Phone scams are becoming more sophisticated with advancements in AI-driven speech tools, making it easier for scammers to manipulate victims.
To combat these growing threats, Google has introduced a groundbreaking security feature in Android 16 that prevents users from making certain sensitive settings changes during phone calls, as per a report by Android Authority.
This could serve as a game-changer in reducing the success rate of phone-based scams.
This feature, already live in Android 16 Beta 2, aims to stop scammers from tricking victims into enabling permissions like sideloading apps or granting accessibility access—actions that could compromise device security.
A video demonstration of this feature in action has showcased its potential to thwart scams.
How Phone Scams Exploit Users
Phone scammers often employ psychological tactics to convince victims to install malware or disclose sensitive information.
A common tactic involves guiding victims through the process of sideloading apps, as most users are unfamiliar with how to enable this setting on their own.
Scammers typically pose as someone offering help and staying on the line to manipulate the victim into granting dangerous permissions.
Once malware is granted access to tools like accessibility permissions, it can read the screen, perform actions on behalf of the user, and even take control of the device.
These permissions are the cornerstone of many scams, making Android’s new safeguards a critical step toward user protection.
How Android 16’s New Feature Works
The new security update leverages call detection to block the enabling of specific permissions while a phone call is active. For example:
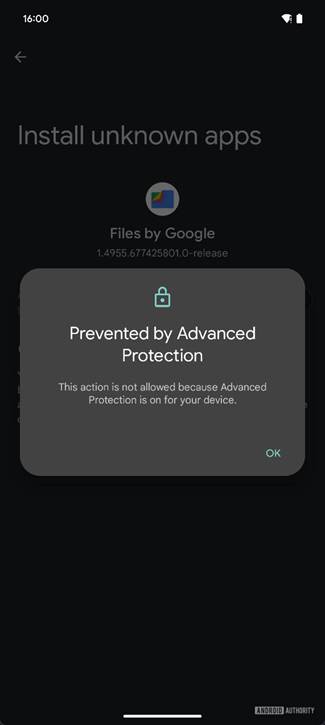
- Blocking Sideloading Permissions:
- Android 16 prevents users from enabling the sideloading permission (found under Settings > Apps > Special app access > Install unknown apps) during an ongoing call.
- Sideloading is disabled by default for security reasons, as it is a gateway for malware distribution outside of official app stores.
- Enhanced Warnings:
- A dialog box now appears if a user attempts to toggle sideloading permissions during a call, warning that scammers often target victims with this request and advising caution.
- This warning introduces an extra step, potentially making users more aware of the caller’s intentions and disrupting the scammer’s flow.
- Blocking Sensitive Permissions:
- Android 16 also prevents the activation of sensitive permissions, like accessibility access, during calls. This restriction adds layer of defense against malware gaining control over a user’s device.
While determined scammers may still instruct victims to hang up and re-enable these settings, the added friction created by Android 16’s protections could be enough to make users suspicious.
The prominently displayed warnings about scams can also prompt users to reconsider their actions.
These features build on the foundations of Enhanced Confirmation Mode, introduced in Android 15, which required extra steps for sideloaded apps to gain access to sensitive permissions.
Together, these innovations demonstrate Google’s commitment to enhancing Android’s security and protecting users from evolving scam tactics.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
