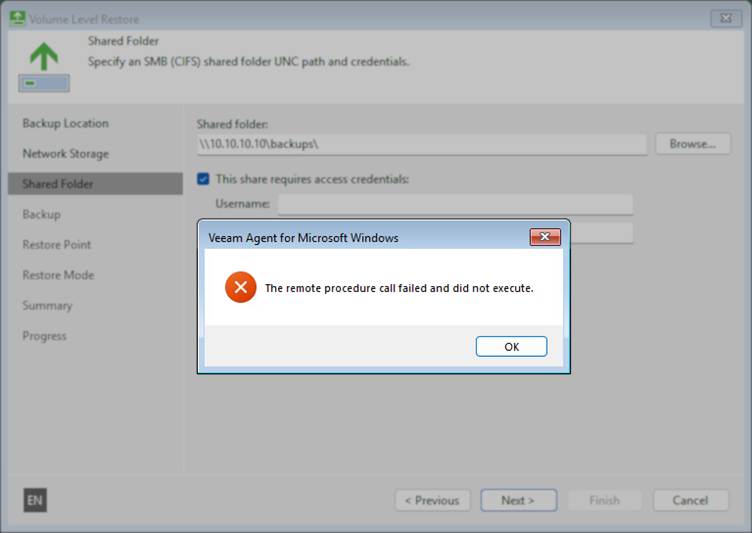
- Error 1: The remote procedure call failed and did not execute
- Error 2
Cause of the Issue
The underlying cause of these connection failures remains unknown at this time. However, it is believed to be associated with a change introduced in the Windows 11 24H2 February update, specifically KB5051987.
Both Veeam and Microsoft are actively investigating this issue to determine the root cause and find a permanent solution.
Until a definitive fix is available, Veeam recommends that affected customers use recovery media generated from older versions of Windows 11, specifically build 26100.3037 or lower.
This workaround should allow users to restore their systems successfully without encountering the connection issues caused by the 24H2 update.
This disruption has significant implications for businesses and individuals relying on Veeam for backup and recovery.
Users are advised to remain vigilant and monitor updates from both Veeam and Microsoft for further guidance on resolving this issue.
It is also crucial for IT professionals to plan by using compatible recovery media until the problem is fully addressed.
While the Windows 11 24H2 update has introduced important features and security enhancements, its impact on Veeam Backup Server connections cannot be overlooked.
Users must be prepared to adapt their recovery strategies temporarily until a comprehensive solution is developed.
Are you from SOC/DFIR Teams? – Analyse Malware, Phishing Incidents & get live Access with ANY.RUN -> Start Now for Free.



