A critical unauthenticated Remote Code Execution (RCE) vulnerability, CVE-2025-22457, has been disclosed by Ivanti, sparking concerns across the cybersecurity industry.
The flaw, which affects several Ivanti products, allows attackers to execute arbitrary code remotely, potentially compromising sensitive enterprise environments.
Researchers, including the Rapid7 vulnerability team, have provided a detailed breakdown of how the flaw was exploited and what steps are needed for remediation.
Vulnerability Overview
The flaw resides in Ivanti Connect Secure, Pulse Connect Secure, Ivanti Policy Secure, and ZTA Gateways due to a stack-based buffer overflow vulnerability in the HTTPS web server.
Ivanti initially classified the issue as a minor bug and silently patched it in February 2025 without a proper security release or advisory. However, a sophisticated China-based threat actor reverse-engineered this patch to build a working exploit.
The vulnerability lies in the HTTPS web server binary /home/bin/web, specifically within the WebRequest::dispatchRequest function.
This function processes HTTP headers, including the X-Forwarded-For header, without proper length checks. An attacker can overflow a fixed 50-character buffer on the stack by supplying a manipulated header value exceeding this size.
char *current_header_value = ctx->header_value_array[header_index];
size_t sz = strspn(current_header_value, "01234567890.");
char buff50[50];
strlcpy(buff50, current_header_value, sz + 1); // Vulnerable code snippetHere, the lack of length validation results in arbitrary stack overwrites, enabling RCE after gaining control over program execution.
Technical Details
- Component Affected: The vulnerability lies in the /home/bin/web binary, specifically in WebRequest::dispatchRequest when processing HTTP headers.
- Exploitation Details: Attackers manipulate the X-Forwarded-For header to overflow the fixed buffer on the stack. However, exploitation is challenging as the overflow is restricted to certain characters (0123456789.).
- Heap Spraying: Attackers use heap spraying techniques to control memory locations that allow arbitrary execution despite the Address Space Layout Randomization (ASLR) security mechanism.
Proof of Concept (PoC)
Within four business days, Rapid7 researchers developed a fully functional exploit that leverages Return-Oriented Programming (ROP) techniques.
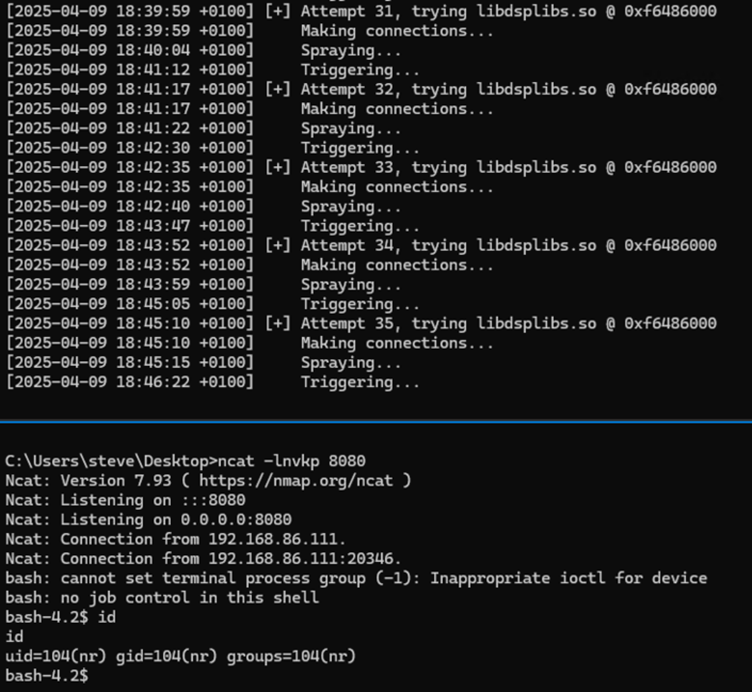
Using gadgets from shared libraries, such as libdsplibs, attackers achieve a stack pivot and eventually execute arbitrary commands. The PoC implementation is public, highlighting the risk to unpatched systems.
Affected Systems
Products impacted by CVE-2025-22457 include:
- Ivanti Connect Secure: Versions prior to 22.7R2.6.
- Pulse Connect Secure: End-of-Life (EoL); customers must migrate to supported versions of Ivanti Connect Secure.
- Ivanti Policy Secure: Versions prior to 22.7R1.4 (scheduled patch on April 21, 2025).
- ZTA Gateways: Versions prior to 22.8R2.2 (scheduled patch on April 19, 2025).
The flaw has already been exploited in the wild, reportedly by state-linked operations. The China-based group performed reconnaissance and exploitation targeting high-value enterprise systems.
Attackers relied on brute-forcing ASLR to execute their payloads, causing frequent web server crashes.
Mitigations and Remediation
Ivanti has provided patches for some affected systems, with remaining updates scheduled later this month. Users are advised to:
- Update Systems Immediately:
- Ivanti Connect Secure: Patch to version 22.7R2.6 released February 11, 2025.
- ZTA Gateways: Patch available April 19, 2025.
- Ivanti Policy Secure: Patch expected April 21, 2025.
- Migrate Legacy Products: Pulse Connect Secure is no longer supported; migrate to Ivanti Connect Secure.
- Implement Network Segmentation: Isolate and monitor Ivanti appliances.
- Audit Logs: Regularly review logs for suspicious behavior such as unexplained crashes.
The delayed disclosure of CVE-2025-22457 has led to criticism over Ivanti’s patching policies.
Experts emphasize the growing danger of state-sponsored actors reverse-engineering “silent patches” and exploiting overlooked vulnerabilities.
Cybersecurity professionals agree this incident reaffirms the importance of timely vulnerability disclosure and robust processes for assessing edge-device risks.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
