A new Android malware called ‘Autolycos’ installed over 3 million times is surfing on the Google Play Store by secretly subscribing users to its premium services.
Maxime Ingrao, Security Researcher from Evina found the new android malware ‘Autolycos’, which is available on the Google Play store at present.
There are two applications that are still available on the google play store including ‘Funny Camera’ by KellyTech, which has over 500,000 installations, and ‘Razer Keyboard & Theme’ by rxcheldiolola, counts over 50,000 installs on the Play Store.
As updated on 13th July, Google removed the two applications also from the Google Play Store.
Six Applications Removed From the Google Play Store
- Vlog Star Video Editor (com.vlog.star.video.editor) – 1 million downloads
- Creative 3D Launcher (app.launcher.creative3d) – 1 million downloads
- Wow Beauty Camera (com.wowbeauty.camera) – 100,000 downloads
- Gif Emoji Keyboard (com.gif.emoji.keyboard) – 100,000 downloads
- Freeglow Camera 1.0.0 (com.glow.camera.open) – 5,000 downloads
- Coco Camera v1.1 (com.toomore.cool.camera) –1,000 downloads
Experts warn that “Those who still have them installed risk being charged with costly subscriptions by the malware’s activities”. Users are asked to remove them from their endpoints using antivirus software or other malware-removing solutions.
The Working of Autolycos Malware
This new malware ‘Autolycos’ execute URLs on the remote browser including the result in HTTP requests instead of using Android Webview. Experts say this nature makes its activities unnoticed. Therefore it is not detected by users of compromised devices.
The malware group has promoted its apps to hack new users with several social media campaigns. The group also created various bot reviews which look legitimate to new users or users who are unaware of Autolycos’s activity.
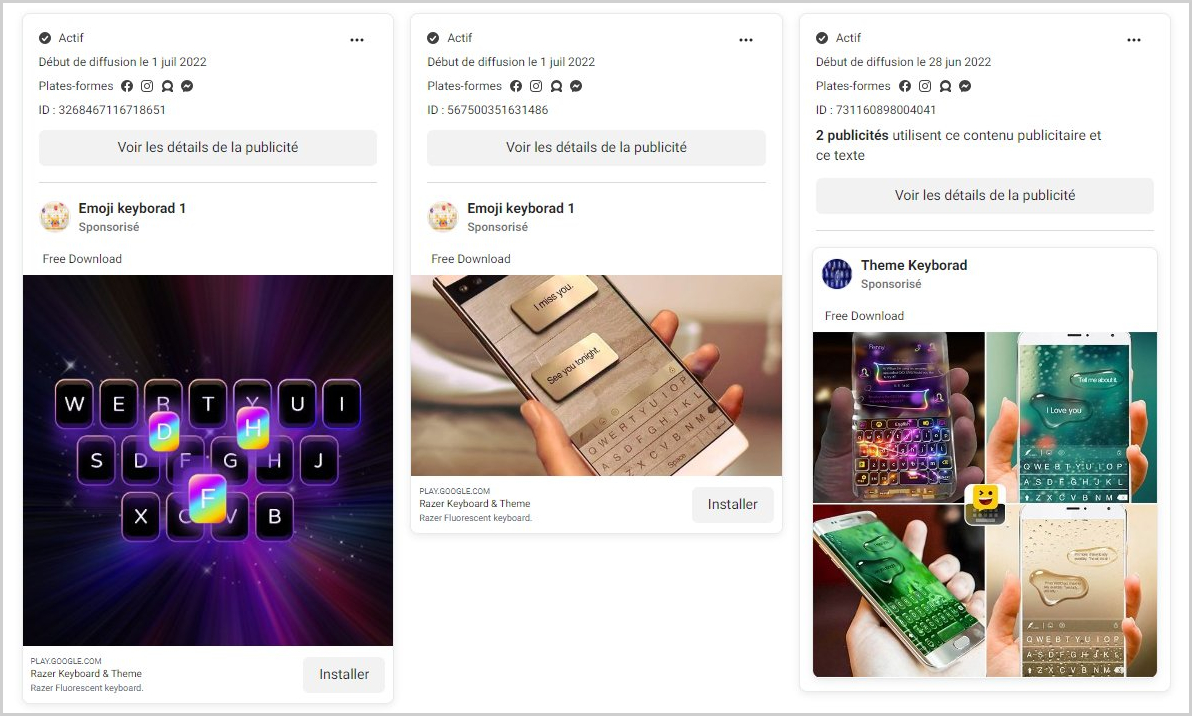
Campaigns on Facebook (@IngraoMaxime)
Generally, the malicious applications requested permission to read SMS content upon installation on the device, allowing the apps to access a victim’s SMS text messages.
Therefore, experts advise the users to download software from verified sources however the App Store and the Play Store are not protected to assaults.
Android users should observe background internet data and battery consumption, keep Play Protect active, and try to reduce the number of apps they install on their smartphones.
Users should persistently be cautious with their devices, keeping them up to date, installing an antivirus solution, and using firewalls to monitor incoming and outgoing data.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.



.png
)
