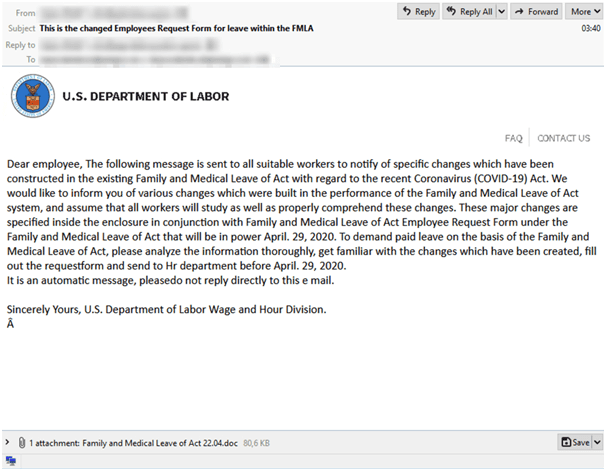
The Cyberthreat uses COVID-19 themed malspam to distribute the Trickbot malware, says IBM Security Researchers. This time attacker utilizes FMLA (Family and Medical Leave Act) to lure the user over COVID-19 medical leaves with the attachment named “Family and Medical Leave of Act 22.04.doc” to distribute the malware. Spam mail disguised to come from the U.S. Department of Labor (DoL).
Trickbot Campaigns
TrickBot is a sophisticated banking Trojan operated by an organized cybercrime gang. Users infected with the TrickBot Trojan becomes part of a botnet that can allow attackers to gain complete control of the device.
Typical consequences of TrickBot infections are bank account takeover, high-value wire fraud, and possibly ransomware attacks targeting organizational networks. Mainly financially motivated cyber-attacks.
DocuSign themes used by Trickbot
Sample email US-DoL.eml, contains three attachments: uslogo.png, faq.png, and Family and Medical Leave of Act 22.04.doc.
As first two attachments were just image files and the third one “Family and Medical Leave of Act 22.04.doc” asks users to enable macros ((ThisDocument.cls), to drops the bat file into the user machine location ”C:\Test\terop.bat”.
Using the cURL utility, the terop.bat file attempts to download an executable from what appears to be a hijacked or compromised domain: hxxps://www.omegasystemsuae[.]com/9hfudnsfl.exe .The file is set to be written to %APPDATA%\Bio_Tecs.exe.
Terop.bat contains TIMEOUT /T 30 and ping 8.8.8.8 commands to evade detection and delay execution.
Overall, the following files are used in the infection chain:
| File Name | File Category | File Hash | Parent |
| US-DoL.eml | f481ba37fdcfaee9fa991e203963bad8 | N/A | |
| Family and Medical Leave of Act 22.04.doc | Carrier File | d341215eb15167870aeff64d5380a69b | US-DoL.eml |
| terop.bat | Downloader | 9f52f07856cdf2b076c27ae60cb0d100 | Family and Medical Leave of Act 22.04.doc |
| faq.png | Benign | eb77c6a9fc86bd73d77b92c24ca889db | US-DoL.eml |
| us-logo.png | Benign | 1af19e6717acf7f38b8f1a651c738954 | US-DoL.eml |
Infection chain – Trickbot This has been observed that the “Macro on Close” function used in the Docusign theme became a tactic for Trickbot distributors.
Other Trickbot Campaigns
New TrickBot Module BruteForce RDP Connections Attacks Telecommunication Industry
Hackers Abusing Window 10 Remote Desktop ActiveX control to Install New Version of Trickbot Malware
TrickBot Credential Stealer Malware Abuses Google Suite to Hide Malicious Activity



.png
)
