A recent analysis by Rhino Security Labs has uncovered a series of critical vulnerabilities in the Appsmith developer tool, a platform used for building internal applications such as dashboards and customer support tools.
The most severe of these vulnerabilities is CVE-2024-55963, which enables unauthenticated remote code execution due to a misconfigured PostgreSQL database that ships with the product.
Appsmith, an open-source developer tool, is popular for its ability to connect various data sources to user interfaces, including databases and Large Language Models (LLMs).
However, the default installation includes a misconfigured PostgreSQL database.
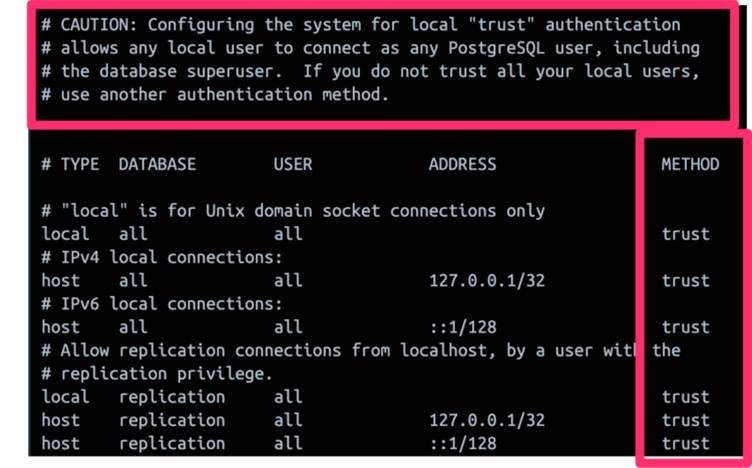
Specifically, the PostgreSQL authentication file (pg_hba.conf) is set to allow any local user to connect as any PostgreSQL user without a password, which can be exploited for remote code execution.
The exploitation path leverages Appsmith’s default configuration that allows user signup. An attacker can sign up for the application, create a new workspace and application, and connect to the vulnerable PostgreSQL database.
From there, they can execute SQL queries that enable system command execution, posing a significant risk to any organization relying on Appsmith.
Proof of Concept Explained
A proof-of-concept exploit demonstrates how attackers can abuse this vulnerability. It involves creating a table, copying data from a program into the table (e.g., cat /etc/passwd), selecting data from the table, and then dropping the table to clean up tracks.
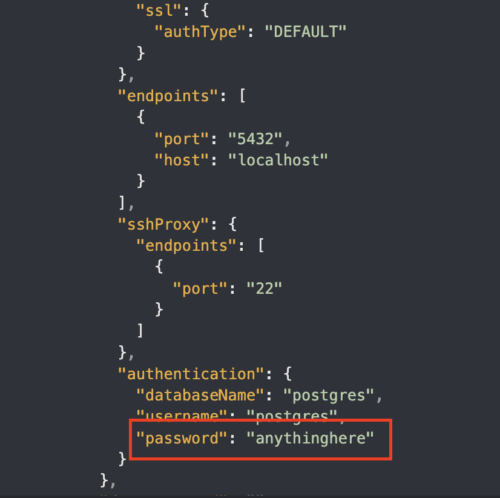
This exploitability is facilitated by the application server connecting to the database directly, allowing attackers to bypass client-side security checks.
CREATE TABLE PoC (column1 TEXT);
COPY PoC FROM PROGRAM 'cat /etc/passwd';
SELECT * FROM PoC;
DROP PoC; -- Cleans up the database after the exploitAdditional Vulnerabilities
Beyond CVE-2024-55963, two other vulnerabilities have been identified:
CVE-2024-55964: Insecure Direct Object Reference (IDOR) Allowing Unauthorized SQL Access
This vulnerability affects users with the “App Viewer” role, who are only supposed to have view-only permissions.
However, through API manipulation, attackers can identify and access database connections, allowing them to execute arbitrary SQL queries against databases within accessible workspaces.
The exploit relies on brute-forcing predictable parts of the datasource IDs and using specific API endpoints designed for SQL databases.
Though this vulnerability is mitigated by workspace-level authorization, it still poses a risk for sensitive data exposure.
CVE-2024-55965: Denial of Service via Broken Access Control
This vulnerability involves a flawed permission check that allows “App Viewer” users to restart the application server, triggering a denial-of-service attack.
Exploited by leveraging persistent session cookies, attackers can automate repeated restart requests, temporarily disabling access to the application.
The flaw lies in the Global Exception Handler, which improperly bypasses permission checks for certain requests, including the restart function. This leads to unauthorized access to administrative-level operations.
Impact and Mitigation
These vulnerabilities impact Appsmith versions 1.20 through 1.51 across their product lineup. To mitigate these risks, organizations are advised to update their Appsmith installations to versions that include patches for these vulnerabilities.
Rhino Security Labs has provided detailed exploit scripts and detection tools to help security teams identify and protect against these vulnerabilities.
The scripts and tools are available in their CVE Github repository, offering proactive measures to safeguard against potential attacks.
The revelations of these critical vulnerabilities highlight the importance of rigorous security testing and configuration audits in software development tools.
Organizations utilizing Appsmith should prioritize updating their installations and reviewing their current setups to prevent unauthorized access and potential remote code execution.
By acting promptly, companies can protect their systems and data from these vulnerabilities, ensuring the continued use of Appsmith’s beneficial functionalities while minimizing risk exposure.
Are you from SOC/DFIR Teams? – Analyse Malware, Phishing Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
