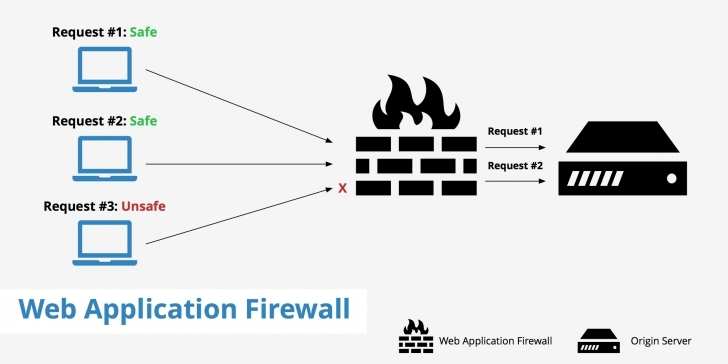
A web application firewall is a firewall that monitors, filters and blocks statistics packets as they journey to and from an internet site or net software.
AWAF can be either network-based, host-based totally or cloud-based totally and is frequently deployed thru a reverse proxy and located in front of 1 or greater websites or applications.
Jogging as a network appliance, server plugin or cloud provider, the WAF inspects each packet and makes use of a rule base to investigate layer 7 net utility good judgment and clear out doubtlessly harmful visitors that could facilitate net exploits.
A WAF analyzes hypertext transfer protocol (http) requests and applies a set of regulations that outline what parts of that communiqué are benign and what elements are malicious.
The main components of http conversations that a WAF analyzes are getting and publish requests.
Web systems towards zero-day exploits,Web application firewalls are a common security control utilized by organizations to defend malware infections, impersonation, and different known and unknown threats and vulnerabilities.
Via customized inspections, a WAF is able to locate and right now prevent several of the maximum dangerous net utility security flaws so learn more about WAF and its types, which traditional network firewalls and other intrusion detection structures and intrusion prevention structures won’t be capable of doing.
WAF are specifically useful to corporations that offer services or products over the internet which include e-commerce shopping, on-line banking and different interactions between customers or commercial enterprise companions.
Types of WAF
Host-based WAFs
Host-based WAF Can is completely included into the application code itself. The blessings of a number-based totally WAF implementation include decrease value and expanded customization options.
Host-based totally WAFs may be a mission to control because they require application libraries and rely upon nearby server resources to run successfully.
Therefore, greater workforce resources, consisting of that of developers, device analysts, and DevOps/develops, can be required.
Network-based WAFs
Network-based WAF is normally hardware-based and may reduce latency due to the fact they may be installed locally on-premises via committed equipment, as near the utility as feasible.
Most important community-based WAF companies permit replication of regulations and settings across a couple of home equipment, thereby making large-scale deployment, configuration and management feasible.
The most important disadvantage for this form of WAF product is value there’s an in advance capital expenditure, in addition to ongoing operational prices for upkeep.
Advantages
A WAF has a bonus over traditional firewalls because it offers more visibility into touchy software data that is communicated the use of the http software layer.
It may save you utility layer assaults that commonly bypass conventional network firewalls.
Other advantage of a WAF is that it may shield web-primarily based applications without necessarily getting access to the supply code of the application.
At the same time as a number-primarily based WAF may be included into software code, a cloud-hosted WAF is able to defending the application while not having access.
In addition, a cloud WAF is easy to set up and manipulate and gives quick virtual patching solutions that permit customers to rapidly customize their settings to adapt to newly detected threats.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.


.png
)
