A new cybersecurity threat targeting Facebook advertisers in Vietnam, known as VietCredCare, has emerged.
This information stealer has been active since at least August 2022 and is designed to hijack corporate Facebook accounts by automatically filtering out Facebook session cookies and credentials from compromised devices.
The malware assesses whether the stolen accounts manage business profiles and if they maintain a positive Meta ad credit balance.
How do Hackers Bypass 2FA?
Live attack simulation Webinar demonstrates various ways in which account takeover can happen and practices to protect your websites and APIs against ATO attacks.
How VietCredCare Operates
VietCredCare is distributed through links to bogus sites on social media posts and instant messaging platforms, masquerading as legitimate software like Microsoft Office or Acrobat Reader.
Once installed, it can extract credentials, cookies, and session IDs from web browsers, including Google Chrome, Microsoft Edge, and Cốc Cốc, a browser focusing on the Vietnamese market, Group-IB said.

The malware is notable for its ability to retrieve a victim’s IP address, check if a Facebook account is a business profile, and assess whether the account currently manages ads.
It also takes steps to evade detection by disabling the Windows Antimalware Scan Interface (AMSI) and adding itself to the Windows Defender Antivirus exclusion list.
VietCredCare’s core functionality to filter out Facebook credentials puts organizations at risk of reputational and financial damages if their sensitive accounts are compromised, reads the report.
Credentials belonging to several government agencies, universities, e-commerce platforms, banks, and Vietnamese companies have been siphoned via the stealer malware.
The threat actors then use the stolen Facebook accounts to post political content or propagate phishing and affiliate scams for financial gain.
This large-scale malware distribution scheme facilitates the takeover of corporate Facebook accounts, targeting Vietnamese individuals who manage the Facebook profiles of prominent businesses and organizations.
Stealer-as-a-Service Model
VietCredCare is offered to other aspiring cybercriminals under the stealer-as-a-service model and is advertised on Facebook, YouTube, and Telegram.
It is managed by Vietnamese-speaking individuals.
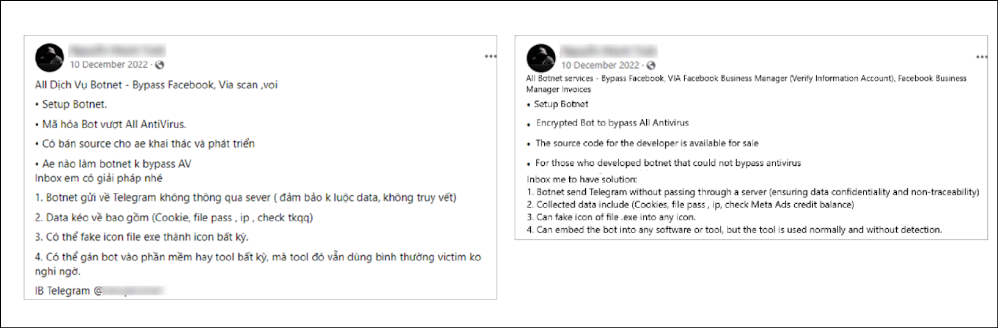
Customers can purchase access to a botnet managed by the malware’s developers or procure access to the source code for resale or personal use.
They are also provided a bespoke Telegram bot to control the exfiltration and delivery of credentials from an infected device.
Protecting Against VietCredCare
Organizations and individuals must be vigilant and take preventive measures against malware-based attacks.
This includes regular software updates, the use of antivirus software, and strong passwords.
It is also crucial to be cautious when clicking links or downloading attachments from unknown sources, as these could potentially contain malware like VietCredCare.
In conclusion, VietCredCare is a sophisticated malware that significantly threatens businesses and their online presence.
The ability of this malware to target and steal credentials from business-related Facebook accounts underscores the need for enhanced cybersecurity measures and awareness among users and organizations alike.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.



.png
)
