Cybersecurity experts at Seqrite Labs have reported a surge in cyberattacks against Indian government entities.
These attacks have been attributed to Pakistani Advanced Persistent Threat (APT) groups, which have been intensifying their malicious activities.
Attack Methods
The recent campaigns uncovered by Seqrite Labs’ APT team reveal a sophisticated level of cyber warfare.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
The Pakistani-linked APT group SideCopy has been particularly active, deploying its commonly used AllaKore Remote Access Trojan (RAT) in three separate campaigns.
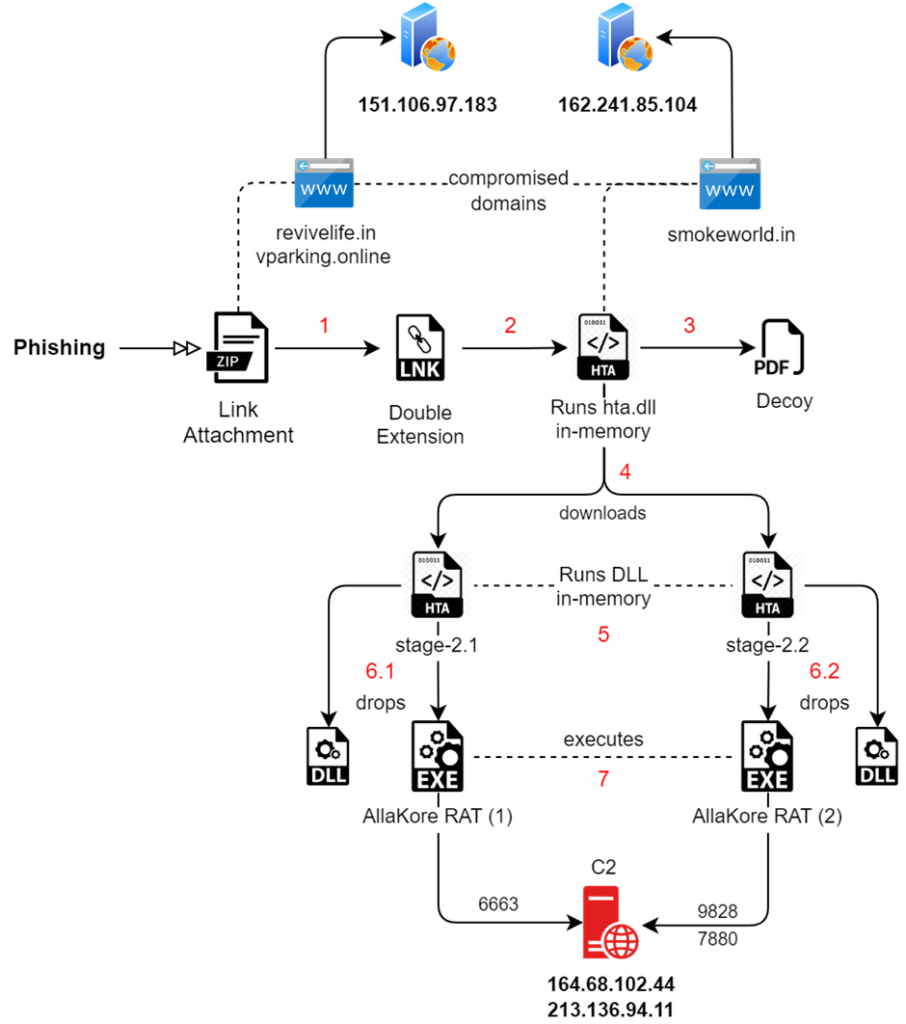
In each of these campaigns, two instances of the RAT were used simultaneously, showcasing the group’s aggressive tactics.
Simultaneously, Transparent Tribe (APT36), the parent group of SideCopy, has been consistently utilizing the Crimson RAT.
However, they have modified their approach by encoding or packing the RAT differently to evade detection.
Targets
The primary targets of these cyberattacks are Indian defense and government entities.
SideCopy and APT36 have been persistent in their efforts to infiltrate these sectors since at least 2019.
The decoy files used in previous campaigns in February-March 2023 have been observed.
“Grant_of_Risk_and_HardShip_Allowances_Mar_24.pdf.” As the name suggests, it is an advisory from 2022 on allowance grants to Army officers under India’s Ministry of Defence.

Their arsenal is not limited to AllaKore and Crimson RATs but includes other malicious tools such as Ares RAT, Action RAT, Reverse RAT, and Margulas RAT.
The impact of these cyberattacks is significant, as they compromise the security and integrity of critical government systems.
The persistent targeting of these entities threatens national security and puts sensitive data at risk of being exploited.
Countermeasures
In response to these escalating threats, Indian cybersecurity forces are urged to strengthen their defenses and remain vigilant.
This includes updating security protocols, conducting regular system checks, and training personnel to effectively recognize and respond to cyber threats.
As geopolitical tensions continue influencing the cyber threat landscape, India remains a prime target for APT groups.
Seqrite Labs’ recent findings underscore the need for robust cybersecurity measures to protect against these sophisticated and persistent threats.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training -> Try Free Demo
.webp?w=696&resize=696,0&ssl=1)


.png
)
