Cybersecurity enthusiasts and IT administrators worldwide are voicing concerns over a newly discovered vulnerability in AnyDesk that could lead to local privilege escalation (LPE).
The vulnerability, identified as CVE-2024-12754 and coordinated by Trend Micro’s Zero Day Initiative, allows attackers to weaponize Windows background images for escalating permissions on Windows systems.
A Closer Look at the Vulnerability
Discovered by security researcher Naor Hodorov, the flaw lies in the way the AnyDesk service handles background images during remote sessions.
Specifically, when a session is initiated, AnyDesk copies the user’s background image into the C:\Windows\Temp directory using NT AUTHORITY\SYSTEM privileges.
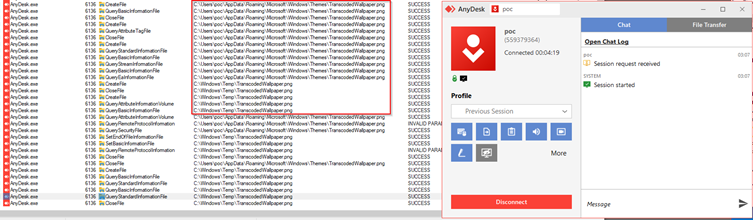
Here’s the twist: A low-privileged user can manipulate this file-copy operation to gain access to otherwise restricted files and, ultimately, escalate their privileges.
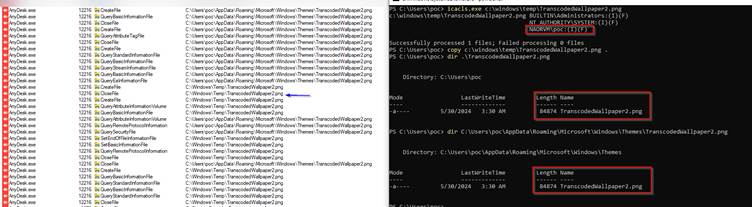
By carefully pre-creating a target file in C:\Windows\Temp and exploiting file ownership inheritance behaviors, the attacker can execute an arbitrary file read or copy operation.
Exploiting the Vulnerability
To exploit this vulnerability for privilege escalation, the attacker follows these steps:
- Pre-Creation of Target Files: The attacker pre-creates a file in C:\Windows\Temp matching the name of the background image.
- Triggering AnyDesk’s File Copy Mechanism: They set their desktop background image to the desired file and establish a connection to their own AnyDesk ID. This triggers the file to be copied as NT AUTHORITY\SYSTEM.
- Manipulating File Ownership: Using directory reparse points and symbolic links, they redirect AnyDesk’s copy operation to sensitive system files, such as the SAM, SYSTEM, and SECURITY files stored in Volume Shadow Copies (used for Restore Points).
- Extracting Credentials: By reading these files, the attacker gains access to hashes and credentials of local administrators and cached users, effectively gaining administrative rights on the system.
What makes this vulnerability dangerous is its potential simplicity. AnyDesk, a popular remote administration tool used by millions worldwide, is installed on enterprise and personal devices alike.
While the complexity of the attack chain may deter casual attackers, skilled adversaries could weaponize this for more sophisticated breaches.
The vulnerability was responsibly disclosed to AnyDesk Software GmbH on July 24, 2024, with public disclosure coordinated for December 19, 2024.
The credit for this discovery goes to Naor Hodorov, whose findings were facilitated by Trend Micro’s Zero Day Initiative.
Until a patch is released, users and administrators are urged to:
- Restrict access to AnyDesk installations, particularly on high-value systems.
- Regularly monitor and secure the C:\Windows\Temp directory.
- Disable Volume Shadow Copies if not in use.
As organizations increasingly rely on remote access tools, this vulnerability serves as a stark reminder of the importance of regular security audits and timely patching.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
